File list
This special page shows all uploaded files.
| Date | Name | Thumbnail | Size | User | Description | Versions |
|---|---|---|---|---|---|---|
| 20:38, 21 May 2020 | Mobile Security Concerns.png (file) |  |
23 KB | User | Mobile Security Concerns | 1 |
| 15:17, 20 May 2020 | ISMS.png (file) | 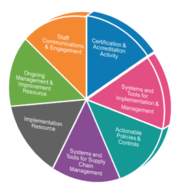 |
186 KB | User | Elements of an ISMS | 1 |
| 14:25, 20 May 2020 | Security Triad.png (file) | 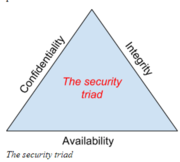 |
61 KB | User | Security Triad | 1 |
| 18:26, 19 May 2020 | MTTR Formula.png (file) | 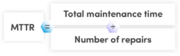 |
55 KB | User | MTTR Formula | 1 |
| 16:10, 19 May 2020 | FCAPS Model.png (file) |  |
710 KB | User | FCAPS Model | 1 |
| 02:47, 19 May 2020 | Computer Security Threats.jpg (file) | 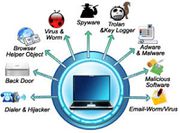 |
84 KB | User | Computer Security Threats | 1 |
| 01:52, 19 May 2020 | Data Security Vs Data Privacy.png (file) |  |
185 KB | User | Data Security Vs. Data Privacy | 1 |
| 19:11, 18 May 2020 | PCI DSS Compliance Levels.png (file) |  |
6 KB | User | PCI DSS compliance levels | 1 |
| 17:57, 18 May 2020 | FISMA Requirements.png (file) |  |
359 KB | User | FISMA Requirements | 1 |
| 17:39, 18 May 2020 | Cognitive Security.png (file) |  |
359 KB | User | Cognitive Security | 1 |
| 14:13, 18 May 2020 | CDSA Layers.png (file) |  |
156 KB | User | CDSA Layers | 1 |
| 16:16, 16 May 2020 | IT Control Frameworks.png (file) |  |
430 KB | User | IT Control Frameworks | 1 |
| 18:01, 15 May 2020 | IT Controls.png (file) | 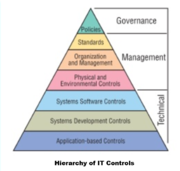 |
288 KB | User | Hierarchy of IT Controls | 1 |
| 19:48, 14 May 2020 | ICT Components.jpg (file) |  |
67 KB | User | ICT Components | 1 |
| 19:23, 14 May 2020 | ICT.png (file) |  |
48 KB | User | Information and Communications Technology (ICT) | 1 |
| 15:45, 13 May 2020 | Innovation Value Chain.png (file) | 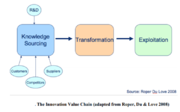 |
104 KB | User | Innovation Value Chain | 1 |
| 20:39, 29 April 2020 | SWOT Analysis.png (file) |  |
144 KB | User | SWOT Analysis | 1 |
| 21:51, 20 April 2020 | SD-WAN Architecture.png (file) | 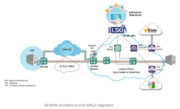 |
399 KB | User | SD-WAN Architecture | 1 |
| 20:15, 17 April 2020 | Software Design.png (file) | 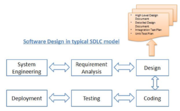 |
380 KB | User | Software Design | 1 |
| 19:27, 17 April 2020 | OPM.jpg (file) |  |
89 KB | User | Organizational Project Management | 1 |
| 17:46, 17 April 2020 | Software Categories.png (file) | 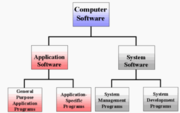 |
91 KB | User | Software Categories | 1 |
| 16:53, 17 April 2020 | Market Cap Segments.png (file) | 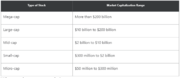 |
84 KB | User | Market Cap Segments | 1 |
| 21:09, 15 April 2020 | Logistics.png (file) | 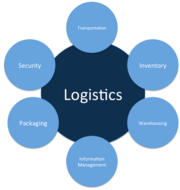 |
54 KB | User | Logistics | 1 |
| 19:11, 15 April 2020 | Logistics Management Importance.jpeg (file) | 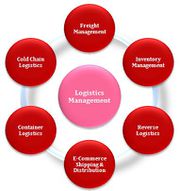 |
34 KB | User | Importance of Logistics Management | 1 |
| 15:26, 11 April 2020 | Business Case Steps.png (file) |  |
372 KB | User | Steps to developing a business case | 1 |
| 19:40, 1 April 2020 | RACI Matrix.jpg (file) |  |
152 KB | User | RACI Matrix Template | 1 |
| 06:46, 24 March 2020 | FCM Model.gif (file) |  |
16 KB | User | FCM (Factor-Criteria-Metrics) Model | 1 |
| 04:03, 21 March 2020 | RBT Process.jpg (file) | 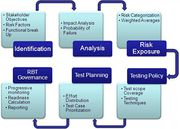 |
112 KB | User | Risk Based Testing (RBT) Process | 1 |
| 18:38, 20 March 2020 | TARA Process.png (file) | 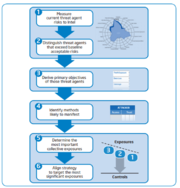 |
218 KB | User | TARA Process | 1 |
| 16:25, 20 March 2020 | Threat Agent Risk Assessment.png (file) | 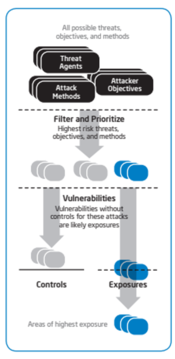 |
104 KB | User | Threat Agent Risk Assessment (TARA) | 1 |
| 19:45, 19 March 2020 | Bowtie Diagram.png (file) | 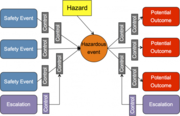 |
117 KB | User | Bowtie Diagram | 1 |
| 19:38, 19 March 2020 | Risk Assessment vs BIA.jpg (file) |  |
64 KB | User | Risk Assessment vs BIA | 1 |
| 19:35, 19 March 2020 | BIA Risk Assessment Difference.png (file) | 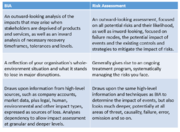 |
413 KB | User | The Difference Between Risk Assessment and BIA | 1 |
| 18:50, 19 March 2020 | Risk Assessment Methods.png (file) |  |
199 KB | User | Advantages and Disadvantages of Risk Assessment Methods | 1 |
| 18:02, 19 March 2020 | Hierarchy of controls.jpg (file) | 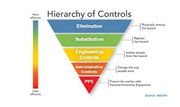 |
11 KB | User | Hierarchy of controls | 1 |
| 17:05, 18 March 2020 | Risk Matrix.png (file) | 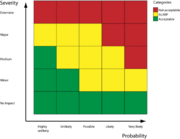 |
74 KB | User | Risk Matrix | 1 |
| 18:45, 5 March 2020 | Operational Risk Events.png (file) | 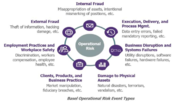 |
611 KB | User | Operational Risk Events | 1 |
| 19:48, 4 March 2020 | Avoid Confirmation Bias.png (file) | 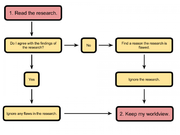 |
88 KB | User | How to Avoid Confirmation Bias | 1 |
| 19:59, 27 February 2020 | DMAIC Process.png (file) |  |
165 KB | User | DMAIC Process | 1 |
| 17:46, 27 February 2020 | Six Sigma Concept.png (file) |  |
210 KB | User | Six Sigma Concept | 1 |
| 16:30, 27 February 2020 | Six Sigma.jpg (file) | 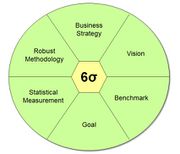 |
30 KB | User | Six Sigma | 1 |
| 15:53, 27 February 2020 | Takt Time Optimized Balanced Line.jpg (file) | 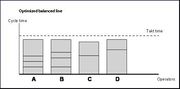 |
9 KB | User | Takt Time Optimized Balanced Line | 1 |
| 15:53, 27 February 2020 | Takt Time Balanced Line.jpg (file) |  |
8 KB | User | Takt Time Balanced Line | 1 |
| 15:52, 27 February 2020 | Takt Time Initial Stage.jpg (file) |  |
9 KB | User | Takt Time Initial Stage | 1 |
| 15:34, 27 February 2020 | Takt Time Approach.png (file) | 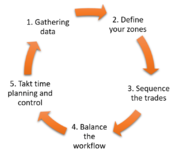 |
34 KB | User | Five Step Approach to Developing TAKT Time | 1 |
| 18:13, 26 February 2020 | Strategic Agility Subconstructs.png (file) |  |
1.09 MB | User | Strategic Agility Subconstructs | 1 |
| 18:11, 26 February 2020 | Strategic Agility Dimensions.png (file) | 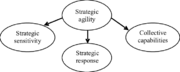 |
13 KB | User | Strategic Agility Dimensions | 1 |
| 17:54, 26 February 2020 | Strategic Agility.jpg (file) | 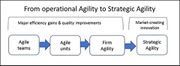 |
51 KB | User | From Operational Agility to Strategic Agility | 1 |
| 21:29, 25 February 2020 | IT Strategic Plan Model.png (file) | 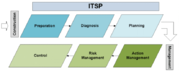 |
35 KB | User | IT Strategic Plan Model | 1 |
| 18:56, 25 February 2020 | IT-Strategic-Plan-Map.png (file) | 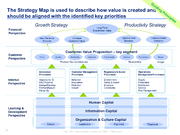 |
147 KB | User | IT Strategy Map | 1 |
