Adaptive Security Architecture (ASA)
Adaptive Security Architecture describes an approach that uses a combination of integrated tactics to help businesses stay ahead of cybercriminals, instigating flexible security measures to protect data and systems in as agile a way as possible, rather than relying on outdated perimeter defense strategies.[1]
The Adaptive Security Architecture is the enterprise security immune system. Adaptive Security Architecture (ASA) is based on solutions that use adaptive and dynamic operational styles to maintain the integrity of data, systems, and their survivability. To extend the parallel between biological ecosystems and enterprise IT infrastructures, ASA follows the Darwinian concept of ‘adapt or die’. Successful IT infrastructures must adapt or they will eventually fall to predator attacks, viral infections, or the inability to adjust to environmental changes. ASA behaves similarly to how an organism defends against a localized disease outbreak or even a pandemic. Using an adaptive approach, ASA is an autonomic system that effectively mimics both an organic immune system and a large-scale natural ecosystem. To this end, the key objective of an Adaptive Security Architecture (ASA) is to be able to detect, contain and respond to cyber threats before they cause damage by: • Continuously monitoring the “entire IT stack” • Shifting from “incident response” to “continuous response” • Moving to a “unified” or “integrated” detection, response, prediction & protection capability • Preventing “successful attacks” • Reducing the surface and velocity of attacks • Reducing the Mean-Time-To-Detect Threats (MTTD) and the Mean-Time-To-Respond to Threats (MTTR) • Implementing continuous response-enabled operations (SOC) Moreover, the ASA has to provide the ability to take remedial actions such as: • The quarantine of resources for forensic purposes so that the ecosystem can learn from the breach • The provisioning of other resources to replace affected systems, enabling service continuity • The application of corrective measures as needed[2]
Components of an Adaptive Security Architecture[3]
The adaptive security architecture that Gartner refers to provides continuous, pervasive monitoring and visibility.
- "To enable a truly adaptive and risk-based response to advanced threats, the core of a next-generation security protection process will be continuous, pervasive monitoring and visibility that are constantly analyzed for indications of compromise.”
- “Enterprise monitoring should be pervasive and encompass as many layers of the IT stack as possible, including network activity, endpoints, system interactions, application transactions, and user activity monitoring.”
- “Improved prevention, detection, response, and prediction capabilities are all needed to deal with all types of attacks, 'advanced' or not. Furthermore, these should not be viewed as siloed capabilities; rather, they should work intelligently together as an integrated, adaptive system to constitute a complete protection process for advanced threats.”
Stages of Adaptive Security Architecture[4]
Gartner lists the four stages of an adaptive security architecture as predict, prevent, respond and defect. These can be briefly defined as:
Predict – assess risk, anticipate attacks and malware, and implement baseline systems and posture.
Prevent – harden and isolate systems to prevent security breaches.
Respond – investigate incidents, design policy changes, and conduct retrospective analysis.
Defect – prioritize risks, and defect and contain incidents.
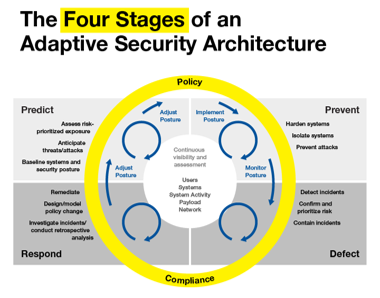
source: Gartner
Objectives of Adaptive Security Architecture[5]
Sun Microsoft lists the following as the objectives of Adaptive Security Architecture:
- Reduce threat amplification – it restricts the potential spread of a pandemic in a monoculture.
- Shrink the attack surface – make the target of an attack smaller
- Decrease attack velocity – slow the rate of attack
- Reduce remediation time – respond to an attack quickly
- Facilitate the availability of data and processing resources – prevent or contain attacks that try to limit resources
- Promote correctness of data and the reliability of processing resources – respond to attacks intended to compromise data or system integrity.
Implementing an Adaptive Security Architecture[6]
Any approach to implementing ASA must be integrated into a larger fabric of the overall security architecture. It must occur within the context of other security features such as application, system, and network design, quality assurance, and configuration validation to ensure that all components and design entities comply with overall security policy.
The following is a list of steps to begin designing an adaptive security model:
• Define threats and threat characteristics that are desirable to avoid or destroy. A threat characteristic may be an attribute of a known threat but may not include the entire threat structure. It may also be particular behavior exhibited by some entity or process.
• Identify acceptable behavior, trusted components, and actions that must not be mistaken for a threat.
• Define triggers to monitor for threats and, as necessary, to invoke an auto-immune system response. These “immune response mediators” are the threat detection sensors that alert the larger IT infrastructure of potential threats and prime the threat response mechanisms.
• Implement redundancy for critical functions. Note that there should not be any critical “trusted” elements that if compromised could cause the entire system to fail. This instantiates the notions of survivability, diversity, and redundancy.
• Define threat response mechanisms that are focused and that do not result in killing the host.
• Define a recovery process whereby systems are capable of adaptively reconfiguring and restarting themselves. Part of this process also includes a learning and knowledge distribution mechanism so the infrastructure learns how to avoid similar threats in the future.
• Define feedback capabilities that allow the threat response mechanisms to validate threats so that they only respond to legitimate and realistic threats. These feedback mechanisms help to ensure that the triggers and threat response mechanisms understand the security context in which they operate. This enables the desired adaptive behavior.
Benefits of Adaptive Security Architecture[7]
Companies have always relied on prevention and policy-based controls for security, deploying products such as anti-virus software, IDS/IPS, and firewalls. Today, we are flooded by advanced and targeted attacks. However, the security architect can advise a shift in the security mindset from ‘incident response’ to ‘continuous response’, by assuming that systems are compromised and require continuous monitoring and remediation. Adaptive Security Architecture has the potential to provide organizations and businesses with the following benefits.
- Real-time Monitoring and Responses: Teams are enabled to move from after-the-fact analysis logs to real-time evaluation of users. This makes a dynamic, immediate, and potentially autonomous response possible.
- Filtering and Prioritizations: By applying advanced analytics and machine learning, organizations can identify some ongoing security breaches they cannot detect by monitoring the system alone.
- Reduce Threat Amplification: Restrict the potential spread of a pandemic in a monoculture.
- Shrink the Attack Surface: Make the target of an attack smaller.
- Decrease the Attack Velocity: Slow the rate of attack.
- Reduce Remediation Time: Responds to attack quickly.
Key Challenges and Recommendations in Designing Adaptive Security Architecture[8]
Key Challenges
- Existing blocking and prevention capabilities are insufficient to protect against motivated, advanced attackers.
- Most organizations continue to overly invest in prevention-only strategies.
- Limited visibility in advanced attacks.
- Because enterprise systems are under continuous attack and are continuously compromised, an ad hoc approach to "incident response" is the wrong mindset.
Recommendations
- Shift from "Incident response" to "Continuous response".
- Adopt an adaptive security architecture.
- Spend less on prevention; invest in detection, response and predictive capabilities.
- Develop a security operations center that supports continuous monitoring.
Analytics and Machine Learning in Adaptive Security[9]
A primary tenet of adaptive security is to always assume there is something wrong with the system. Continual monitoring and improvements of security architecture are the main priorities. The modus operandi is to not wait for an incident to happen, but to expect it, identify it, and respond before having the chance to breach the system. It needs to be a proactive approach model as opposed to a reactive one. Security analytics and machine learning are key components of adaptive security architecture. In addition to this, descriptive analytics detect anomalous events, diagnostic analytics help explain why an adverse event happened and predictive analytics can identify suspicious behavior based on historical data and patterns – both on microscopic and macroscopic levels. With endless reams of Big Data locked up in data warehouses in the cloud and malicious activity disguised as legitimate commands, and server requests becoming nearly impossible to detect, machine learning can serve a useful purpose. It can assist a security team by automating many processes such as pattern recognition used in analytics. MIT’s Computer Science and Artificial Intelligence Lab (CSAIL) is developing an adaptive security platform called AI2. Machine learning is used to review data from tens of millions of data logs per day. It reduces the number of events a cybersecurity analyst must review from one or two hundred to tens of thousands. With the ability to autonomously learn from past successes and failures, it has an 85% success rate in predicting cyber attacks.
See Also
Enterprise Architecture
Architecture
Security Architecture
Gartner’s CARTA Framework
References
- ↑ Definition - Defining Adaptive Security Architecture (ASA) IFP
- ↑ Explaining Adaptive Security Architecture (ASA) Unisys
- ↑ Components of an Adaptive Security Architecture [[1]
- ↑ The Four Stages of Adaptive Security Architecture [2]
- ↑ objectives of Adaptive Security Architecture ASA247
- ↑ Implementing an Adaptive Security Architecture Sun Microsystems (now Oracle)
- ↑ What are the Benefits of Adaptive Security Architecture? cso.com
- ↑ What are the Key Challenges in Designing Adaptive Security Architecture? [3]
- ↑ Analytics and Machine Learning in Adaptive Security [4]
Further Reading
- Enabling Adaptive Security With Advanced Threat Detection Solutions Napatech
- Adaptive security architecture for protecting RESTful web services in enterprise computing environment Mohamed Ibrahim Beer, Mohd Fadzil Hassan
- A Comparison of Methods for Implementing Adaptive Security Policies Michael Carney and Brian Loe
