Protocol Stack
What is Protocol Stack?
A protocol stack, in networking terminology, is a collection of software protocols that provides communications between computers on a network, and between computers and the network infrastructure. The protocol stack model helps to organize layered network models.
The term "stack" is used interchangeably with "protocol stack," but strictly speaking, the latter definition is more accurate. A protocol suite comprises a group of protocols that work together to provide specific communication functions. Protocols within a suite are modularized and designed with a single purpose in mind. This allows for greater efficiency when implementing multiple protocols into an application or system.
Protocols at the bottom of the stack deal with low-level communication hardware, while those higher up add additional capabilities to user applications. For example, TCP/IP—the most common set of protocols on the internet—consists of four layers: physical, data link, network, and transport. Each layer implements specific functionality that enables two-way communication over an electronic channel.
General Protocol Suite Description
T ~ ~ ~ T [A] [B]_____[C]
Imagine three computers: A, B, and C. A and B both have radio equipment and can communicate via airwaves using a suitable network protocol (such as IEEE 802.11). B and C are connected via a cable, using it to exchange data (again, with the help of a protocol, for example, Point-to-Point Protocol). However, neither of these two protocols will be able to transport information from A to C, because these computers are conceptually on different networks. An inter-network protocol is required to connect them.
One could combine the two protocols to form a powerful third, mastering both cable and wireless transmission, but a different super-protocol would be needed for each possible combination of protocols. It is easier to leave the base protocols alone, and design a protocol that can work on top of any of them (the Internet Protocol is an example). This will make two stacks of two protocols each. The inter-network protocol will communicate with each of the base protocols in their simpler language; the base protocols will not talk directly to each other.
A request on computer A to send a chunk of data to C is taken by the upper protocol, which (through whatever means) knows that C is reachable through B. It, therefore, instructs the wireless protocol to transmit the data packet to B. On this computer, the lower layer handlers will pass the packet up to the inter-network protocol, which, on recognizing that B is not the final destination, will again invoke lower-level functions. This time, the cable protocol is used to send the data to C. There, the received packet is again passed to the upper protocol, which (with C being the destination) will pass it on to a higher protocol or application on C.
In practical implementation, protocol stacks are often divided into three major sections: media, transport, and applications. A particular operating system or platform will often have two well-defined software interfaces: one between the media and transport layers, and one between the transport layers and applications. The media-to-transport interface defines how to transport protocol software makes use of particular media and hardware types and is associated with a device driver. For example, this interface level would define how TCP/IP transport software would talk to the network interface controller. Examples of these interfaces include ODI and NDIS in Microsoft Windows and DOS environments. The application-to-transport interface defines how application programs make use of the transport layers. For example, this interface level would define how a web browser program would talk to TCP/IP transport software. Examples of these interfaces include Berkeley sockets and System V STREAMS in Unix-like environments and Winsock for Microsoft Windows.[1]
Types of Protocols
There are various types of protocols that support a major and compassionate role in communicating with different devices across the network. These are:
- Transmission Control Protocol (TCP): TCP is a popular communication protocol that is used for communicating over a network. It divides any message into a series of packets that are sent from source to destination and there it gets reassembled at the destination.
- Internet Protocol (IP): IP is designed explicitly as an addressing protocol. It is mostly used with TCP. The IP addresses in packets help in routing them through different nodes in a network until it reaches the destination system. TCP/IP is the most popular protocol connecting networks.
- User Datagram Protocol (UDP): UDP is a substitute communication protocol for Transmission Control Protocol implemented primarily for creating loss-tolerating and low-latency linking between different applications.
- Post office Protocol (POP): POP3 is designed for receiving incoming E-mails.
- Simple mail transport Protocol (SMTP): SMTP is designed to send and distribute outgoing E-Mail.
- File Transfer Protocol (FTP): FTP allows users to transfer files from one machine to another. Types of files may include program files, multimedia files, text files, documents, etc.
- Hyper Text Transfer Protocol (HTTP): HTTP is designed for transferring a hypertext among two or more systems. HTML tags are used for creating links. These links may be in any form like text or images. HTTP is designed on Client-server principles which allow a client system for establishing a connection with the server machine for making a request. The server acknowledges the request initiated by the client and responds accordingly.
- Hyper Text Transfer Protocol Secure (HTTPS): HTTPS abbreviated as Hyper Text Transfer Protocol Secure is a standard protocol to secure communication between two computers one using the browser and the other fetching data from web server. HTTP is used for transferring data between the client browser (request) and the web server (response) in the hypertext format, the same in the case of HTTPS except that the transferring of data is done in an encrypted format. So it can be said that https thwart hackers from interpreting or modification of data throughout the transfer of packets.
- Telnet: Telnet is a set of rules designed for connecting one system with another. The connecting process here is termed a remote login. The system which requests for connection is the local computer, and the system which accepts the connection is the remote computer.
- Gopher: Gopher is a collection of rules implemented for searching, retrieving as well as displaying documents from isolated sites. Gopher also works on the client/server principle.
Some other popular protocols act as co-functioning protocols associated with these primary protocols for core functioning. These are:
- ARP (Address Resolution Protocol)
- DHCP (Dynamic Host Configuration Protocol)
- IMAP4 (Internet Message Access Protocol)
- SIP (Session Initiation Protocol)
- RTP (Real-Time Transport Protocol)
- RLP (Resource Location Protocol)
- RAP (Route Access Protocol)
- L2TP (Layer Two Tunnelling Protocol)
- PPTP (Point To Point Tunnelling Protocol)
- SNMP (Simple Network Management Protocol)
- TFTP (Trivial File Transfer Protocol)[2]
The TCP/IP Protocol Stack
The TCP/IP Protocol Stack TCP/IP is the world's most widely-used non-proprietary protocol suite because it enables computers using diverse hardware and software platforms, on different types of networks, to communicate. The protocols work equally well in both LANs and WANs. TCP/IP is a collection of protocols named after its two best-known and most important protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP). As well as these relatively low-level protocols, TCP/IP includes several higher-level protocols that facilitate common applications such as electronic mail, terminal emulation, and file transfer.
TCP/IP Layers
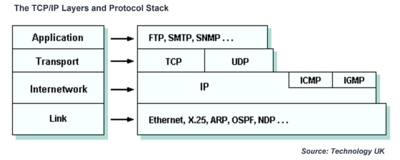
The TCP/IP protocol suite can be modeled as a layered protocol stack, allowing TCP/IP to be compared with other layered models such as the OSI Reference Model. The TCP/IP model has four layers. From lowest to highest, these are the link layer, the internet layer, the transport layer, and the application layer, as shown below.
- The link layer is undefined in some ways, because it may consist of virtually any low-level network technology, including Ethernet, X.25, Point-to-Point Protocol (PPP), or whatever happens to be implemented on a particular network or subnet link. The link layer roughly equates to the data link and physical layers of the OSI 7-layer reference model and provides the interface with the underlying network hardware.
- The internetwork layer provides addressing and routing functions that ensure messages are delivered to their destination. Internet Protocol (IP) is the most important protocol in this layer. It is a connectionless, unreliable protocol that does not provide flow control or error handling, and attempts to deliver datagrams (in the form of IP packets) on a best-effort basis. Network devices called routers forward incoming datagrams according to the destination IP address specified within the IP packet. The internet layer corresponds more or less to the network layer of the OSI model. Other protocols at this layer include Internet Control Messaging Protocol (ICMP) and Internet Group Management Protocol (IGMP).
- The transport layer oversees the end-to-end transfer of data and can handle a number of data streams simultaneously. The main transport layer protocol is Transmission Control Protocol (TCP), which provides a reliable, connection-oriented service. User Datagram Protocol (UDP) provides an unreliable, connectionless service (delivery is not guaranteed, but UDP is useful for applications for which speed is more important than reliability). The transport layer roughly corresponds to its namesake in the OSI model.
- An application layer protocol is specific to a particular type of application (e.g. file transfer, electronic mail, network management, etc.) and is sometimes embodied within the application's client software, although it could also be implemented within the operating system software. The interface between an application layer protocol and a transport layer protocol is defined with reference to port numbers and sockets (more about this later). The application layer effectively combines the functionality of the application, presentation, and session layers of the OSI model.
Each layer in the TCP/IP model handles a particular set of problems involving some aspect of sending data between distributed user applications, i.e. applications that are running on different computers, and often on different networks. Each of the lower three layers provides services to the layer immediately above it, while the application layer provides an interface between the user application above it and the communication-oriented layers below it. As the raw data moves from the application itself down through the various layers, it is wrapped up (or encapsulated) within protocol data units (PDUs) created by each of the protocols it encounters. The names commonly used to refer to these protocol data units tend to vary. At the internet layer, for example, they are called packets or datagrams. At the link layer, they are more often called frames.[3]
See Also
References
- ↑ https://en.wikipedia.org/wiki/Protocol_stack General protocol suite description ]
- ↑ Types of Protocols
- ↑ Technology TCPIP Layers and Protocol Stack