Ransomware
Ransomware, or Ransom malware, is a type of malware that prevents users from accessing their system or personal files and demands ransom payment in order to regain access. The earliest variants of ransomware were developed in the late 1980s, and payment was to be sent via snail mail. Today, ransomware authors order that payment be sent via cryptocurrency or credit card.[1]
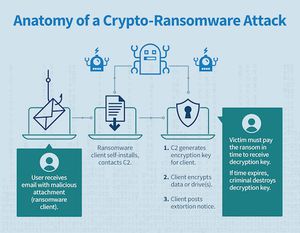
Anatomy of a Ransomware Attack[2]
A common form of delivering ransomware is through malicious attachments to email messages. Users are convinced against their better judgment – through social engineering – to open the attachment. The attachment is typically a form of self-installing malware, often called a Trojan or virus dropper file. Once installed, the dropper enrolls in a cyberattacker’s botnet by contacting the botnet command and control (C2). When contacted, the C2 will generate and return encryption-keying material for the ransomware dropper (and possibly additional malicious code). The ransomware dropper will use the keying material to encrypt personal files on the infected device. It then posts an extortion notification, demanding that the victim pay a ransom payment for a key that will decrypt the now inaccessible data.
Many ransomware attackers threaten victims with permanent loss of their personal files if the ransom is not paid within a 24-hour timeframe. To enhance deception, some ransomware notifications impersonate law enforcement or government agencies and represent the extortion as a fine.
How Ransomware Works[3]
The good news is that ransomware does not usually appear on its own. It must be activated in order to deliver its payload, usually through a malicious link or attachment in an email. There are generally five steps required for ransomware to achieve its objective:
- The System Is Compromised: The majority of ransomware attacks start life as a social engineering exercise, usually in the form of an attachment or malicious link. The aim is to entice the user to click on these objects in order to activate the malware.
- The Malware Takes Control: Once the malware has taken control of the system, certain file types will be encrypted and access will be denied to users.
- The Victim Is Notified: For the ransom to be paid, the user must be aware of the demands of the criminals. At this point, they will usually receive notification on the screen explaining the demands and how they can regain access.
- The Ransom Is Paid: Once they have system access, attackers will either identify and encrypt certain file types or deny access to the entire system.
- Full Access Is Returned: In the majority of cases, attackers return full control to the victim. It is in their interest to do this; failure to do so would mean few organizations would be willing to pay if they didn't believe their data would be restored.
Preventing Ransomware<re>How to prevent ransomware CSO Online</ref>
There are a number of defensive steps you can take to prevent ransomware infection. These steps are a of course good security practices in general, so following them improves your defenses from all sorts of attacks:
Keep your operating system patched and up-to-date to ensure you have fewer vulnerabilities to exploit. Don't install software or give it administrative privileges unless you know exactly what it is and what it does. Install antivirus software, which detects malicious programs like ransomware as they arrive, and whitelisting software, which prevents unauthorized applications from executing in the first place. And, of course, back up your files, frequently and automatically! That won't stop a malware attack, but it can make the damage caused by one much less significant.
- ↑ Definition - What Does Ransomware Mean? Malwarebytes
- ↑ Anatomy of a Ransomware Attack Icann
- ↑ How Ransomware Works Forcepoint