Difference between revisions of "Threat Agent Risk Assessment (TARA)"
| Line 6: | Line 6: | ||
| − | + | '''The TARA Process<ref>The TARA Process in Detail [https://www.researchgate.net/publication/335589639_Prioritizing_Information_Security_Risks_with_Threat_Agent_Risk_Assessment_TARA Matt Rosenquist, Timothy Casey]</ref>'''<br /> | |
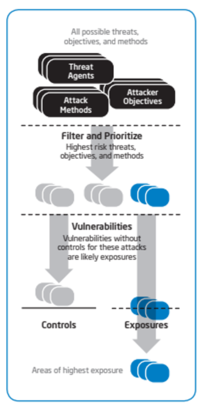
| − | The TARA Process in Detail | + | To find the critical areas of exposure, the TARA methodology uses six steps.<br /> |
| − | To find the critical areas of exposure, the TARA methodology uses six steps. | + | 1. Measure current threat agent: Using the TAL. regularly review and rank the current threat levels. This is a qualitative to quantitative exercise necessary to establish a general understanding of current risks, and it creates a baseline for future TARA exercises.<br />2. Distinguish threat agents that exceed baseline acceptable risks: Again using the TAL, measure new threat levels when starting a new project; create an acceptable risk baseline if current baseline is determined to be insufficient.<br />At the end of steps 1 and 2, threat agents that exceed the current or new baseline threat level for the areas being evaluated will have been identified.<br />3. Derive primary objectives of those threat agents. TARA defines objectives as the combination of threat agent motivations and threat agent capabilities. Using the MOL - derive the primary motivations and objectives of those threat agents identified in steps 1 and 2. Motivations are important because they underpin action, and they contribute to factors such as the attacker’s commitment, the point at which attacker will cease pursuit, and the attacker’s susceptibility to targets of opportunity.<br />4. Identify methods likely to manifest. Again using the MOL - identify the likely methods by which an attack may occur. TARA defines a method as a combination of threat agent objectives and threat agent operating methods. TARA identifies the type of impact that could be expected based on motivations and objectives.<br />5. Determine the most important collective exposures. Using the CEL, the methodology first finds attack vectors, which are vulnerabilities without controls. Then, the intersection of the methods determined in step 4 and the attack vectors define likely exposures. Finally, these likely exposures are ranked according to their severity of consequence. The end result of step 5 is a list of the most important collective exposures.<br />6. Align strategy to target the most significant exposures. An assessment is worthless if it does not reinforce the decision-making process. Analysts and management can use the results of TARA analysis to concentrate their [[Information Security|information security]] strategy on the most important areas of concern and allocate [[Information Security Governance|information security resources]] in the most effective manner. |
| − | 1. Measure current threat agent: regularly review and rank the current threat levels. This is a qualitative to quantitative exercise necessary to establish a general understanding of current risks, and it creates a baseline for future TARA exercises. | ||
| − | 2. Distinguish threat agents that exceed baseline acceptable risks: measure new threat levels when starting a new project; create an acceptable risk baseline if current baseline is determined to be insufficient. | ||
| − | At the end of steps 1 and 2, threat agents that exceed the current or new baseline threat level for the areas being evaluated will have been identified. | ||
| − | 3. Derive primary objectives of those threat agents. TARA defines objectives as the combination of threat agent motivations and threat agent capabilities. | ||
| − | Using the MOL | ||
| − | motivations and objectives of those | ||
| − | threat agents identified in steps 1 and 2. | ||
| − | Motivations are important because they | ||
| − | underpin action, and they contribute to | ||
| − | factors such as the attacker’s commitment, | ||
| − | the point at which attacker will cease | ||
| − | pursuit, and the attacker’s susceptibility to | ||
| − | targets of opportunity. | ||
| − | |||
| − | 4. Identify methods likely to manifest. | ||
| − | Again using the MOL | ||
| − | methods by which an attack may occur. | ||
| − | TARA defines a method as a combination | ||
| − | of threat agent objectives and threat | ||
| − | agent operating methods. TARA identifies | ||
| − | the type of impact | ||
| − | on motivations and objectives. | ||
| − | 5. Determine the most important | ||
| − | collective exposures. Using the CEL, the | ||
| − | methodology first finds attack vectors, | ||
| − | which are vulnerabilities without controls. | ||
| − | Then, the intersection of the methods | ||
| − | determined in step 4 and the attack | ||
| − | vectors define likely exposures. Finally, | ||
Revision as of 18:23, 20 March 2020
The Threat Agent Risk Assessment (TARA) is a threat-based methodology to help identify, assess, prioritize, and control cybersecurity risks. It is a practical method to determine the most critical exposures while taking into consideration mitigation controls and accepted levels of risk. It is intended to augment formal risk methodologies to include important aspects of attackers, resulting in a much improved picture of risk.[1]
The TARA Process[2]
To find the critical areas of exposure, the TARA methodology uses six steps.
1. Measure current threat agent: Using the TAL. regularly review and rank the current threat levels. This is a qualitative to quantitative exercise necessary to establish a general understanding of current risks, and it creates a baseline for future TARA exercises.
2. Distinguish threat agents that exceed baseline acceptable risks: Again using the TAL, measure new threat levels when starting a new project; create an acceptable risk baseline if current baseline is determined to be insufficient.
At the end of steps 1 and 2, threat agents that exceed the current or new baseline threat level for the areas being evaluated will have been identified.
3. Derive primary objectives of those threat agents. TARA defines objectives as the combination of threat agent motivations and threat agent capabilities. Using the MOL - derive the primary motivations and objectives of those threat agents identified in steps 1 and 2. Motivations are important because they underpin action, and they contribute to factors such as the attacker’s commitment, the point at which attacker will cease pursuit, and the attacker’s susceptibility to targets of opportunity.
4. Identify methods likely to manifest. Again using the MOL - identify the likely methods by which an attack may occur. TARA defines a method as a combination of threat agent objectives and threat agent operating methods. TARA identifies the type of impact that could be expected based on motivations and objectives.
5. Determine the most important collective exposures. Using the CEL, the methodology first finds attack vectors, which are vulnerabilities without controls. Then, the intersection of the methods determined in step 4 and the attack vectors define likely exposures. Finally, these likely exposures are ranked according to their severity of consequence. The end result of step 5 is a list of the most important collective exposures.
6. Align strategy to target the most significant exposures. An assessment is worthless if it does not reinforce the decision-making process. Analysts and management can use the results of TARA analysis to concentrate their information security strategy on the most important areas of concern and allocate information security resources in the most effective manner.
- ↑ Definition - What Does Threat Agent Risk Assessment (TARA) Mean? Matthew Rosenquist, Timothy Casey
- ↑ The TARA Process in Detail Matt Rosenquist, Timothy Casey