Threat Agent Risk Assessment (TARA)
The Threat Agent Risk Assessment (TARA) is a threat-based methodology to help identify, assess, prioritize, and control cybersecurity risks. It is a practical method to determine the most critical exposures while taking into consideration mitigation controls and accepted levels of risk. It is intended to augment formal risk methodologies to include important aspects of attackers, resulting in a much improved picture of risk.[1]
TARA Components[2]
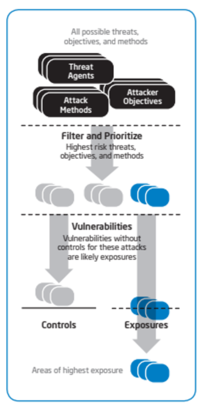
The TARA methodology relies on three main references to reach its predictive conclusions:
- Threat agent library (TAL): The primary premise of the TARA methodology is that threat agents are the source of information security losses. Previously, Intel developed the TAL to simplify the character set of all possible threat agents. It was therefore a natural choice to use it with the TARA methodology. The Intel TAL defines eight common threat agent attributes, such as intent—hostile or non-hostile—and access—internal or external. Based on unique combinations of these attributes, the TAL identifies 22 unique threat agent archetypes, such as disgruntled employee, competitor, and organized crime. It is important to remember that the TAL provides archetypes, not exact descriptions of real people; individuals may vary in degree of hostility from the model, for example.
- Methods and objectives library (MOL): The MOL lists known threat agent objectives — what they want to accomplish — and the most likely methods they will employ to reach these objectives. These methods and objectives are cross-referenced with defense-indepth controls, such as firewalls, proxies, secure device configurations, and a securityaware workforce. When the MOL is coupled with the TAL, a picture begins to emerge of the types of likely possible attacks, based upon many factors such as resources, objectives, typical methods, and preferred vulnerabilities. Additionally, an estimate of consequences begins to form. When the CEL is overlaid on this picture, those vulnerabilities with sufficient controls aligned to reduce risk are dropped, and the remaining vectors of attack emerge as the areas of highest exposure.
- Common exposure library (CEL): For the first application of the TARA methodology, Intel created CEL, which enumerates known information security vulnerabilities and exposures. There are also several publicly available CELs that provide additional data. The CEL maps vulnerabilities against existing controls to show which exposures are residual. For example, with an antivirus solution installed on corporate laptop PCs, currently known viruses do not represent an overt exposure. However, if an unknown virus appears before the antivirus solution is updated, then an appreciable residual exposure exists.
Standard frameworks such as these help ensure consistency and comprehensiveness when different risk assessors apply TARA methodology to different environments.
The TARA Process[3]
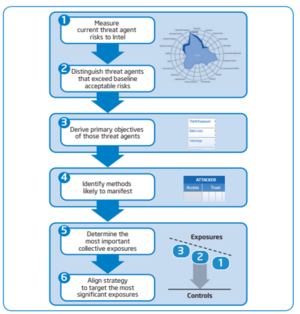
To find the critical areas of exposure, the TARA methodology uses six steps.
1. Measure current threat agent: Using the TAL. regularly review and rank the current threat levels. This is a qualitative to quantitative exercise necessary to establish a general understanding of current risks, and it creates a baseline for future TARA exercises.
2. Distinguish threat agents that exceed baseline acceptable risks: Again using the TAL, measure new threat levels when starting a new project; create an acceptable risk baseline if current baseline is determined to be insufficient.
At the end of steps 1 and 2, threat agents that exceed the current or new baseline threat level for the areas being evaluated will have been identified.
3. Derive primary objectives of those threat agents. TARA defines objectives as the combination of threat agent motivations and threat agent capabilities. Using the MOL - derive the primary motivations and objectives of those threat agents identified in steps 1 and 2. Motivations are important because they underpin action, and they contribute to factors such as the attacker’s commitment, the point at which attacker will cease pursuit, and the attacker’s susceptibility to targets of opportunity.
4. Identify methods likely to manifest. Again using the MOL - identify the likely methods by which an attack may occur. TARA defines a method as a combination of threat agent objectives and threat agent operating methods. TARA identifies the type of impact that could be expected based on motivations and objectives.
5. Determine the most important collective exposures. Using the CEL, the methodology first finds attack vectors, which are vulnerabilities without controls. Then, the intersection of the methods determined in step 4 and the attack vectors define likely exposures. Finally, these likely exposures are ranked according to their severity of consequence. The end result of step 5 is a list of the most important collective exposures.
6. Align strategy to target the most significant exposures. An assessment is worthless if it does not reinforce the decision-making process. Analysts and management can use the results of TARA analysis to concentrate their information security strategy on the most important areas of concern and allocate information security resources in the most effective manner.
See Also
- OCTAVE (Operationally Critical Threat, Asset and Vulnerability Evaluation)
- Factor Analysis of Information Risk (FAIR)
References
- ↑ Definition - What Does Threat Agent Risk Assessment (TARA) Mean? -Matthew Rosenquist, Timothy Casey
- ↑ TARA Components Intel Information Technology
- ↑ The TARA Process in Detail Matt Rosenquist, Timothy Casey