Security Reference Model (SRM)
The Security Reference Model (SRM) is a framework used to define and organize the security requirements for an information system. It is part of the overall enterprise architecture and is used to guide the development and implementation of security controls.
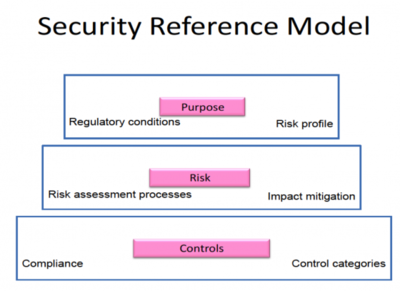
The SRM defines the security domains and components of an information system, as well as the relationships between them. It provides a systematic approach to designing and implementing security controls based on the specific needs and risks of the organization.
The SRM is typically composed of three main components: the security objectives, the security reference architecture, and the security controls. The security objectives define the goals and requirements of the security program, such as confidentiality, integrity, availability, and compliance.
The security reference architecture defines the structure and components of the security program, such as the security domains, layers, and components. It also defines the interfaces and interactions between the components.
Security controls are the specific measures and techniques to protect the information system and its assets. These may include physical controls, such as access controls and surveillance systems, and technical controls, such as firewalls, encryption, and intrusion detection systems.
The SRM is designed to be flexible and adaptable to the specific needs and risks of each organization. It provides a structured approach to security planning and implementation, allowing customization and innovation.
The benefits of using an SRM include increased security effectiveness and efficiency, improved communication and collaboration among stakeholders, and better alignment between security objectives and business goals. It also helps organizations to meet regulatory and compliance requirements, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS).
In conclusion, the Security Reference Model (SRM) is a framework used to define and organize the security requirements for an information system. It provides a systematic approach to designing and implementing security controls based on the specific needs and risks of the organization. The SRM is flexible and adaptable and provides numerous benefits for organizations looking to improve their security posture.