Cyber Security
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users; or interrupting normal business processes.[1]
Approach to Cyber Security[2]
An effective approach to cyber security starts with establishing an effective organisational risk management regime (shown at the centre of the following diagram). This regime and the 9 steps that surround it are described below.
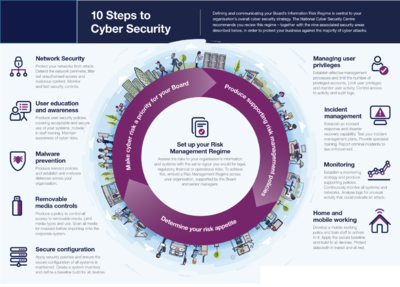
source: National Cyber Security Center
- Risk Management Regime: Embed an appropriate risk management regime across the organisation. This should be supported by an empowered governance structure, which is actively supported by the board and senior managers. Clearly communicate your approach to risk management with the development of applicable policies and practices. These should aim to ensure that all employees, contractors and suppliers are aware of the approach, how decisions are made, and any applicable risk boundaries.
- Secure configuration: Having an approach to identify baseline technology builds and processes for ensuring configuration management can greatly improve the security of systems. You should develop a strategy to remove or disable unnecessary functionality from systems, and to quickly fix known vulnerabilities, usually via patching. Failure to do so is likely to result in increased risk of compromise of systems and information.
- Network security: The connections from your networks to the Internet, and other partner networks, expose your systems and technologies to attack. By creating and implementing some simple policies and appropriate architectural and technical responses, you can reduce the chances of these attacks succeeding (or causing harm to your organisation). Your organisation's networks almost certainly span many sites and the use of mobile or remote working, and cloud services, makes defining a fixed network boundary difficult. Rather than focusing purely on physical connections, think about where your data is stored and processed, and where an attacker would have the opportunity to interfere with it.
- Managing user privileges: If users are provided with unnecessary system privileges or data access rights, then the impact of misuse or compromise of that users account will be more severe than it need be. All users should be provided with a reasonable (but minimal) level of system privileges and rights needed for their role. The granting of highly elevated system privileges should be carefully controlled and managed. This principle is sometimes referred to as ‘least privilege’.
- User education and awareness: Users have a critical role to play in their organisation’s security and so it's important that security rules and the technology provided enable users to do their job as well as help keep the organisation secure. This can be supported by a systematic delivery of awareness programmes and training that deliver security expertise as well as helping to establish a security-conscious culture.
- Incident management: All organisations will experience security incidents at some point. Investment in establishing effective incident management policies and processes will help to improve resilience, support business continuity, improve customer and stakeholder confidence and potentially reduce any impact. You should identify recognised sources (internal or external) of specialist incident management expertise.
- Malware prevention: Malicious software, or malware is an umbrella term to cover any code or content that could have a malicious, undesirable impact on systems. Any exchange of information carries with it a degree of risk that malware might be exchanged, which could seriously impact your systems and services. The risk may be reduced by developing and implementing appropriate anti-malware policies as part of an overall 'defence in depth' approach.
- Monitoring: System monitoring provides a capability that aims to detect actual or attempted attacks on systems and business services. Good monitoring is essential in order to effectively respond to attacks. In addition, monitoring allows you to ensure that systems are being used appropriately in accordance with organisational policies. Monitoring is often a key capability needed to comply with legal or regulatory requirements.
- Removable media controls: Removable media provide a common route for the introduction of malware and the accidental or deliberate export of sensitive data. You should be clear about the business need to use removable media and apply appropriate security controls to its use.
- Home and mobile working: Mobile working and remote system access offers great benefits, but exposes new risks that need to be managed. You should establish risk based policies and procedures that support mobile working or remote access to systems that are applicable to users, as well as service providers. Train users on the secure use of their mobile devices in the environments they are likely to be working in.
The Importance of Cybersecurity[3]
The world relies on technology more than ever before. As a result, digital data creation has surged. Today, businesses and governments store a great deal of that data on computers and transmit it across networks to other computers. Devices and their underlying systems have vulnerabilities that, when exploited, undermine the health and objectives of an organization.
A data breach can have a range of devastating consequences for any business. It can unravel a company’s reputation through the loss of consumer and partner trust. The loss of critical data, such as source files or intellectual property, can cost a company its competitive advantage. Going further, a data breach can impact corporate revenues due to non-compliance with data protection regulations. It’s estimated that, on average, a data breach costs an affected organization $3.6 million. With high-profile data breaches making media headlines, it’s essential that organizations adopt and implement a strong cybersecurity approach.
The scale of the Cyber Threat[4]
The global cyber threat continues to evolve at a rapid pace, with a rising number of data breaches each year. A report by RiskBased Security revealed that a shocking 7.9 billion records have been exposed by data breaches in the first nine months of 2019 alone. This figure is more than double (112%) the number of records exposed in the same period in 2018.
Medical services, retailers and public entities experienced the most breaches, with malicious criminals responsible for most incidents. Some of these sectors are more appealing to cybercriminals because they collect financial and medical data, but all businesses that use networks can be targeted for customer data, corporate espionage, or customer attacks.
With the scale of the cyber threat set to continue to rise, the International Data Corporation predicts that worldwide spending on cyber-security solutions will reach a massive $133.7 billion by 2022. Governments across the globe have responded to the rising cyber threat with guidance to help organizations implement effective cyber-security practices.
In the U.S., the National Institute of Standards and Technology (NIST) has created a cyber-security framework. To combat the proliferation of malicious code and aid in early detection, the framework recommends continuous, real-time monitoring of all electronic resources.
The importance of system monitoring is echoed in the “10 steps to cyber security”, guidance provided by the U.K. government’s National Cyber Security Centre. In Australia, The Australian Cyber Security Centre (ACSC) regularly publishes guidance on how organizations can counter the latest cyber-security threats.
Types of Cyber Attacks[5]
Cyber attacks come in all shapes and sizes. Some may be overt ransomware attacks (hijacking important business products or tools in exchange for money to release them), while some are covert operations by which criminals infiltrate a system to gain valuable data only to be discovered months after-the-fact, if at all. Criminals are getting craftier with their malicious deeds and here are some of the basic types of cyber attacks affecting thousands of people each day.
- Malware: Malware is used to describe malicious software, including spyware, ransomware and viruses. It usually breaches networks through a vulnerability, like clicking on suspicious email links or installing a risky application. Once inside a network, malware can obtain sensitive information, further produce more harmful software throughout the system and can even block access to vital business network components (ransomware).
- Phishing: Phishing is the practice of sending malicious communications (usually emails) designed to appear from reputable, well-known sources. These emails use the same names, logos, wording, etc., as a CEO or company to dull suspicions and get victims to click on harmful links. Once a phishing link is clicked, cyber criminals have access to sensitive data like credit card, social security or login information.
- Social Engineering: Social engineering is the process of psychologically manipulating people into divulging personal information. Phishing is a form of social engineering, where criminals take advantage of people’s natural curiosity or trust. An example of more advanced social engineering is with voice manipulation. In this case, cyber criminals take an individual’s voice (from sources like a voicemail or social media post) and manipulate it to call friends or relatives and ask for credit card or other personal information.
- Man-in-the-Middle Attack: Man-in-the-Middle (MitM) attacks occur when criminals interrupt the traffic between a two-party transaction. For example, criminals can insert themselves between a public Wi-Fi and an individual’s device. Without a protected Wi-Fi connection, cyber criminals can sometimes view all of a victim’s information without ever being caught.
- Zero-day attack: Zero-day attacks are becoming more-and-more common. Essentially, these attacks occur between a network vulnerability announcement and a patch solution. In the name of transparency and security, most companies will announce that they found a problem with their network safety, but some criminals will take this opportunity to unleash attacks before the company can come up with a security patch.
Cyber Security vs. Computer Security vs. IT Security vs. Information Security
Cyber security is the practice of defending your electronic systems, networks, computers, mobile devices, programs and data from malicious digital attacks. Cybercriminals can deploy a variety of attacks against individual victims or businesses that can include accessing, changing or deleting sensitive data; extorting payment; or interfering with business processes.
How is cyber security achieved? Through an infrastructure that’s divided into three key components: IT security, cyber security, and computer security.
Information technology (IT) security, also known as electronic information security, is the protection of data both where it is stored and while moving through a network. While cyber security only protects digital data, IT security protects both digital and physical data from intruders. Cyber security is a subset of IT security. While IT security protects both physical and digital data, cyber security protects the digital data on your networks, computers and devices from unauthorized access, attack and destruction. Network security, or computer security, is a subset of cyber security. This type of security uses hardware and software to protect any data that’s sent through your computer and other devices to the network. Network security serves to protect the IT infrastructure and guard against information being intercepted and changed or stolen by cybercriminals.
Often information technology security professionals and cyber security professionals will work hand in hand to protect a company’s data and prevent unauthorized access. Although in many instances today, both an IT security professional and a cyber security professional will not both be employed by a company. In many companies, cyber security professionals will be found addressing the needs of protecting all data.
Cyber Security involves anything security-related in the cyber realm (or cyberspace). Information security involves the security of information or information systems regardless of the realm it occurs in (e.g., risk of exposure in physical world). Since anything that occurs in the cyber realm would involve the protection of information and information systems in some way, you can conclude that information security is a super-set of cyber security.
Below is a graphic that shows how cyber security is often considered a part of Information Security.
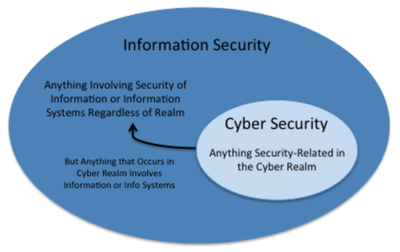
source: NovaInfosec
Cybersecurity Best Practices[6]
To minimize the risks of cyberattacks, follow basic cybersecurity best practices:
- Keep software up to date. Install software patches so that attackers cannot take advantage of known problems or vulnerabilities. Many operating systems offer automatic updates. If this option is available, you should enable it.
- Run up-to-date antivirus software. A reputable antivirus software application is an important protective measure against known malicious threats. It can automatically detect, quarantine, and remove various types of malware. Be sure to enable automatic virus definition updates to ensure maximum protection against the latest threats. Note: Because detection relies on signatures—known patterns that can identify code as malware—even the best antivirus will not provide adequate protections against new and advanced threats, such as zero-day exploits and polymorphic viruses.
- Use strong passwords. Select passwords that will be difficult for attackers to guess, and use different passwords for different programs and devices. It is best to use long, strong passphrases or passwords that consist of at least 16 characters.
- Change default usernames and passwords. Default usernames and passwords are readily available to malicious actors. Change default passwords, as soon as possible, to a sufficiently strong and unique password.
- Implement multi-factor authentication (MFA). Authentication is a process used to validate a user’s identity. Attackers commonly exploit weak authentication processes. MFA uses at least two identity components to authenticate a user’s identity, minimizing the risk of a cyberattacker gaining access to an account if they know the username and password.
- Install a firewall. Firewalls may be able to prevent some types of attack vectors by blocking malicious traffic before it can enter a computer system, and by restricting unnecessary outbound communications. Some device operating systems include a firewall. Enable and properly configure the firewall as specified in the device or system owner’s manual.
- Be suspicious of unexpected emails. Phishing emails are currently one of the most prevalent risks to the average user. The goal of a phishing email is to gain information about you, steal money from you, or install malware on your device. Be suspicious of all unexpected emails.
Managing Cyber Security[7]
The National Cyber Security Alliance, through SafeOnline.org, recommends a top-down approach to cyber security in which corporate management leads the charge in prioritizing cyber security management across all business practices. NCSA advises that companies must be prepared to “respond to the inevitable cyber incident, restore normal operations, and ensure that company assets and the company’s reputation are protected.” NCSA’s guidelines for conducting cyber risk assessments focus on three key areas: identifying your organization’s “crown jewels,” or your most valuable information requiring protection; identifying the threats and risks facing that information; and outlining the damage your organization would incur should that data be lost or wrongfully exposed. Cyber risk assessments should also consider any regulations that impact the way your company collects, stores, and secures data, such as PCI-DSS, HIPAA, SOX, FISMA, and others. Following a cyber risk assessment, develop and implement a plan to mitigate cyber risk, protect the “crown jewels” outlined in your assessment, and effectively detect and respond to security incidents. This plan should encompass both the processes and technologies required to build a mature cyber security program. An ever-evolving field, cyber security best practices must evolve to accommodate the increasingly sophisticated attacks carried out by attackers. Combining sound cyber security measures with an educated and security-minded employee base provides the best defense against cyber criminals attempting to gain access to your company’s sensitive data. While it may seem like a daunting task, start small and focus on your most sensitive data, scaling your efforts as your cyber program matures.
Cybersecurity Challenges[8]
Cybersecurity is continually challenged by hackers, data loss, privacy, risk management, and changing cybersecurity strategies. Nothing currently indicates that cyber-attacks will decrease. Moreover, with the more entry points, there are for attacks, the more cybersecurity is needed to secure networks and devices.
One of the most problematic elements of cybersecurity is the continually evolving nature of security risks. As new technologies emerge, and technology is used in new or different ways, new avenues of attack are developed as well. Keeping up with these continual changes and advances in attacks can be challenging to organizations, as well as updating their practices to protect against them. This also includes ensuring that all the elements of cybersecurity are continually changed and updated to protect against potential vulnerabilities. This can be especially challenging for smaller organizations.
Additionally, today, there is a lot of potential data an organization can gather on individuals who take part in one of their services. With more data being collected, the likelihood of a cybercriminal who wants to steal personally identifiable information is another concern. For example, an organization that stores personally identifiable information in the cloud may be subject to a ransomware attack, and should do what they can to prevent a cloud breach.
Cybersecurity should also address end-user education, as an employee may accidently bring a virus into a workplace on their work computer, laptop, or smartphone.
Another large challenge to cybersecurity includes a job shortage. As growth in data from businesses become more important, the need for more cybersecurity personnel to analyze, manage and respond to incidents increases. It is estimated that there are two million unfilled cybersecurity jobs worldwide. Cybersecurity Ventures also estimates that by 2021, there will be up to 3.5 million unfilled cybersecurity jobs.
However, new advances in machine learning and artificial intelligence (AI) have started to be developed to help in organizing and managing data -- although not to the effect needed.
See Also
Data Security
Security Architecture
Security Policy
Security Reference Model (SRM)
Information Security Governance
Information Security
Adaptive Security Architecture (ASA)
Business Model for Information Security (BMIS)
Common Data Security Architecture (CDSA)
Payment Card Industry Data Security Standard (PCI DSS)
Data Security
Computer Security
Enterprise Information Security Architecture (EISA)
Fault Configuration Accounting Performance Security (FCAPS)
Graduated Security
Information Systems Security (INFOSEC)
Information Security Management System (ISMS)
Information Technology Security Assessment
Mobile Security
Network Security
Cyber Crime
Cyber Espionage
Cybernetics
Cyberspace
Internet Crime
Internet Reputation
Malvertising
References
- ↑ Defining Cybersecurity Cisco
- ↑ 10 Steps To Cyber Security NCSC
- ↑ Why is cybersecurity important? Forcepoint
- ↑ The scale of the Cyber Threat Kaspersky USA
- ↑ Types of Cyber Attacks Builtin
- ↑ Cybersecurity Best Practices CISA
- ↑ Managing Cyber Security Digital Guardian
- ↑ Cybersecurity Challenges Techtarget
