Machine-to-Machine (M2M)
Machine-to-Machine (M2M) communication is a form of data communication that involves one or more entities that do not necessarily require human interaction or intervention in the process of communication. M2M is also named as Machine Type Communication (MTC) in 3GPP. It is different from the current communication models in the ways that it involves:
- new or different market scenarios
- lower costs and effort
- a potentially very large number of communicating terminals
- little traffic per terminal, in general
M2M communication could be carried over mobile networks (e.g. GSM-GPRS, CDMA EVDO networks). In the M2M communication, the role of mobile network is largely confined to serve as a transport network. With a potential market of probably 50 million connected devices, M2M offers tremendous opportunities as well as unique challenges. These devices vary from highly-mobile vehicles communicating in real-time, to immobile meter-reading appliances that send small amounts of data sporadically.[1]
Machine-to-Machine (M2M) Communication Architecture[2]
A generic M2M communication architecture is shown in Figure 1. To support the high number of M2M devices (billions to trillions) that are expected to be part of an M2M network, hierarchical communication architectures have been proposed. At the highest level, the goal of M2M architectures is to aggregate information from data collectors, and to apply some decision-making function to this information to produce decisions which are then executed. Several data collectors (e.g. temperature sensors, location sensors or heart rate monitors) are used to collect information from multiple locations. Data collectors gather data in areas that are small compared to the total area covered by the M2M architecture. The data collectors are usually separated in physical space and can collect information from various types of sources. For example, one data collector could record the ambient temperature in one location, and another could record the current consumed by a television set in another distant physical location.
Figure 1. Generic M2M communication architecture
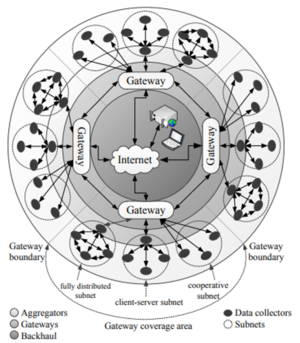
source: KSII
In M2M architectures, data collectors of the same type are connected to small networks (e.g. Body Area Networks (BANs), Zigbee, and Bluetooth), called subnets. Each subnet uses a network technology appropriate for the type of information to be collected and distributed. The network technology which is employed determines the subnet architecture. Three types of subnets (fully distributed, client-server and cooperative) are shown in Figure 1. In a fully distributed network, all nodes (e.g. various computers on a home Wi-Fi network) are connected as peers and share data amongst themselves. One of the nodes (e.g. a router’s Wi-Fi module) acts as a super-peer that has the ability to connect through some gateway (e.g. a router’s ADSL connection) to the Internet. In a client-server network, all clients onlycommunicate with the server; an example would be portable media players connecting to a media server. The server then relays appropriate information to other clients (e.g. wireless speakers). The server also has the ability to connect to the Internet through some gateway (e.g. a home router). A cooperative network is not, strictly speaking, a subnet. None of the nodes
(e.g. BAN sensors) communicate directly with each other as is the case on a subnet, but rather via the gateway (e.g. a cellular phone).
The collected data is then aggregated at possibly multiple layers of aggregation points. The number of aggregation layers depends on the expected number of M2M devices and how these devices are logically grouped. At each aggregation layer, data from multiple data collectors can be aggregated by applying some intelligence to the data. This means that the aggregation function is not merely assembling the data, but it can also reduce the amount of data retransmitted. This can be achieved, for example, through filtering data based on relevance, or by extracting higher-level information from aggregated data. Data aggregation is used to allow M2M devices to have low cost, consume little power and have a limited operating area. This is required to enable a system of billions to trillions of these devices.
Multiple local subnets using different communication standards can communicate with each other using some gateway which provides Internet connectivity or a similar backhaul network. The gateway typically interfaces with at least one device on each subnet to which it is connected, and is also connected to other gateways. An end-user can connect to a server to access information collected from the M2M data collectors. This server may be connected to the Internet or some other backhaul network. The function of the M2M server is to perform final processing tasks on the collected data, to store the data, log the transactions that occurred and to make the data available online to the various users of the M2M system.
Features of M2M Communications[3]
The most important features of an M2M Communication system are:
- Low Mobility: M2M devices do not move, move infrequently, or move only within a certain region.
- Application Independent: M2M devices enable communications to key applications that don’t have any communication today and are completely transparent to the application. The application is unaware that the communication service is provided by a wired or wireless connection. IP-based: As LMR communication networks migrate from analog to digital, these new digital networks support IP bearer services and have the ability to transport both IP and serial-based protocols over the IP-based network.
- Small Data Transmissions: M2M devices frequently send or receive small amounts of data, leveraging the extra capacity enabled by migrating to a new TDMA-based digital LMR network.
- High Reliability: High reliability means that whenever and wherever M2M communication is required or triggered, the connection and reliable transmission between the M2M device and the M2M server shall be available, regardless of the operating environment. High reliability is required in M2M applications that involve either the prospect of an emergency or highly sensitive data. Utility LMR systems have long been designed for high reliability for their voice needs, and the benefit of this is extended directly to the M2M applications that leverage the same network. Mission critical radio networks are designed for high reliability and redundancy where failure is not an option while business enterprise operations networks are not designed to meet the same redundancy and reliability specifications.
- Network Priority: Network priority means that there is a method for providing a hierarchical prioritization of users or applications within the solution when applications, voice or data, are competing for network access.The P25, TETRA and DMR standards and the systems provided by the manufacturers have provisions in their protocols to accommodate a prioritization scheme, whether it is simple or sophisticated. This is important as utilities have long considered their voice communications to be mission critical because they rely on them for both safety and security, such that prioritization cannot be disrupted. Many fixed data applications, which weren’t previously considered mission critical, are now being considered as such since the information about the water facility’s performance has a direct impact on a utility’s operation and performance.
- Security: Security functions include the protection and confidentiality of M2M data, authentication of users prior to access to M2M devices, and encryption of the data transferred across M2M networks. Knowing that utilities desire private LMR networks for their higher levels of security provides a strong platform that can be leveraged when using the same security for M2M applications.
- Latency Tolerant: Latency is a time interval between the stimulation and response. When leveraging a LMR network for M2M the target applications should be those that aren’t latency sensitive. The general one-way latency of an LMR network is approximately 1 second. Those polled applications or reports by exception-based applications that don’t require immediate responses measured in milliseconds but rather in seconds are target applications for M2M over LMR.
IoT and the M2M Economy[4]
The processing power of such IoT devices and the heaps of data generated by them can be of great value.
For instance, an individual having a water purifier fitted in his home no longer needs to worry about the intricacies and step-by-step monitoring of the purifying process. Depending upon the hardness of the incoming water, the microprocessor-fitted purifier can schedule the purifying cycle and let the water be treated to a specified level of hardness. The same device can also be equipped with sensors to assess the residual quality of the purifying cartridge and is also capable of sending alerts to the service center to request a replacement.
Additionally, the data generated by such devices offers great value. It can assist in assessing consumption behavior and usage patterns and will also serves to inform macro-level tasks like city planning and assessing the quality and demand of water across a region. Additionally, device owners can willingly sell selected data points for monetary rewards.
Beyond such basic workings of the device and automated communication across a network comprised of installed devices, many blockchain-based projects are being launched to harness the power of such commonly used appliances. For instance, the processors and memory modules fitting in these IoT devices can be utilized for cryptocurrency mining and transaction authentication activities. Projects like IOTA, IoT Chain, and IOTW are attempting to harness the power and resources for their blockchain projects, which otherwise lies idle much of the time.
See Also
References
- ↑ Definition - What does Machine-to-Machine (M2M) mean? TEC India
- ↑ M2M Communication Architecture M.J. Booysen, J.S. Gilmore, S. Zeadally, and G.-J.van Rooyen
- ↑ Key Features of Mission Critical M2M Communications Motorola
- ↑ How IoT Devices Help Run an M2M Economy Investopedia
Further Reading
- M2M Traffic Characteristics - When machines participate in communication Anders Orrevad
