Difference between revisions of "Risk Management Framework (RMF)"
| Line 1: | Line 1: | ||
| − | + | The '''Risk Management Framework (RMF)''' is a set of criteria that dictate how United States government IT systems must be architected, secured, and monitored. Originally developed by the Department of Defense (DoD), the RMF was adopted by the rest of the US federal information systems in 2010. The RMF is maintained by the National Institute of Standards and Technology (NIST), and provides a solid foundation for any data security strategy.<ref>Defining Risk Management Framework [https://www.varonis.com/blog/risk-management-framework/ Varonis]</ref> | |
| − | The risk-based approach to security control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, Executive Orders, policies, standards, or regulations. The following activities related to managing organizational risk (also known as the Risk Management Framework) are paramount to an effective information security program and can be applied to both new and legacy information systems within the context of the system development life cycle and the Federal Enterprise Architecture: | + | NIST Special Publication 800-37, "Guide for Applying the Risk Management Framework to Federal Information Systems", developed by the Joint Task Force Transformation Initiative Working Group, transforms the traditional Certification and Accreditation (C&A) process into the six-step Risk Management Framework (RMF). The Risk Management Framework (RMF), provides a disciplined and structured process that integrates information security and risk management activities into the system development life cycle.<ref>What is the Risk Management Framework [https://en.wikipedia.org/wiki/Risk_management_framework Wikipedia]</ref> |
| + | |||
| + | |||
| + | '''Risk Management Framework (RMF) Steps<ref>Risk Management Framework (RMF) Steps [http://csrc.nist.gov/groups/SMA/fisma/framework.html NIST]</ref><br />''' | ||
| + | The risk-based approach to security control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, Executive Orders, policies, standards, or regulations. The following activities related to managing organizational risk (also known as the Risk Management Framework) are paramount to an effective information security program and can be applied to both new and legacy information systems within the context of the system development life cycle and the [[Federal Enterprise Architecture Framework (FEA)|Federal Enterprise Architecture]]: | ||
Step 1: Categorize | Step 1: Categorize | ||
| Line 19: | Line 23: | ||
Step 6: Monitor | Step 6: Monitor | ||
| − | Monitor and assess selected security controls in the information system on an ongoing basis including assessing security control effectiveness, documenting changes to the system or environment of operation, conducting security impact analyses of the associated changes, and reporting the security state of the system to appropriate organizational officials | + | Monitor and assess selected security controls in the information system on an ongoing basis including assessing security control effectiveness, documenting changes to the system or environment of operation, conducting security impact analyses of the associated changes, and reporting the security state of the system to appropriate organizational officials |
| Line 40: | Line 44: | ||
[[Risk Maturity]]<br /> | [[Risk Maturity]]<br /> | ||
[[Risk Maturity Model (RMM)]]<br /> | [[Risk Maturity Model (RMM)]]<br /> | ||
| − | [[Risk Mitigation]] | + | [[Risk Mitigation]]<br /> |
| + | [[Enterprise Architecture]]<br /> | ||
| + | [[Federal Enterprise Architecture Framework (FEA)]]<br /> | ||
| + | [[IT Governance]]<br /> | ||
| + | [[IT Governance Framework]] | ||
Revision as of 19:37, 20 March 2020
The Risk Management Framework (RMF) is a set of criteria that dictate how United States government IT systems must be architected, secured, and monitored. Originally developed by the Department of Defense (DoD), the RMF was adopted by the rest of the US federal information systems in 2010. The RMF is maintained by the National Institute of Standards and Technology (NIST), and provides a solid foundation for any data security strategy.[1]
NIST Special Publication 800-37, "Guide for Applying the Risk Management Framework to Federal Information Systems", developed by the Joint Task Force Transformation Initiative Working Group, transforms the traditional Certification and Accreditation (C&A) process into the six-step Risk Management Framework (RMF). The Risk Management Framework (RMF), provides a disciplined and structured process that integrates information security and risk management activities into the system development life cycle.[2]
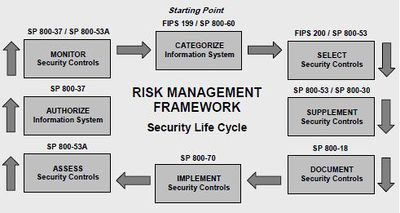
Risk Management Framework (RMF) Steps[3]
The risk-based approach to security control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, Executive Orders, policies, standards, or regulations. The following activities related to managing organizational risk (also known as the Risk Management Framework) are paramount to an effective information security program and can be applied to both new and legacy information systems within the context of the system development life cycle and the Federal Enterprise Architecture:
Step 1: Categorize Categorize the information system and the information processed, stored, and transmitted by that system based on an impact analysis.
Step 2: Select Select an initial set of baseline security controls for the information system based on the security categorization; tailoring and supplementing the security control baseline as needed based on organization assessment of risk and local conditions.
Step 3: Implement Implement the security controls and document how the controls are deployed within the information system and environment of operation.
Step 4: Assess Assess the security controls using appropriate procedures to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system.
Step 5: Authorize Authorize information system operation based upon a determination of the risk to organizational operations and assets, individuals, other organizations and the Nation resulting from the operation of the information system and the decision that this risk is acceptable.
Step 6: Monitor Monitor and assess selected security controls in the information system on an ongoing basis including assessing security control effectiveness, documenting changes to the system or environment of operation, conducting security impact analyses of the associated changes, and reporting the security state of the system to appropriate organizational officials
source: [1]
See Also
Risk Analysis
Risk Assessment Framework (RAF)
Risk Management
Risk Assessment
Information Technology Risk (IT Risk)
Enterprise Risk Management (ERM)
Risk IT Framework
Risk Based Testing
Risk-Adjusted Return
Risk-Adjusted Return on Capital (RAROC)
Risk Matrix
Risk Maturity
Risk Maturity Model (RMM)
Risk Mitigation
Enterprise Architecture
Federal Enterprise Architecture Framework (FEA)
IT Governance
IT Governance Framework
References