Difference between revisions of "Personally Identifiable Information (PII)"
| Line 4: | Line 4: | ||
[[File:PII.png|300px|Personally Identifiable Information (PII)]]<br /> | [[File:PII.png|300px|Personally Identifiable Information (PII)]]<br /> | ||
source: Imperva | source: Imperva | ||
| + | |||
| + | |||
| + | '''PII Security Controls<ref>PII Security Controls [https://www.imperva.com/learn/data-security/personally-identifiable-information-pii/ Imperva]</ref>'''<br /> | ||
| + | The Data Privacy Framework should define which security controls the organization needs to have in place to prevent data loss or data leak: | ||
| + | *[[Change Management]]: tracking and auditing changes to configuration on [[Information Technology (IT)|IT]] systems which might have security implications, such as adding/removing user accounts. | ||
| + | *[[Data Loss Prevention (DLP)|Data Loss Prevention]]: implementing systems that can track sensitive data transferred within the [[Organization|organization]] or outside it, and identify unnatural patterns that might suggest a breach. | ||
| + | *[[Data Masking|Data masking]]: ensuring that data is stored or transmitted with the minimal required details for the specific transaction, with other details masked or omitted. | ||
| + | *Ethical walls: implementing screening mechanisms to prevent certain departments or individuals within an organization from viewing PII that is not relevant to their work, or that might create a [[Conflict of Interest|conflict of interest]]. | ||
| + | *Privileged user monitoring: monitoring all privileged access to files and [[Database (DB)|databases]], user creation and newly granted privileges, blocking and alerting when suspicious activity is detected. | ||
| + | *Sensitive data access auditing: in parallel to monitoring activities by privileged users, monitoring and auditing all access to sensitive data, blocking and alerting on suspicious or anomalous activity. | ||
| + | *Secure [[Audit Trail|audit trail]] archiving: ensuring that any activity conducted on or in relation to PII is audited and retained for a period of 1-7 years, for legal or [[Compliance|compliance]] purposes, and also to enable forensic investigation of security incidents. | ||
| + | *User rights management: identifying excessive, inappropriate, or unused user privileges and taking corrective action, such as removing user accounts that have not been used for several months. | ||
| + | *User tracking: implementing ways of tracking user activity, online and while using organizational systems, to identify negligent exposure of sensitive data, compromise of user accounts, or malicious insiders. | ||
Revision as of 19:58, 17 February 2021
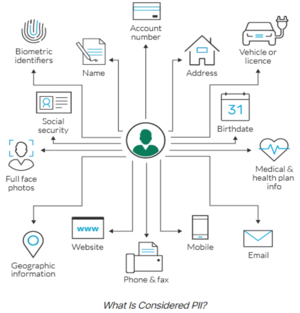
Personally Identifiable Information (PII) is any data that can be used to identify a specific individual. Social Security numbers, mailing or email address, and phone numbers have most commonly been considered PII, but technology has expanded the scope of PII considerably. It can include an IP address, login IDs, social media posts, or digital images. Geolocation, biometric, and behavioral data can also be classified as PII. This broad definition of PII creates security and privacy challenges, especially when specific and stringent safeguards for it are spelled out in regulations such as the European Union’s (EU’s) General Data Protection Regulation (GDPR).[1]
PII Security Controls[2]
The Data Privacy Framework should define which security controls the organization needs to have in place to prevent data loss or data leak:
- Change Management: tracking and auditing changes to configuration on IT systems which might have security implications, such as adding/removing user accounts.
- Data Loss Prevention: implementing systems that can track sensitive data transferred within the organization or outside it, and identify unnatural patterns that might suggest a breach.
- Data masking: ensuring that data is stored or transmitted with the minimal required details for the specific transaction, with other details masked or omitted.
- Ethical walls: implementing screening mechanisms to prevent certain departments or individuals within an organization from viewing PII that is not relevant to their work, or that might create a conflict of interest.
- Privileged user monitoring: monitoring all privileged access to files and databases, user creation and newly granted privileges, blocking and alerting when suspicious activity is detected.
- Sensitive data access auditing: in parallel to monitoring activities by privileged users, monitoring and auditing all access to sensitive data, blocking and alerting on suspicious or anomalous activity.
- Secure audit trail archiving: ensuring that any activity conducted on or in relation to PII is audited and retained for a period of 1-7 years, for legal or compliance purposes, and also to enable forensic investigation of security incidents.
- User rights management: identifying excessive, inappropriate, or unused user privileges and taking corrective action, such as removing user accounts that have not been used for several months.
- User tracking: implementing ways of tracking user activity, online and while using organizational systems, to identify negligent exposure of sensitive data, compromise of user accounts, or malicious insiders.