Access Control Facility (ACF2)
Access Control Facility or ACF2 (more formally, CA-ACF2) is a set of programs from Computer Associates that enable [security on mainframes. ACF2 prevents accidental or deliberate modification, corruption, mutilation, deletion, or viral infection of files. With ACF2, access to a system is denied to unauthorized personnel. Any authorized or unauthorized attempt to gain access is logged. System status can be monitored on a continuous basis, and a permanent usage log can be created. The logging feature, besides helping to identify potential intruders, makes it possible to identify and analyze changes and trends in the use of the system. Settings can be changed on a moment's notice, according to current or anticipated changes in the security or business requirements of the organization using the system.[1]
ACF2 (Access Control Facility 2) is a commercial, discretionary access control software security system developed for the MVS (z/OS today), VSE (z/VSE today) and VM (z/VM today) IBM mainframe operating systems by SKK, Inc. Barry Schrager, Eberhard Klemens, and Scott Krueger combined to develop ACF2 at London Life Insurance in London, Ontario in 1978. The "2" was added to the ACF2 name by Cambridge Systems (who had the North American marketing rights for the product) to differentiate it from the prototype, which was developed by Schrager and Klemens at the University of Illinois—the prototype name was ACF. The "2" also helped to distinguish the product from IBM's ACF/VTAM. ACF2 was developed in response to IBM's RACF product (developed in 1976), which was IBM's answer to the 1974 SHARE Security and Data Management project's requirement whitepaper. ACF2's design was guided by these requirements, taking a resource-rule oriented approach. Unique to ACF2 were the concepts of "Protection by Default" and resource pattern masking. As a result of the competitive tension between RACF and ACF2, IBM matured the SAF (Security Access Facility) interface in MVS (now z/OS), which allowed any security product to process operating system ("OS"), third-party software and application security calls, enabling the mainframe to secure all facets of mainframe operations. SKK and ACF2 were sold to UCCEL Corporation in 1986, which in turn was purchased by Computer Associates International, Inc. in 1987. Broadcom Inc. now (2019) markets ACF2 as CA ACF2.[2]
ACF2 has five different operation modes:[3]
- Quiet Mode - Only data set rules are disabled.
- Rule Mode - Individual access rules are defined.
- Log Mode - Access is permitted but still logged.
- Abort Mode - This is the default mode where ACF2 bars access, logs, and issues messages.
- Warn Mode - Access is allowed but issues warnings.
CA-ACF2 MVS[4]
CA-ACF2 MVS provides comprehensive data security functions for the IBM z/OS operating system. CA-ACF2 MVS protects all data and installation-defined resources by default, sharing data only when explicitly requested to by the owner of the data or by a security officer. CA-ACF2 MVS differs from other security systems that force you to define what is to be protected, rather than what is to be shared.
Model 204 CA-ACF2 MVS Interface
The Model 204 CA-ACF2 MVS Interface provides for an orderly migration from Model 204 security to CA-ACF2 security and allows an installation to use a combination of either or both security methods. The interface provides the tools and instructions needed to:
- Define Model 204 as a CA-ACF2 Multiuser Single Address Space System (MUSASS)
- Define the meaning of Model 204 user privileges
- Define CA-ACF2 Generalized Resource Rules for CA-ACF2 authorization of Model 204 user login privileges
- Define an installation default user priority class or the offset of a priority class byte within the user’s CA-ACF2 Logonid record
- Define the offset and length of a default login account within a CA-ACF2 Logonid record, and provide account authorization services
- Define the offset and bit within the CA-ACF2 Logonid record that determines whether or not a user can log in to a particular Model 204 job
- Define the offset and length within the CA-ACF2 Logonid record that contains data to be used as the user’s record security key field
- Activate the external CA-ACF2 Interface security mechanism
In summary, the CA-ACF2 MVS Interface provides all the facilities an installation site needs to implement CA-ACF2 security within the Model 204 environment.
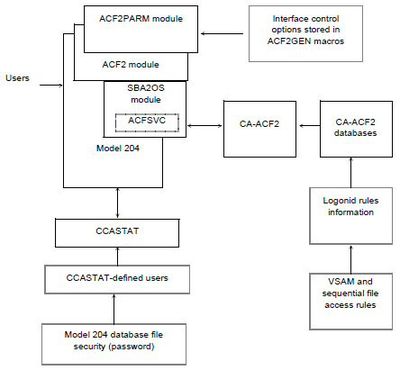
CA-ACF2 MVS Interface components
The following figure illustrates the components of the CA-ACF2 MVS Interface, which consists of:
- Model 204
- ACF2 Interface module, which is linked into Model 204
- ACF2PARM module, which can be linked with Model 204 or loaded dynamically at initialization
- SBA20S module, which is linked into Model 204 and contains the ACFSVC macro that invokes the CA-ACF2 SVC
- Model 204 system file, CCASTAT, which contains user IDs subject to Model 204 security
- CA-ACF2 MVS, which retrieves data from its VSAM databases and returns it to Model 204 for processing
References
- ↑ definition - What is Access Control Facility (ACF2)? Techtarget
- ↑ Explaining ACF2 Wikipedia
- ↑ What are the operation modes of ACF2? techopedia
- ↑ CA-ACF2 MVS Rocket Software