Active Directory
Active Directory is an advanced, hierarchical network directory service that comes with Windows servers and is used for managing permissions and user access to network resources. Introduced in Windows 2000, Active Directory is a domain-based network that is structured like the Internet's Domain Naming System (DNS). Using the LDAP directory access protocol, a company's workgroups (departments, sections, offices, etc.) are assigned domain names similar to Web addresses, and any LDAP-compliant Windows, Mac, Unix, or Linux client can access them. Active Directory can function in a heterogeneous, enterprise network and encompass other directories including NDS and NIS+. Cisco supports Active Directory in its IOS router operating system.[1]
Active Directory, like many information-technology efforts, originated out of a democratization of design using Requests for Comments or RFCs. The Internet Engineering Task Force (IETF), which oversees the RFC process, has accepted numerous RFCs initiated by widespread participants. Active Directory incorporates decades of communication technologies into the overarching Active Directory concept and then makes improvements upon them. For example, LDAP underpins Active Directory. Also, X.500 directories and the Organizational Unit preceded the Active Directory concept that makes use of those methods. The LDAP concept began to emerge even before the founding of Microsoft in April 1975, with RFCs as early as 1971. RFCs contributing to LDAP include RFC 1823 (on the LDAP API, August 1995), RFC 2307, RFC 3062, and RFC 4533. Microsoft previewed Active Directory in 1999, released it first with Windows 2000 Server edition, and revised it to extend functionality and improve administration in Windows Server 2003. Additional improvements came with subsequent versions of Windows Server. In Windows Server 2008, additional services were added to Active Directory, such as Active Directory Federation Services. The part of the directory in charge of the management of domains, which was previously a core part of the operating system, was renamed Active Directory Domain Services (ADDS) and became a server role like others. "Active Directory" became the umbrella title of a broader range of directory-based services. According to Bryon Hynes, everything related to identity was brought under Active Directory's banner.[2]
Active Directory provides the following network services:
- Lightweight Directory Access Protocol (LDAP) – An open standard used to access other directory services
- Security service using the principles of Secure Sockets Layer (SSL) and Kerberos-based authentication
- Hierarchical and internal storage of organizational data in a centralized location for faster access and better network administration
- Data availability in multiple servers with concurrent updates to provide better scalability
Active Directory is internally structured with a hierarchical framework. Each node in the tree-like structure is referred to as an object and associated with a network resource, such as a user or service. Like the database topic schema concept, the Active Directory schema is used to specify attributes and types for a defined Active Directory object, which facilitates searching for connected network resources based on assigned attributes. For example, if a user needs to use a printer with color printing capability, the object attribute may be set with a suitable keyword, so that it is easier to search the entire network and identify the object's location based on that keyword. A domain consists of objects stored in a specific security boundary and interconnected in a tree-like structure. A single domain may have multiple servers – each of which is capable of storing multiple objects. In this case, organizational data is stored in multiple locations, so a domain may have multiple sites for a single domain. Each site may have multiple domain controllers for backup and scalability reasons. Multiple domains may be connected to form a Domain Tree, which shares a common schema, configuration, and global catalog (used for searching across domains). A Forest is formed by a set of multiple and trusted domain trees and forms the uppermost layer of the Active Directory. Novell's directory service, an Active Directory alternative, contains all server data within the directory itself, unlike Active Directory.[3]
Active Directory (AD) allows for the centralization of user and computer management, as well as the centralization of resource access and usage. In a situation where there are 50 users in an office. If each user were to have their own login to each computer, one would have to configure 50 local user accounts on each PC. With AD, the user account is created only once and it can log into any PC on the domain by default. If one wanted to harden security, it would have to be done 50 times. Similarly in a situation where file share was allowed to only half of those people, without AD, one would need to replicate their username and passwords manually on the server to give seamless access or have to make a shared account and give each user the username and password. Active Directory also provides the ability to use Group Policy. Group Policy is a set of objects that are linked to OUs that define settings for users and/or computers in those OUs. For example, if you want to make it so that "Shutdown" isn't on the start menu for 500 lab PCs, you can do that in one setting in Group Policy. Instead of spending hours or days configuring the proper registry entries, a Group Policy Object is created and linked to the correct OU or OUs. There are hundreds of GPOs that can be configured, and the flexibility of Group Policy is one of the major reasons that Microsoft is so dominant in the enterprise market.[4]
Composition of an Active Directory[5]
Most Active Directory installations have a few distinct parts that all work together:
- a directory database that stores the actual directory information
- a Kerberos key distribution center that helps manage user passwords and other security resources
- a DNS server, which maps IP addresses to hostnames and back
- a DHCP server, which grants dynamic IP addresses to hosts as they join the network
- one or more Global Catalogs, which cache parts of the directory database and help speed up some common queries
Also, Active Directory is designed in such a way that it can be run on multiple computers at the same time, which coordinates between themselves to ensure that their data is always consistent; this process is called “replication”.
Active Directory is subdivided into one or more domains.[6]
A domain is a security boundary. Each domain is hosted by a server computer called a domain controller (DC). A domain controller manages all of the user accounts and passwords for a domain.
- Domains and the Domain Name System (DNS): Domains are named using the Domain Name System (DNS). If your company is called ACME Corporation your DNS name would be (for example) acme.com. This is the top-level domain name for your company. The security domain in Active Directory maps directly to the DNS domain name.
- For larger organizations you can subdivide Active Directory into child domains (based on geography for example). If ACME Corporation has three divisions named West, Central, and East, the sub-domains can have the DNS names west.acme.com, central.acme.com, and east.acme.com. Each domain requires a server computer. In the above scenario you would need at least four servers to host Active Directory as follows:
- acme.com
- west.acme.com
- central.acme.com
- east.acme.com
How an Active Directory Works[7]
An Active Directory performs a variety of tasks which include providing information on objects such as hardware and printers and services for the end users on the network such as Web email and other applications.
- Network Objects: Network objects are anything that is associated with the network such as a printer, end-user applications, and security applications that are implemented by the network administrator. Network objects can also contain additional objects within their file structure which are identified by a folder name. Each object has its own unique identification by the specific information that is contained within the object.
- Schemas: Since network objects, each has their own identity which is also known as a characterization schema, the type of identification is the determining factor as to how each object will be used on the network.
- Hierarchy: The hierarchal structure determines how each object can be viewed within the hierarchy which consists of three different levels which are known as a forest, tree, and domain with the forest being the highest level that allows the network administrator to see all of the objects in the active directory. The trees are the second level of the hierarchy each of which can hold multiple domains.
What Does Active Directory Look Like?[8]
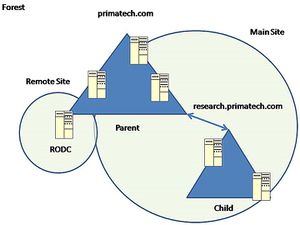
From a physical perspective, Active Directory allows you to group computers (both workstations and servers) into sites. A site typically includes a single subnet or subnets all located within the same physical area. So you might have two offices, one in New York, and one in Los Angeles. You should, by rights, have two different sites. But going beyond that, you might have multiple subnets in New York due to the size of that location. You can break that physical location into multiple sites as well (or keep them under one site). Active Directory has been designed to allow for that level of flexibility so that the final design decisions aren’t forced upon the administrative team. Those sites are helpful because they curtail the amount of replication that occurs between those sites and that gives you the ability to control the amount of bandwidth that is utilized for replication traffic that might be caused by Active Directory itself. Beyond the physical side, however, there is also the logical side, which allows for even more flexibility in your design of Active Directory objects. Forests, domains, Organizational Units—this is the lingo of logical Active Directory. A forest contains trees, of course (Figure below). You can see in the Figure below that in this case, a tree is called a domain. There is a parent domain and there can be sub-domains, called child domains. So you might have a forest with a single domain tree (albeit this would be a very small forest) or you might have multiple domains with multiple child domains all interconnected by transitive two-way trusts.
If your office used Active Directory, all of the machines would be connected to a domain, which means all of the information is stored in a central location, not locally on the individual computers’ hard drives. The domain is controlled by a global catalog, which keeps track of all of the devices that are registered to the network. The global catalog stores the IP addresses, computer names, and users, so that the global administrator can oversee everything that happens on the domain. In order to access someone else’s computer, a user would just need that computer’s name, because everything is already linked on the back end. When you’re using Active Directory, everything is already permission from the domain controller. This means that the network administrator has already told the domain controller what permissions to assign to each user. This makes all digital communication more efficient, because everything is easily accessible, and information is readily available.[9]
Security[10]
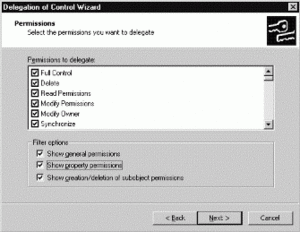
Active Directory plays an important role in the future of Windows networking. Administrators must be able to protect their directories from attackers and users while delegating tasks to other administrators where necessary. This is all possible using the Active Directory security model, which associates an access control list (ACL) with each container, object, and object attribute within the directory. The figure below shows a step from the Delegation Of Control wizard, a helpful utility for assigning permissions to Active Directory objects.
See Also
References
- ↑ Definition of Active Directory
- ↑ History of Active Directory
- ↑ Active Directory Explained
- ↑ The Need for Active Directory
- ↑ What is Active Directory composed of?
- ↑ What is Active Directory?
- ↑ How does an Active Directory Work?
- ↑ What Does Active Directory Look Like?
- ↑ Why Companies Need Active Directory?
- ↑ Active Directory - Security
Further Reading
- Active Directory Fundamentals
- Knowledge Base Articles with Information on Microsoft Active Directory
- Structure of Active Directory
- Virtualizing Active Directory Domain Services On VMware vSphere®
- Active Directory network protocols and traffic
- Beyond the MCSE: Active Directory for the Security Professional