Information Security Management System (ISMS)
Definition of Information Security Management System (ISMS)
An ISMS is a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes, and IT systems by applying a risk management process. It can help small, medium, and large businesses in any sector keep information assets secure.[1]
The Information Security Management System (ISMS) represents the collation of all the interrelated/interacting information security elements of an organization so as to ensure policies, procedures, and objectives can be created, implemented, communicated, and evaluated to better guarantee an organization's overall information security. This system is typically influenced by the organization's needs, objectives, security requirements, size, and processes. An ISMS includes and lends to effective risk management and mitigation strategies. Additionally, an organization's adoption of an ISMS largely indicates that it is systematically identifying, assessing, and managing information security risks and "will be capable of successfully addressing information confidentiality, integrity, and availability requirements." However, the human factors associated with ISMS development, implementation, and practice (the user domain) must also be considered to ensure the ISMS' ultimate success.[2]
Elements of an ISMS[3]
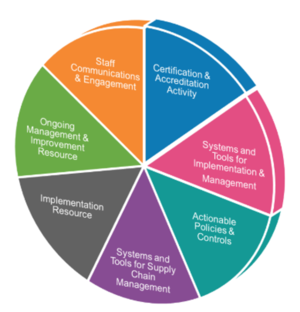
An effective Information Security Management System is made up of 7 elements, as shown in the pie chart below.
The real size of these pie slices, in terms of time and cost, depends on your objectives, your starting point, the scope you want to include in your ISMS, and your organization’s preferred way of working.
Investing well in one slice will help reduce or avoid much larger investments in the other slices. But beware of the pitfalls, such as following the cheap ISO 27001 documentation toolkit route, as it will cost you much more in the long run, and you’ll fail to demonstrate the ‘management system’ aspects of your ISMS too.
ISMS Frameworks[4]
- ISO 27001 is a leader in information security, but other frameworks offer valuable guidance as well. These other frameworks often borrow from ISO 27001 or other industry-specific guidelines.
- ITIL (Information Technology Infrastructure Library), the widely adopted ITSM framework, has a dedicated component called Information Security Management (ISM). The goal of ISM is to align IT and business security to ensure InfoSec is effectively managed in all activities.
- COBIT (Control Objectives for Information and Related Technology), another IT-focused framework, spends significant time on how asset management and configuration management are foundational to information security as well as nearly every other ITSM function—even those unrelated to InfoSec.
What Should an ISMS Framework Address[5]
ITIL suggests that your ISMS should address what it calls “The Four P’s”: people, process, products and technology, and partners and suppliers. Many global IT organizations seek global certification for their ISMS frameworks, which is done through ISO 27001. Typically, an ISMS framework addresses five key elements:
- Control: You should establish a management framework for managing information security, preparing and implementing an Information Security Policy, allocating responsibilities, and establishing and controlling documentation.
- Plan: In the planning phase of the framework, you will be responsible for gathering and fully understanding the security requirements of the organization — then recommending the appropriate measures to take based on budget, corporate culture around security, and other factors.
- Implement: Next, you’ll put the plan into action, making sure that you have the proper safeguards in place to properly enact and enforce your Information Security Policy in the process.
- Evaluate: Once your policies and plans are in place, you need to properly oversee them to ensure that your systems are truly secure and your processes are running in compliance with your policies, SLAs, and other security requirements.
- Maintain: Finally, an effective ISMS means you are continuously improving the entire process — looking for opportunities to revise SLAs, security agreements, the way you monitor and control them, and more.
ISMS Security Controls[6]
ISMS security controls span multiple domains of information security as specified in the ISO 27001 standard. The catalog contains practical guidelines with the following objectives:
- Information security policies. An overall direction and support help establish appropriate security policies. The security policy is unique to your company, devised in the context of your changing business and security needs.
- Organization of information security. This addresses threats and risks within the corporate network, including cyberattacks from external entities, inside threats, system malfunctions, and data loss.
- Asset management. This component covers organizational assets within and beyond the corporate IT network., which may involve exchanging sensitive business information.
- Human resource security. Policies and controls pertaining to your personnel, activities, and human errors, including measures to reduce risk from insider threats and workforce training to reduce unintentional security lapses.
- Physical and environmental security. These guidelines cover security measures to protect physical IT hardware from damage, loss, or unauthorized access. While many organizations are taking advantage of digital transformation and maintaining sensitive information in secure cloud networks off-premise, the security of physical devices used to access that information must be considered.
- Communications and operations management. Systems must be operated with respect and maintenance to security policies and controls. Daily IT operations, such as service provisioning and problem management, should follow IT security policies and ISMS controls.
- Access control. This policy domain deals with limiting access to authorized personnel and monitoring network traffic for anomalous behavior. Access permissions relate to both digital and physical mediums of technology. The roles and responsibilities of individuals should be well defined, with access to business information available only when necessary.
- Information system acquisition, development, and maintenance. Security best practices should be maintained across the entire lifecycle of the IT system, including the phases of acquisition, development, and maintenance.
- Information security and incident management. Identify and resolve IT issues in ways that minimize the impact to end users. In complex network infrastructure environments, advanced technology solutions may be required to identify insightful incident metrics and proactively mitigate potential issues.
- Business continuity management. Avoid interruptions to business processes whenever possible. Ideally, any disaster situation is followed immediately by recovery and procedures to minimize damage.
- Compliance. Security requirements must be enforced per regulatory bodies.
- Cryptography. Among the most important and effective controls to protect sensitive information, it is not a silver bullet on its own. Therefore, ISMS governs how cryptographic controls are enforced and managed.
- Supplier relationships. Third-party vendors and business partners may require access to the network and sensitive customer data. It may not be possible to enforce security controls on some suppliers. However, adequate controls should be adopted to mitigate potential risks through IT security policies and contractual obligations.
Implementing an ISMS[7]
There are numerous ways of approaching the implementation of an ISMS. The most common method to follow is a ‘Plan Do Check Act’ process. The international standard detailing the requirements for implementing an ISMS, ISO 27001, and the best-practice guidelines contained in ISO 27002, serve as two excellent guides to get you started implementing an ISMS. A certified ISMS, independently audited by an approved certification body, can serve as the necessary reassurance to customers and potential clients that the organization has taken the necessary steps to protect their personal and confidential data from a range of identified risks.
The strength of an ISMS is based on the robustness of the information security risk assessment, which is key to any implementation. The ability to recognize the full range of risks that the organization and its data may face in the foreseeable future is a precursor to implementing the necessary mitigating measures (known as ‘controls’).
ISO 27001 provides a list of recommended controls that can serve as a checklist to assess whether you have considered all the controls necessary for legislative, business, contractual, or regulatory purposes.
Principles of an Information Security Management System[8]
While the implementation of an ISMS will vary from organization to organization, there are underlying principles that all ISMS must abide by in order to be effective at protecting an organization’s information assets. These principles – a few of which are mentioned below – will help guide you on the road to ISO/IEC 27001 certification.
The first step in successfully implementing an ISMS is making key stakeholders aware of the need for information security. Without buy-in from the people who will implement, oversee, or maintain an ISMS, it will be difficult to achieve and maintain the level of diligence needed to create and maintain a certified ISMS.
In order for an organization’s ISMS to be effective, it must analyze the security needs of each information asset and apply appropriate controls to keep those assets safe. Not all information assets need the same controls, and there is no silver bullet for information security. Information comes in all shapes and sizes, as do the controls that keep your information safe.
Implementing an ISMS is not a project with a fixed length. To keep an organization safe from threats to your information, an ISMS must continually grow and evolve to meet the rapidly changing technical landscape. Therefore, continual reassessment of an Information Security Management System is a must. By frequently testing and assessing an ISMS, an organization will know whether their information is still protected or if modifications need to be made.
ISMS Implementation Steps[9]
Organizations can benefit significantly from implementing an ISMS, achieving compliance with ISO 27001, and ensuring the security of their informational assets. Still, a thorough implementation and training process is required to derive the complete benefits of the ISMS. Here's how to start implementing ISMS in your organization:
- Step One: Asset Identification and Valuation: The first step to implementing an ISMS is to identify the assets that must be protected and determine their relative value to the organization. Remember, a risk-based ISMS considers the relative importance of different types of data and devices and protects them accordingly. In this step, organizations collect data from documentation to identify business-critical IT assets and their relative importance to the organization. Organizations must create a Statement of Sensitivity (SoS) that assigns a rating to each of its IT assets across three separate dimensions— confidentiality, integrity, and availability:
- Confidentiality - ensuring that the information is exclusively accessible to authorized persons only
- Integrity - ensuring that the information to be secured is accurate and complete and that information and processing methods are safeguarded
- Availability - ensuring that authorized persons have access to the protected information and assets when needed
Organizations must strike a balance between securing assets and making them accessible to authorized persons that may need the data to do their jobs.
- Step Two: Conduct a Detailed Risk Assessment: Once asset identification and valuation have been completed and the organization has formulated an SoS, it's time to conduct a detailed risk assessment that will inform the production of the ISMS. A risk assessment analysis includes four important steps for determining how the IT asset should be protected:
- Threats - The organization should analyze the threats to the asset by documenting any unwanted events that could result in either deliberate or accidental misuse, loss, or damage of the assets.
- Vulnerabilities - Threats are a concrete description of what could happen, and vulnerabilities measure how susceptible the IT asset could be to the threats identified in the first part of the analysis. This is where you start to differentiate between different types of assets—while a malicious software attack is a threat for servers, laptops, and phones, we might indicate here that phones are more vulnerable to the threat because they will be used remotely and might be connected to several external networks. In contrast, servers will be kept in-house and monitored around the clock.
- Impact and Likelihood - The organization can now assess the likelihood of certain types of breaches occurring along with the magnitude of the potential damage resulting from each type of data breach. Organizations can use a cost-benefit analysis to help them target the most potentially damaging breaches with the most aggressive security measures.
- Mitigation - Finally, the organization proposes methods for minimizing the recognized threats, vulnerabilities, and impacts through policies and procedures in the ISMS.
- Step Three: Establish the ISMS: Now that the organization has identified the assets to be protected and conducted a full risk assessment, it can proceed to write the actual policies and procedures that comprise the ISMS. Organizations should establish the ISMS in compliance with ISO 27001 if they wish to earn a certification for best practices in information security management.
Taking the example of an unsecured business phone, what steps could the organization take to ensure that information on the phone is adequately protected in case the phone is lost or stolen? Here are some sample policies that could be implemented to help mitigate the risk:- Lost or stolen phones must be reported to the IT department within eight hours. If you do not know where your phone is, contact IT immediately.
- IT must be able to remotely track and wipe any phone owned by the company.
- Company phones must be protected by a biological password corresponding to the assignee—a fingerprint, retina scan, or facial recognition technology must be used to unlock the phone.
- Company phones are issued with a secure waist holster, encouraging employees to avoid losing the asset by securing it to their person when not in use.
This set of policies and procedures would minimize the possibility of a data breach occurring due to a lost phone. The requirement of a biological password significantly increases the level of sophistication required to gain unauthorized access to the phone, the reporting requirements introduce additional accountability to the user of the phone, and IT is able to remove sensitive data from any phone that is reported missing.
Advantages of ISMS Certification[10]
Certification of ISMS brings several advantages;
- Provide a structured way of managing information security within an organization
- Provide an independent assessment of an organization’s conformity to the best practices agreed upon by a community of experts for ISMS.
- Provide evidence and assurance that an organization has complied with the standards required.
- Enhance information security governance within the organization.
- Enhance the organization’s global positioning and reputation.
- Increase the level of information security in the organization.
See Also
References
- ↑ Defining Information Security Management System (ISMS)?
- ↑ What is Information Security Management System (ISMS)?
- ↑ What’s included in an ISMS?
- ↑ ISMS Frameworks
- ↑ What Should an ISMS Framework Address
- ↑ ISMS Security Controls
- ↑ Implementing an ISMS
- ↑ Principles of an Information Security Management System
- ↑ How to Implement ISMS at Your Organization
- ↑ What are the advantages if my organization is ISMS certified?