Machine-to-Machine (M2M)
What is Machine-to-Machine (M2M) Communication?
Machine-to-Machine (M2M) communication is a form of data communication that involves one or more entities that do not necessarily require human interaction or intervention in the process of communication. M2M is also named as Machine Type Communication (MTC) in 3GPP. It is different from the current communication models in the ways that it involves:
- new or different market scenarios
- lower costs and effort
- a potentially very large number of communicating terminals
- little traffic per terminal, in general
M2M communication could be carried over mobile networks (e.g. GSM-GPRS, CDMA EVDO networks). In the M2M communication, the role of mobile network is largely confined to serve as a transport network. With a potential market of probably 50 million connected devices, M2M offers tremendous opportunities as well as unique challenges. These devices vary from highly-mobile vehicles communicating in real-time, to immobile meter-reading appliances that send small amounts of data sporadically.[1]
M2M technologies typically use sensors to capture data that is fed through networks, providing critical input to various types of machines that perform different tasks. Although a broad term, M2M usually refers to the use of these distributed systems to control industrial or manufacturing equipment. One such system is telemetry, which uses radio waves to facilitate this type of communication between devices. Those discussing the history of M2M systems may point to the evolution of new smart meter utility systems, automotive technologies and the integration of more intelligent networking systems with a broader variety of machines and appliances. The emergence of new models, like Web-distributed software, is also helping M2M technologies evolve and gain ground within manufacturing and industrial industries.[2]
Evolution of M2M Technology[3]
Most people are not aware of the fact that communication between devices in the form of machine-to-machine (M2M) systems is not a new phenomenon. This technology has existed for more than a century now and is an integral part of our workplace and personal lives. Evolution of machine-to-machine solutions has been steady and staggering at the same time. Starting with telemetry solutions in mid 1800s, M2M technology has made a massive leap into the IoT solutions of today. Here is a summary of the evolution phases of M2M systems.
Lifestyle of M2M technology
- Telemetry (1845 to 1990s)
The history of M2M systems began with use of data transmission systems by the Russian army in 1845. It was the most basic form of a wired data transfer network. It was followed by the invention of two-way radio networks in the 1900s. The technology fast moved from telephone lines to weather balloons to aerospace telemetry through the mid-90s. In 1973, IBM released its first main frame computers (IBM 3650 and 3660). This brought about a technology wave that gave us innovations like caller Ids (1968), electrical power consumption meters (1977), and single computer processing chips (1978).
- M2M systems (1990s to 2010)
Next generation of M2M technology was highlighted with the introduction of GSM data connectivity on mobile phones in 1995 (by Siemens). By 1997, wireless connectivity became mature and found countless applications varying from vending machines to telemedicine. RFID technology also became mainstream in the mid 1990s (although it had been in beta phase since 1970s). Evolution of machine-to-machine solutions based on analog connectivity had reached its prime by 2010 and the technology was ready for a digital revolution.
- Internet of Things (2010 to present)
The latest chapter in the history of M2M systems is what we have termed as the Internet of Things (IoT). The basic device connectivity principles remain the same but the technology is a lot more evolved. Cloud computing became prime time in 2012, which contributed significantly to the feasibility of today’s IoT solutions. 2013 and 2014 were the launch years for sensor-based IoT devices like thermostats and home lighting. With technology giants like Apple (introduced Homekit in 2014), Google, and Microsoft putting their weight behind the Internet of things, the future of M2M systems looks very bright. M2M systems are predicted to contribute up to 40% of the total data generated by the year 2020. And we are expecting a whopping 40-fold (50 billion to 2 trillion) increase in the numbers of machine sensors in the next few years. The limelight might be taken by the new-age term (Internet of Things) but M2M solutions will continue serving as the hardworking backbone of this technology.
Machine-to-Machine (M2M) Communication Architecture[4]
A generic M2M communication architecture is shown in Figure 1. To support the high number of M2M devices (billions to trillions) that are expected to be part of an M2M network, hierarchical communication architectures have been proposed. At the highest level, the goal of M2M architectures is to aggregate information from data collectors, and to apply some decision-making function to this information to produce decisions which are then executed. Several data collectors (e.g. temperature sensors, location sensors or heart rate monitors) are used to collect information from multiple locations. Data collectors gather data in areas that are small compared to the total area covered by the M2M architecture. The data collectors are usually separated in physical space and can collect information from various types of sources. For example, one data collector could record the ambient temperature in one location, and another could record the current consumed by a television set in another distant physical location.
Figure 1. Generic M2M communication architecture
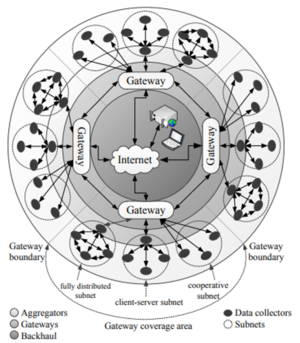
source: KSII
In M2M architectures, data collectors of the same type are connected to small networks (e.g. Body Area Networks (BANs), Zigbee, and Bluetooth), called subnets. Each subnet uses a network technology appropriate for the type of information to be collected and distributed. The network technology which is employed determines the subnet architecture. Three types of subnets (fully distributed, client-server and cooperative) are shown in Figure 1. In a fully distributed network, all nodes (e.g. various computers on a home Wi-Fi network) are connected as peers and share data amongst themselves. One of the nodes (e.g. a router’s Wi-Fi module) acts as a super-peer that has the ability to connect through some gateway (e.g. a router’s ADSL connection) to the Internet. In a client-server network, all clients onlycommunicate with the server; an example would be portable media players connecting to a media server. The server then relays appropriate information to other clients (e.g. wireless speakers). The server also has the ability to connect to the Internet through some gateway (e.g. a home router). A cooperative network is not, strictly speaking, a subnet. None of the nodes
(e.g. BAN sensors) communicate directly with each other as is the case on a subnet, but rather via the gateway (e.g. a cellular phone).
The collected data is then aggregated at possibly multiple layers of aggregation points. The number of aggregation layers depends on the expected number of M2M devices and how these devices are logically grouped. At each aggregation layer, data from multiple data collectors can be aggregated by applying some intelligence to the data. This means that the aggregation function is not merely assembling the data, but it can also reduce the amount of data retransmitted. This can be achieved, for example, through filtering data based on relevance, or by extracting higher-level information from aggregated data. Data aggregation is used to allow M2M devices to have low cost, consume little power and have a limited operating area. This is required to enable a system of billions to trillions of these devices.
Multiple local subnets using different communication standards can communicate with each other using some gateway which provides Internet connectivity or a similar backhaul network. The gateway typically interfaces with at least one device on each subnet to which it is connected, and is also connected to other gateways. An end-user can connect to a server to access information collected from the M2M data collectors. This server may be connected to the Internet or some other backhaul network. The function of the M2M server is to perform final processing tasks on the collected data, to store the data, log the transactions that occurred and to make the data available online to the various users of the M2M system.
How M2M Works[5]
The main purpose of machine-to-machine technology is to tap into sensor data and transmit it to a network. Unlike SCADA or other remote monitoring tools, M2M systems often use public networks and access methods -- for example, cellular or Ethernet -- to make it more cost-effective.
The main components of an M2M system include sensors, RFID, a Wi-Fi or cellular communications link, and autonomic computing software programmed to help a network device interpret data and make decisions. These M2M applications translate the data, which can trigger preprogrammed, automated actions.
One of the most well-known types of machine-to-machine communication is telemetry, which has been used since the early part of the last century to transmit operational data. Pioneers in telemetrics first used telephone lines, and later, radio waves, to transmit performance measurements gathered from monitoring instruments in remote locations.
The internet and improved standards for wireless technology have expanded the role of telemetry from pure science, engineering and manufacturing to everyday use in products such as heating units, electric meters and internet-connected devices, such as appliances.
Features of M2M Communications[6]
The most important features of an M2M Communication system are:
- Low Mobility: M2M devices do not move, move infrequently, or move only within a certain region.
- Application Independent: M2M devices enable communications to key applications that don’t have any communication today and are completely transparent to the application. The application is unaware that the communication service is provided by a wired or wireless connection. IP-based: As LMR communication networks migrate from analog to digital, these new digital networks support IP bearer services and have the ability to transport both IP and serial-based protocols over the IP-based network.
- Small Data Transmissions: M2M devices frequently send or receive small amounts of data, leveraging the extra capacity enabled by migrating to a new TDMA-based digital LMR network.
- High Reliability: High reliability means that whenever and wherever M2M communication is required or triggered, the connection and reliable transmission between the M2M device and the M2M server shall be available, regardless of the operating environment. High reliability is required in M2M applications that involve either the prospect of an emergency or highly sensitive data. Utility LMR systems have long been designed for high reliability for their voice needs, and the benefit of this is extended directly to the M2M applications that leverage the same network. Mission critical radio networks are designed for high reliability and redundancy where failure is not an option while business enterprise operations networks are not designed to meet the same redundancy and reliability specifications.
- Network Priority: Network priority means that there is a method for providing a hierarchical prioritization of users or applications within the solution when applications, voice or data, are competing for network access.The P25, TETRA and DMR standards and the systems provided by the manufacturers have provisions in their protocols to accommodate a prioritization scheme, whether it is simple or sophisticated. This is important as utilities have long considered their voice communications to be mission critical because they rely on them for both safety and security, such that prioritization cannot be disrupted. Many fixed data applications, which weren’t previously considered mission critical, are now being considered as such since the information about the water facility’s performance has a direct impact on a utility’s operation and performance.
- Security: Security functions include the protection and confidentiality of M2M data, authentication of users prior to access to M2M devices, and encryption of the data transferred across M2M networks. Knowing that utilities desire private LMR networks for their higher levels of security provides a strong platform that can be leveraged when using the same security for M2M applications.
- Latency Tolerant: Latency is a time interval between the stimulation and response. When leveraging a LMR network for M2M the target applications should be those that aren’t latency sensitive. The general one-way latency of an LMR network is approximately 1 second. Those polled applications or reports by exception-based applications that don’t require immediate responses measured in milliseconds but rather in seconds are target applications for M2M over LMR.
Applications of Machine 2 Machine Technology[7]
Basically, Machine 2 Machine communication is crucial for developing connection across all aspects of the physical world around us. Using this tool, business processes can be improved, business assets can be monitored in a more efficient manner and new revenues can be generated with ease.(see Figure 2.)
Figure 2. M2M Applications
source: IoTWorm
Some of the applications of Machine to Machine Technology include but are not limited to:
- Utility Companies: M2M communications help the utility companies in harvesting energy products, like oil, gas, etc. and in billing their customers. The remote sensors deployed in oil drilling sites collect regular data about the presence of oil at a particular field and send that data to a remote computer. They are also capable of sending information about the flow rates, temperature, pressure, fuel levels, etc. wirelessly to the remote computer.
- Traffic Control: Traffic Control is another common area where the use of M2M communication can be seen. A traffic system collects data related to the speed and volume of the traffic with the help of various sensors and sends this information across the computers that control the devices such as signals and lights. The cameras installed on the traffic signals also collect data about the vehicles not following the traffic rules and send pictures to the software which then sends challan receipts to the defaulters.
- Telemedicine: Another common area of application of M2M communications is Telemedicine. Heart patients wear special devices which monitor their heart rate. This data is sent to the implanted device which sends back shocks to the patient for correcting any errant rhythms in the heart beat.
- Inventory Management: Products are tagged with RFID tags which send signals to the computers and alert the retailer in case of a theft attempt. These tags also help the retailers to keep a track of their goods which are sold online in large quantities and have high chances of theft/shortage.
- Banking: Banking is another common area to make use of M2M. With an increase in the smartphone market, people have started making mobile payments for their purchases. They can deposit money into the bank, transfer money to other accounts and can even withdraw at their convenience. The mobile system is connected to the bank’s central system and updates the mobile transaction in the books as and when they happen. On the other hand, Banks can monitor the cash available in the ATMs and also the technical issues they are facing.
Today, M2M communication involves a network of personal and industrial devices talking with each other and it continues to grow. The industry is estimated to grow to $200 billion by 2022 and we believe M2M technology holds a bright future and the flexibility of this technology is certainly of great use in all kinds of businesses.
The Need for Machine 2 machine Communication[8]
For the idea of Internet of Things to become successful, it is very necessary for Machine 2 Machine communication to be used at a very large scale. With modern machines increasingly containing computers as well as other electronic devices for storing large amounts of information, there is need for these machines to have better connectivity as well as sharing capacity with all physical devices and objects around them. Basically, a machine can be anything with electrical, mechanical, environmental as well as electronic properties. All kinds of modern machines that we use at our home and workplace such as storage tanks, television sets, refrigerators, etc are a few common examples of Machine 2 Machine communication.
In order to carry out their tasks efficiently, these machines may also consist of inbuilt radios for retrieving as well as transmitting information. The use of such inbuilt radios makes sure that M2M communication is safe and efficient for all kinds of home, medical, industrial as well as business processes. As a result, when information is retrieved correctly, the operator will be able to interpret it more effectively and will be able to draw better conclusions.
Let us think about the scenario when there are no computers present inside the computers. In this case as well, machines can be attached with sensor radio devices for providing physical information across different devices. In such cases, there are chances that both the communicating devices can be far away from each other; hence there arises the need for routing the information. This is a straight indication that both point to point as well as point to multi- point communications are crucial for developing a M2M communication system.
In fact, electronic devices at your home and workplace are only able to communicate with each other due to this common networking designed between them known as the Machine 2 Machine communication.
IoT and the M2M Economy[9]
The processing power of such IoT devices and the heaps of data generated by them can be of great value.
For instance, an individual having a water purifier fitted in his home no longer needs to worry about the intricacies and step-by-step monitoring of the purifying process. Depending upon the hardness of the incoming water, the microprocessor-fitted purifier can schedule the purifying cycle and let the water be treated to a specified level of hardness. The same device can also be equipped with sensors to assess the residual quality of the purifying cartridge and is also capable of sending alerts to the service center to request a replacement.
Additionally, the data generated by such devices offers great value. It can assist in assessing consumption behavior and usage patterns and will also serves to inform macro-level tasks like city planning and assessing the quality and demand of water across a region. Additionally, device owners can willingly sell selected data points for monetary rewards.
Beyond such basic workings of the device and automated communication across a network comprised of installed devices, many blockchain-based projects are being launched to harness the power of such commonly used appliances. For instance, the processors and memory modules fitting in these IoT devices can be utilized for cryptocurrency mining and transaction authentication activities. Projects like IOTA, IoT Chain, and IOTW are attempting to harness the power and resources for their blockchain projects, which otherwise lies idle much of the time.
The Value Of M2M[10]
Growth in the M2M and IoT markets has been growing rapidly, and according to many reports, growth will continue. Strategy Analytics believes that low power, wide-area network (LPWAN) connections will grow from 11 million in 2014 to 5 billion in 2022. And IDC says the market for worldwide IoT solutions will go from $1.9 trillion in 2013 to $7.1 trillion in 2020.
Many big cell operators, like AT&T and Verizon, see this potential and are rolling out their own M2M platforms. Intel, PTC, and Wipro are are all marketing heavily in M2M and working to take advantage of this major industry growth spurt. But there is still a great opportunity for new technology companies to engage in highly automated solutions to help streamline processes in nearly any type of industry. We’re certain we’ll see a huge influx of companies who begin to innovate in this area in the next five years.
However, as the cost of M2M communication continues to decrease, companies must determine how they will create value for businesses and customers. In our mind, the opportunity and value for M2M doesn’t lie in the more traditional layers of the communication world. Cell carriers and hardware manufacturers, for example, are beginning to look into full-stack offerings that enable M2M and IoT product development. We strongly believe value lies in the application side of things, and the growth in this industry will be driven by smart applications from this point forward.
Issues and Concerns in M2M[11]
The key concerns in M2M are related to addressing and security.
The M2M System should be flexible in supporting more than one naming scheme. Also it should support identification of connected objects or groups of connected objects by their names, temporary id, pseudonym (i.e. different names for the same entity), location or combination thereof (e.g. URIs or IMSI). It shall be possible to reuse names for certain classes of devices or for devices operating in certain (i.e. resource constrained) environments. The addressing schemes should include:
- IP address of connected objects.
- IP address of group of connected objects (including multicast address).
- E.164 addresses of connected objects (e.g. MSISDN)
It is expected that M2M devices would typically operate unmanned and unguarded by humans and thus are subject to increased levels of security threats, such as physical tampering, hacking, unauthorized monitoring, etc. Terminal devices may also get geographically dispersed over time. Such M2M devices should therefore provide adequate security to detect and resist attacks. Devices may also need to support remote management including firmware updates to correct faults or recover from malicious attacks. Some M2M Equipments (M2Mes) are typically required to be small, inexpensive, able to operate unattended by humans for extended periods of time, and to communicate over the wireless area network (WAN) or WLAN. M2Mes are typically deployed in the field for many years, and after deployment, tend to require remote management of their functionality. It is likely that M2Mes will be deployed in very large quantities, and many of them will also be mobile, making it unrealistic or impossible for operators or subscribers to send personnel to manage or service them. These requirements introduce a number of unique security vulnerabilities for the M2Mes and the wireless communication networks over which they communicate.
Open Initiatives in M2M[12]
- Eclipse machine to machine industry working group (open communication protocols, tools, and frameworks), the umbrella of various projects including Koneki, Eclipse SCADA
- ITU-T Focus Group M2M (global standardization initiative for a common M2M service layer)
- 3GPP studies security aspects for machine to machine (M2M) equipment, in particular automatic SIM activation covering remote provisioning and change of subscription.
- Weightless – standard group focusing on using TV "white space" for M2M
- XMPP (Jabber) protocol
- OASIS MQTT – standards group working on a lightweight publish/subscribe reliable messaging transport protocol suitable for communication in M2M/IoT contexts.
- Open Mobile Alliance (OMA_LWM2M) protocol
- RPMA (Ingenu)
- Industrial Internet Consortium
See Also
References
- ↑ Definition - What does Machine-to-Machine (M2M) mean?
- ↑ Explaining Machine to Machine (M2M)
- ↑ Evolution of M2M Technology
- ↑ M2M Communication Architecture
- ↑ How M2M Works
- ↑ Key Features of Mission Critical M2M Communications
- ↑ Top 5 Applications of Machine 2 Machine Technology
- ↑ What is the need for Machine 2 Machine communication?
- ↑ How IoT Devices Help Run an M2M Economy
- ↑ The Value Of M2M
- ↑ Issues and Concerns in M2M
- ↑ Open Initiatives in M2M
