Malvertising
What is Malvertising?
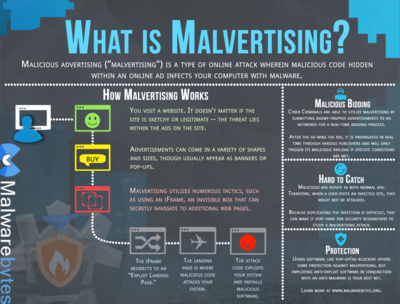
Malvertising is a malicious cyber tactic that attempts to distribute malware through online advertisements. Online advertising is a vital source of income to many websites and internet properties. With demand higher than ever, online networks have become expansive and complex in order to effectively reach large online audiences. A relatively new cyber threat, malvertising takes advantage of these pathways and uses them as a dangerous tool that requires little input from its victims.[1]
How Malvertising Works[2]
Malvertising has continued learning new tricks since it was first seen in the wild in late 2007 or early 2008. Back then, a vulnerability in Adobe Flash allowed attackers to distribute malicious advertising through several websites, including MySpace.
A few years later, in 2011, one of the first cases of a drive-by download was uncovered. Spotify was at the center of a malvertising attack that used the notorious Blackhole exploit kit, which was available for rent for a few hundred dollars a month.
Throughout the years, however, malvertising’s modus operandi has remained the same. Typically, attackers buy ad space from ad agencies and then submit infected images hoping not to get caught. Sometimes, they start by sending a legitimate ad first, and insert malicious code later. After they infect enough people, they can clean up after themselves and remove the bad code.
These cybercriminals often take advantage of the complex mechanisms used by the advertising industry. In many cases, there can be a long supply chain between the advertiser and the publisher that includes an ad network and one or more resellers. As recent malvertising attacks have shown, this entire supply chain can be manipulated. Security company Check Point Software Technologies noticed that a legitimate online advertising company might have been at the center of a malvertising scheme.
In July 2018, Check Point researchers uncovered a massive operation that distributed malvertising to users who drove by thousands of compromised WordPress websites. The ads had malicious JavaScript code that exploited unpatched vulnerabilities in browsers and browser plug-ins, including Adobe Flash Player. These attackers used multiple exploit kits, including the prolific RIG, which combines different web technologies (DoSWF, JavaScript, Flash and VBscript) to obfuscate attacks.
Check Point noticed something even more alarming. “AdsTerra, a famous ad-network company, has been purchasing traffic from a known cybercriminal posing as an ordinary publisher, which obtains its traffic via malicious activities,” Check Point wrote on its website.
Dangu has noticed that malvertisers build relationships with the most reputable ad platforms. “There's a growing awareness in the ad tech industry that it is infected by malvertisers at its core,” he says. “Whenever a malicious ad gets served to a user, it evaded multiple layers of detection through the ad tech ecosystem.”
Sometimes, cybercriminals don’t even need to go through this whole process if they can hack large websites directly, tricking them into serving people with malicious ads. It happened, for instance, to Equifax right after its notorious breach, security blogger Randy Abrams discovered.
From a regular user’s perspective, malicious ads are compelling because they often provoke strong emotions and promote calls-to-action. They can also promise products at a bargain, including an iPhone for just $1, tricking users into giving their credit card data.
Confiant found that malvertising activity is 36 percent higher during weekends, the preferred day of the week for malvertisers to attack being Sunday. The holidays or shopping seasons such as Black Friday when people are actively looking for discounts also see a spike in malvertising.
source: Malwarebytes
Overview of Malvertising[3]
When websites or web publishers unknowingly incorporate corrupted or malicious advertisements into their page, computers can become infected pre-click and post-click. It is a misconception that infection only happens when visitors begin clicking on a malvertisement. "Examples of pre-click malware include being embedded in main scripts of the page or drive-by-downloads. Malware can also auto-run, as in the case of auto redirects, where the user is automatically taken to a different site, which could be malicious. Malware can also be found in the delivery of an ad – where a clean ad that has no malware pre- or post-click (in its build and design) can still be infected whilst being called. Malicious code can hide undetected and the user has no idea what's coming their way. A post-click malvertisement example: "the user clicks on the ad to visit the advertised site, and instead is directly infected or redirected to a malicious site. These sites trick users into copying viruses or spyware usually disguised as Flash files, which are very popular on the web." Redirection is often built into online advertising, and this spread of malware is often successful because users expect a redirection to happen when clicking on an advertisement. A redirection that is taking place only needs to be co-opted in order to infect a user's computer.
Malvertising often involves the exploitation of trustworthy companies. Those attempting to spread malware place "clean" advertisements on trustworthy sites first in order to gain a good reputation, then they later "insert a virus or spyware in the code behind the ad, and after a mass virus infection is produced, they remove the virus", thus infecting all visitors of the site during that time period. The identities of those responsible are often hard to trace, making it hard to prevent the attacks or stop them altogether, because the "ad network infrastructure is very complex with many linked connections between ads and click-through destinations."
Some malvertisements can infect a vulnerable computer even if the user never clicks on the (normal-appearing) advertisement.
Malvertising vs. Ad malware[4]
Malvertising is typically confused with ad malware or adware—another form of malware affecting online advertisements.
Adware is a program running on a user’s computer. It’s usually packaged with other, legitimate software, or is installed without the user’s knowledge. Adware displays unwanted advertising, redirects search requests to advertising websites, and mines data about the user to help target or serve advertisements.
Differences between malvertising and ad malware include:
Malvertising involves malicious code which is initially deployed on a publisher’s web page. Adware, however, is only used to target individual users. Malvertising only affects users viewing an infected webpage. Adware, once installed, operates continuously on a user’s computer.
How Malvertising Can Affect Your Business[5]
Malvertising can affect small businesses in a variety of ways. Employees might unintentionally download malware on a company computer, thereby granting cybercriminals access to sensitive company data. An attack like this could have severe consequences, including ransomware attacks.
Additionally, customers could click on a malicious ad featured on your website and infect their computers. This type of malvertising breach can damage your business’s reputation, erode customer trust and limit future revenue.
Malvertising is an increasingly popular tactic for cybercriminals — some estimate that as many as 1 in 100 ads are malicious or disruptive. Online ads are so ubiquitous that users don’t think twice about clicking on them while casually browsing. A cybercriminal group known as ScamClub was able to leverage this tendency last year to overtake more than 300 million browser sessions using fake ads.
Types of Malvertising[6]
Malvertising comes in all shapes and sizes but all forms can pose risks to your sensitive information. Here are some common types of malvertising:
- Redirection: Clicking on a malware ad will often redirect you to spoof sites that look legitimate but are actually set up for phishing attacks, in which criminals try to trick you into surrendering personal information such as your Social Security number, credit card numbers or bank account credentials. These sites are designed to look like legitimate sites, whether they are mimicking the webpages of banks, credit unions, or credit card providers.
- Malware: The other main type of malvertising is more proactive and can quickly infect your computer. This version of malware populates legitimate sites — ones that you might visit every day — with infected banner or box ads. Clicking on such an ad could install spyware, viruses, trojans or other types of malware on your computer. This type of malicious software can be especially dangerous because it often operates in the background, stealing your personal and financial information, tracking your keystrokes and monitoring your email messages without you ever noticing.
- Sometimes you don’t have to click: You might think you’re safe from malvertising because you never click on online ads, including pop-ups. But here’s the scary part: Even if you vow to never click an ad, you’re not completely safe from malvertising. That’s because the version of malware known as drive-by downloads can start infecting your computer with spyware or malware as soon as an infected page starts loading. You don’t have to click anything to start the process.
Best Practices to Avoid Malvertising Attacks[7]
Awareness is only the first step in protecting against malvertising attacks. There are a number of solutions that, when used in combination, can help ensure that you remain safe from threats distributed by malvertisements:
- Identify ads that seem illegitimate: Use the information in this article to help determine which ads are safe and which may contain harmful code.
- Use an ad blocker: By blocking all advertisements from displaying on websites, you will remove any chance of viewing clicking on an ad that is potentially harmful.
- Search for a company without clicking on an ad: If you are interested in what an advertisement is offering but are unsure about whether an ad is legitimate or not, simply visit the company’s website without clicking on the ad. If there is no website, or if there are complaints about the company, then the ad was most likely fake.
- Resist clicking on ads, even if they appear to be from reputable companies: Simply put, if you never click on advertisements, you will never click on a malvertisement either.
- Stay up-to-date on the latest malvertising scandals: By following news about compromised websites and potential malvertising campaigns, you can protect yourself and others from known malvertising threats.
- Run anti-virus/anti-malware on your computer: While these solutions cannot protect against all forms of malware, they are a good first line of defense against known malware that can infect your computer.
See Also
References
- ↑ Definition - What Does Malvertising Mean? Forcepoint
- ↑ How Malvertising Works CSO Online
- ↑ Overview of Malvertising Wikipedia
- ↑ Malvertising vs. Ad malware Imperva
- ↑ How Malvertising Can Affect Your Business Sitelock
- ↑ Types of Malvertising Norton
- ↑ Best Practices to Avoid Malvertising Attacks Digital Guardian
