Risk IT Framework
What is the Risk IT Framework?
Risk IT is a set of proven, real-world practices that helps enterprises achieve their goals, seize opportunities and seek greater returns with less risk. It works at the intersection of business and IT and allows enterprises to manage and even capitalize on risk in the pursuit of their objectives. It extends COBIT, the globally recognized IT Governance Framework, and saves time, cost and effort by providing enterprises with a way to focus effectively on IT-related business risk areas, including risks related to late project delivery, compliance, misalignment, obsolete IT architecture, and IT service delivery problems.
The Risk IT Framework provides a set of guiding principles and supporting practices for enterprise management, combined to deliver a comprehensive process model for governing and managing IT risk. For users of COBIT and Val IT Framework, this process model will look familiar. Guidance is provided on the key activities within each process, responsibilities for the process, information flows between processes, and performance management of each process. The model is divided into the following three domains, each of which contains three processes:
- Risk Governance:
- Establish and maintain a common risk view
- Integrate with enterprise risk management and
- Make risk-aware business decisions
- Risk Evaluation:
- Collect data
- Analyze risk
- Maintain risk profile
- Risk Response:
- Articulate risk
- Manage risk
- React to events[1]
The Risk IT Framework fills the gap between generic Risk Management Frameworks and detailed (primarily security-related) IT risk management frameworks. It provides an end-to-end comprehensive view of all risks related to the use of IT and a similarly thorough treatment of risk management, from the tone and culture at the top to operational issues. In summary, the framework will enable enterprises to understand and manage all significant IT risk types, building upon the existing risk-related components within the current ISACA frameworks, i.e., COBIT and Val IT Framework.[2]
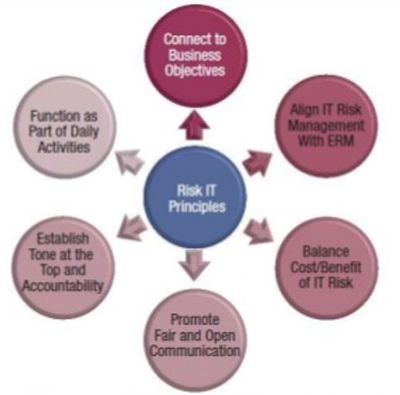
The Risk IT Principles[3]
Risk IT defines and is founded on, a number of guiding principles for the effective management of IT risk. The principles are based on commonly accepted ERM principles, which have been applied to the domain of IT. The Risk IT framework is about IT risk—in other words, business risk related to the use of IT. The connection to business is founded in the principles on which the framework is built, i.e., effective enterprise governance and management of IT risk, as shown in the figure below:
- Always connect to business objectives
- Align the management of IT-related business risk with overall ERM, if applicable, i.e., if ERM is implemented in the enterprise
- Balance the costs and benefits of managing IT risk
- Promote fair and open communication of IT risk
- Establish the right tone from the top while defining and enforcing personal accountability for operating within acceptable and well-defined tolerance levels
- Are a continuous process and part of daily activities
Risk IT Domains and Processes[4]
The three domains of the Risk IT framework are listed below with the contained processes (three by domain); each process contains a number of activities:
- Risk Governance: Ensure that IT risk management practices are embedded in the enterprise, enabling it to secure optimal risk-adjusted returns. It is based on the following processes:
- RG1 Establish and Maintain a Common Risk View
- RG1.1 Perform enterprise IT risk assessment
- RG1.2 Propose IT risk tolerance thresholds
- RG1.3 Approve IT risk tolerance
- RG1.4 Align IT risk policy
- RG1.5 Promote IT risk-aware culture
- RG1.6 Encourage effective communication of IT risk
- RG2 Integrate With ERM
- RG2.1 Establish and maintain accountability for IT risk management
- RG2.2 Coordinate IT risk strategy and business risk strategy
- RG2.3 Adapt IT risk practices to enterprise risk practices
- RG2.4 Provide adequate resources for IT risk management
- RG2.5 Provide independent assurance over IT risk management
- RG3 Make Risk-aware Business Decisions
- RG3.1 Gain management buy-in for the IT risk analysis approach
- RG3.2 Approve IT risk analysis
- RG3.3 Embed IT risk consideration in strategic business decision making
- RG3.4 Accept IT risk
- RG3.5 Prioritise IT risk response activities
- Risk Evaluation: Ensure that IT-related risks and opportunities are identified, analyzed, and presented in business terms. It is based on the following processes:
- RE1 Collect Data
- RE1.1 Establish and maintain a model for data collection
- RE1.2 Collect data on the operating environment
- RE1.3 Collect data on risk events
- RE1.4 Identify risk factors
- RE2 Analyse Risk
- RE2.1 Define IT risk analysis scope
- RE2.2 Estimate IT risk
- RE2.3 Identify risk response options
- RE2.4 Perform a peer review of IT risk analysis
- RE3 Maintain Risk Profile
- RE3.1 Map IT resources to business processes
- RE3.2 Determines business criticality of IT resources
- RE3.3 Understand IT capabilities
- RE3.4 Update risk scenario components
- RE3.5 Maintain the IT risk register and iT risk map
- RE3.6 Develop IT risk indicators
- Risk Response: Ensure that IT-related risk issues, opportunities, and events are addressed in a cost-effective manner and in line with business priorities. It is based on the following processes:
- RR1 Articulate Risk
- RR1.1 Communicate IT risk analysis results
- RR1.2 Report IT risk management activities and state of compliance
- RR1.3 Interpret independent IT assessment findings
- RR1.4 Identify IT-related opportunities
- RR2 Manage Risk
- RR2.1 Inventory controls
- RR2.2 Monitor operational alignment with risk tolerance thresholds
- RR2.3 Respond to discovered risk exposure and opportunity
- RR2.4 Implement controls
- RR2.5 Report IT risk action plan progress
- RR3 React to Events
- RR3.1 Maintain incident response plans
- RR3.2 Monitor IT risk
- RR3.3 Initiate incident response
- RR3.4 Communicate lessons learned from risk events
Each process is detailed by:
- Process components
- Management practice
- Inputs and Outputs
- RACI charts
- Goal and metrics
Risk IT Process Model (see illustration below)
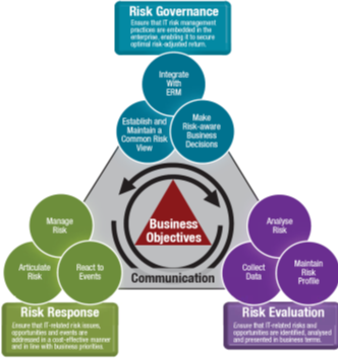
source: Urs Fischer, CISA, CRISC
Risk IT - Implementation Approach[5]
The implementation approach for the risk framework at NSE, (National Stock Exchange) the largest stock exchange in India is described in the figure below:
The implementation of risk management was conducted at two levels:
- Develop risk register for business functions.
- Define aggregation process to arrive at an organization-level risk profile.
Business processes were categorized in the following areas:
- Most critical (core production)
- Critical (production)
- Support functions
For each business function, the following activities were performed:
- Conduct risk evaluation facilitated workshops.
- Generate risk profile for inherent risk (risk without considering controls).
- Determine response options.
- Identify and assess controls from the control catalog.
- Identify positive (excess) and negative (missing) control gaps.
- Define a plan for closing control gaps.
- Finalize the risk register.
- Obtain confirmation from the risk owner (department heads).
For an aggregation of the risk profile at the organization level, the following activities were performed:
- Build a matrix for all identified risks.
- Collect department-wide data, and build the matrix.
- Add weightage of criticality for each department.
- Arrive at organization-level risk profile.
- Review and sanitize the risk profile by eliminating mathematically inappropriate impacts and likelihood.
- Present risk profile to board and senior management.
Benefits/Outcomes of Risk IT
The benefits of using Risk IT include:
- A common language to help communication between business IT, risk, and audit management
- End-to-end guidance on how to manage IT-related risks
- A complete risk profile to better understand risk, so as to better utilize enterprise resources
- A better understanding of the roles and responsibilities with regard to IT risk management
- Alignment with ERM
- A better view of IT-related risk and its financial implications
- Fewer operational surprises and failures
- Increased information quality
- Greater stakeholder confidence and reduced regulatory concerns
- Innovative applications supporting new business initiatives
The Cons of Risk IT[6]
- While the framework’s purpose and design are to address Risk IT, the framework has been recently developed, and therefore, the assessments of touted benefits are not available for longer terms.
- The framework is left flexible and therefore, the incorrect or less robust implementation may not be able to provide the benefits, and may leave unaddressed or undetected risks within the enterprise IT organization.
- The framework is maintained and published by ISACA, and not adopted by any standards body, such as ANSI, etc. but instead is based on best practices and therefore, the acceptability of the framework may not have wider appeal.
- The framework relies on appropriate implementation of both COBIT and Val IT, which may not be the case in all organizations, and therefore, may offer hindrance in its acceptability within many organizations.
- The comprehensive nature of the framework can quickly become a cost overhead of IT risk management, in spite of the utilization of existing IT controls.
See Also
References