Difference between revisions of "Network Address Translation (NAT)"
m (The LinkTitles extension automatically added links to existing pages (https://github.com/bovender/LinkTitles).) |
|||
| Line 1: | Line 1: | ||
| − | [[Network]] Address Translation (NAT) is a [[process]] in which one or more local IP address is translated into one or more Global IP address and vice versa in order to provide [[Internet]] access to the local hosts. Also, it does the translation of [[port]] numbers i.e. masks the port number of the host with another port number, in the packet that will be routed to destination. It then makes the corresponding entries of ip address and port number in the NAT table. NAT generally operates on router or [[firewall]].<ref>Defining Network Address Translation (NAT) [https://www.geeksforgeeks.org/computer-network-network-address-translation-nat/ Geeks for Geeks]</ref> | + | '''[[Network]] Address Translation (NAT)''' is a [[process]] in which one or more local IP address is translated into one or more Global IP address and vice versa in order to provide [[Internet]] access to the local hosts. Also, it does the translation of [[port]] numbers i.e. masks the port number of the host with another port number, in the packet that will be routed to destination. It then makes the corresponding entries of ip address and port number in the NAT table. NAT generally operates on router or [[firewall]].<ref>Defining Network Address Translation (NAT) [https://www.geeksforgeeks.org/computer-network-network-address-translation-nat/ Geeks for Geeks]</ref> |
| + | |||
| + | |||
| + | [[File:Network Address Translation-NAT.jpg|400px|Network Address Translation (NAT)]]<br /> | ||
| + | source: [http://www.watchguard.com/training/fireware/82/nat602.htm Watguard] | ||
| + | |||
| + | |||
| + | '''Explaining Network Address Translation (NAT)'''<ref>Explaining Network Address Translation (NAT) [https://whatismyipaddress.com/nat whatismyipaddress.com]</ref><br /> | ||
| + | The most common form of network translation involves a large private network using addresses in a private range (10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.255, or 192.168.0 0 to 192.168.255.255). The private addressing scheme works well for computers that only have to access resources inside the network, like workstations needing access to file servers and printers. Routers inside the private network can route traffic between private addresses with no trouble. However, to access resources outside the network, like the Internet, these computers have to have a public address in order for responses to their requests to return to them. This is where NAT comes into play. | ||
| + | |||
| + | Internet requests that require Network Address Translation (NAT) are quite complex but happen so rapidly that the end user rarely knows it has occurred. A workstation inside a network makes a request to a computer on the Internet. Routers within the network recognize that the request is not for a resource inside the network, so they send the request to the firewall. The firewall sees the request from the computer with the internal IP. It then makes the same request to the Internet using its own public address, and returns the response from the Internet resource to the computer inside the private network. From the perspective of the resource on the Internet, it is sending information to the address of the firewall. From the perspective of the workstation, it appears that communication is directly with the site on the Internet. When NAT is used in this way, all users inside the private network access the Internet have the same public IP address when they use the Internet. That means only one public address is needed for hundreds or even thousands of users. | ||
| + | |||
| + | Most modern firewalls are stateful – that is, they are able to set up the connection between the internal workstation and the Internet resource. They can keep track of the details of the connection, like ports, packet order, and the IP addresses involved. This is called keeping track of the state of the connection. In this way, they are able to keep track of the session composed of communication between the workstation and the firewall, and the firewall with the Internet. When the session ends, the firewall discards all of the information about the connection. | ||
| + | |||
| + | There are other uses for Network Address Translation (NAT) beyond simply allowing workstations with internal IP addresses to access the Internet. In large networks, some servers may act as Web servers and require access from the Internet. These servers are assigned public IP addresses on the firewall, allowing the public to access the servers only through that IP address. However, as an additional layer of security, the firewall acts as the intermediary between the outside world and the protected internal network. Additional rules can be added, including which ports can be accessed at that IP address. Using NAT in this way allows network engineers to more efficiently route internal network traffic to the same resources, and allow access to more ports, while restricting access at the firewall. It also allows detailed logging of communications between the network and the outside world. | ||
| + | |||
| + | Additionally, NAT can be used to allow selective access to the outside of the network, too. Workstations or other computers requiring special access outside the network can be assigned specific external IPs using NAT, allowing them to communicate with computers and applications that require a unique public IP address. Again, the firewall acts as the intermediary, and can control the session in both directions, restricting port access and protocols. | ||
| + | |||
| + | NAT is a very important aspect of firewall security. It conserves the number of public addresses used within an organization, and it allows for stricter control of access to resources on both sides of the firewall. | ||
| + | |||
| + | |||
| + | '''Why Use NAT?'''<ref>Why Use NAT? [https://www.comptia.org/content/guides/what-is-network-address-translation Comptia.org]</ref><br /> | ||
| + | NAT is a straightforward enough process, but what is the point of it? Ultimately, it comes down to conservation and security. | ||
| + | *IP Conservation: IP addresses identify each device connected to the internet. The existing IP version 4 (IPv4) uses 32-bit numbered IP addresses, which allows for 4 billion possible IP addresses, which seemed like more than enough when it launched in the 1970s. However, the internet has exploded, and while not all 7+ billion people on the planet access the internet regularly, those that do often have multiple connected devices: phones, personal desktop, work laptop, tablet, TV, even refrigerators. Therefore, the number of devices accessing the internet far surpasses the number of IP addresses available. Routing all of these devices via one connection using NAT helps to consolidate multiple private IP addresses into one public IP address. This helps to keep more public IP addresses available even while private IP addresses proliferate. On June 6, 2012, IP version 6 (IPv6) officially launched to accommodate the need for more IP addresses. IPv6 uses 128-bit numbered IP addresses, which allow for exponentially more potential IP addresses. It will take many years before this process finishes; so until then, NAT will be a valuable tool. | ||
| + | *NAT Security: Additionally, NAT can provide security and privacy. Because NAT transfers packets of data from public to private addresses, it also prevents anything else from accessing the private device. The router sorts the data to ensure everything goes to the right place, making it more difficult for unwanted data to get by. It’s not foolproof, but it often acts as the first means of defense for your device. If an organization wants to protect its data, they’ll need to go further than just a NAT firewall — they’ll want to hire a cybersecurity professional. NAT also allows you to display a public IP address while on a local network, helping to keep data and user history private. All of this might seem complicated in theory, but it’s even more so in the real world. IT professionals use NAT to secure their data and use several devices under the same IP – and everyone is interested in securing their data. Getting the right certification helps IT professionals demonstrate their competence and understanding of these complicated subjects. | ||
| + | |||
| + | |||
| + | '''How NAT Works'''<ref>How NAT Works [https://computer.howstuffworks.com/nat.htm How Stuff Works]</ref><br /> | ||
| + | Developed by Cisco, Network Address Translation is used by a device (firewall, router or computer that sits between an internal network and the rest of the world. NAT has many forms and can work in several ways: | ||
| + | *Static NAT - Mapping an unregistered IP address to a registered IP address on a one-to-one basis. Particularly useful when a device needs to be accessible from outside the network. | ||
| + | |||
| + | |||
| + | [[File:Static NAT.jpg|400px|Static NAT]]<br /> | ||
| + | |||
| + | |||
| + | *Dynamic NAT - Maps an unregistered IP address to a registered IP address from a group of registered IP addresses. | ||
| + | |||
| + | |||
| + | [[File:Dynamic NAT.jpg|400px|Dynamic NAT]]<br /> | ||
| + | |||
| + | |||
| + | *Overloading - A form of dynamic NAT that maps multiple unregistered IP addresses to a single registered IP address by using different ports. This is known also as PAT (Port Address Translation), single address NAT or port-level multiplexed NAT. | ||
| + | |||
| + | |||
| + | [[File:Overloading NAT.jpg|400px|Overloading NAT]]<br /> | ||
| + | |||
| + | |||
| + | *Overlapping - When the IP addresses used on your internal network are registered IP addresses in use on another network, the router must maintain a lookup table of these addresses so that it can intercept them and replace them with registered unique IP addresses. It is important to note that the NAT router must translate the "internal" addresses to registered unique addresses as well as translate the "external" registered addresses to addresses that are unique to the private network. This can be done either through static NAT or by using DNS and implementing dynamic NAT. | ||
| + | |||
| + | |||
| + | [[File:Overlapping NAT.jpg|400px|Overlapping NAT]]<br /> | ||
| + | |||
| + | |||
| + | The internal network is usually a LAN (Local Area Network), commonly referred to as the stub domain. A stub domain is a LAN that uses IP addresses internally. Most of the network traffic in a stub domain is local, so it doesn't travel outside the internal network. A stub domain can include both registered and unregistered IP addresses. Of course, any computers that use unregistered IP addresses must use Network Address Translation to communicate with the rest of the world. | ||
Revision as of 15:50, 8 July 2021
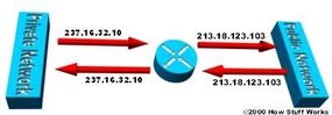
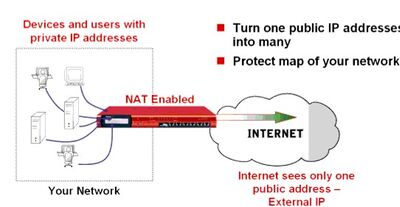
Network Address Translation (NAT) is a process in which one or more local IP address is translated into one or more Global IP address and vice versa in order to provide Internet access to the local hosts. Also, it does the translation of port numbers i.e. masks the port number of the host with another port number, in the packet that will be routed to destination. It then makes the corresponding entries of ip address and port number in the NAT table. NAT generally operates on router or firewall.[1]
source: Watguard
Explaining Network Address Translation (NAT)[2]
The most common form of network translation involves a large private network using addresses in a private range (10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.255, or 192.168.0 0 to 192.168.255.255). The private addressing scheme works well for computers that only have to access resources inside the network, like workstations needing access to file servers and printers. Routers inside the private network can route traffic between private addresses with no trouble. However, to access resources outside the network, like the Internet, these computers have to have a public address in order for responses to their requests to return to them. This is where NAT comes into play.
Internet requests that require Network Address Translation (NAT) are quite complex but happen so rapidly that the end user rarely knows it has occurred. A workstation inside a network makes a request to a computer on the Internet. Routers within the network recognize that the request is not for a resource inside the network, so they send the request to the firewall. The firewall sees the request from the computer with the internal IP. It then makes the same request to the Internet using its own public address, and returns the response from the Internet resource to the computer inside the private network. From the perspective of the resource on the Internet, it is sending information to the address of the firewall. From the perspective of the workstation, it appears that communication is directly with the site on the Internet. When NAT is used in this way, all users inside the private network access the Internet have the same public IP address when they use the Internet. That means only one public address is needed for hundreds or even thousands of users.
Most modern firewalls are stateful – that is, they are able to set up the connection between the internal workstation and the Internet resource. They can keep track of the details of the connection, like ports, packet order, and the IP addresses involved. This is called keeping track of the state of the connection. In this way, they are able to keep track of the session composed of communication between the workstation and the firewall, and the firewall with the Internet. When the session ends, the firewall discards all of the information about the connection.
There are other uses for Network Address Translation (NAT) beyond simply allowing workstations with internal IP addresses to access the Internet. In large networks, some servers may act as Web servers and require access from the Internet. These servers are assigned public IP addresses on the firewall, allowing the public to access the servers only through that IP address. However, as an additional layer of security, the firewall acts as the intermediary between the outside world and the protected internal network. Additional rules can be added, including which ports can be accessed at that IP address. Using NAT in this way allows network engineers to more efficiently route internal network traffic to the same resources, and allow access to more ports, while restricting access at the firewall. It also allows detailed logging of communications between the network and the outside world.
Additionally, NAT can be used to allow selective access to the outside of the network, too. Workstations or other computers requiring special access outside the network can be assigned specific external IPs using NAT, allowing them to communicate with computers and applications that require a unique public IP address. Again, the firewall acts as the intermediary, and can control the session in both directions, restricting port access and protocols.
NAT is a very important aspect of firewall security. It conserves the number of public addresses used within an organization, and it allows for stricter control of access to resources on both sides of the firewall.
Why Use NAT?[3]
NAT is a straightforward enough process, but what is the point of it? Ultimately, it comes down to conservation and security.
- IP Conservation: IP addresses identify each device connected to the internet. The existing IP version 4 (IPv4) uses 32-bit numbered IP addresses, which allows for 4 billion possible IP addresses, which seemed like more than enough when it launched in the 1970s. However, the internet has exploded, and while not all 7+ billion people on the planet access the internet regularly, those that do often have multiple connected devices: phones, personal desktop, work laptop, tablet, TV, even refrigerators. Therefore, the number of devices accessing the internet far surpasses the number of IP addresses available. Routing all of these devices via one connection using NAT helps to consolidate multiple private IP addresses into one public IP address. This helps to keep more public IP addresses available even while private IP addresses proliferate. On June 6, 2012, IP version 6 (IPv6) officially launched to accommodate the need for more IP addresses. IPv6 uses 128-bit numbered IP addresses, which allow for exponentially more potential IP addresses. It will take many years before this process finishes; so until then, NAT will be a valuable tool.
- NAT Security: Additionally, NAT can provide security and privacy. Because NAT transfers packets of data from public to private addresses, it also prevents anything else from accessing the private device. The router sorts the data to ensure everything goes to the right place, making it more difficult for unwanted data to get by. It’s not foolproof, but it often acts as the first means of defense for your device. If an organization wants to protect its data, they’ll need to go further than just a NAT firewall — they’ll want to hire a cybersecurity professional. NAT also allows you to display a public IP address while on a local network, helping to keep data and user history private. All of this might seem complicated in theory, but it’s even more so in the real world. IT professionals use NAT to secure their data and use several devices under the same IP – and everyone is interested in securing their data. Getting the right certification helps IT professionals demonstrate their competence and understanding of these complicated subjects.
How NAT Works[4]
Developed by Cisco, Network Address Translation is used by a device (firewall, router or computer that sits between an internal network and the rest of the world. NAT has many forms and can work in several ways:
- Static NAT - Mapping an unregistered IP address to a registered IP address on a one-to-one basis. Particularly useful when a device needs to be accessible from outside the network.
- Dynamic NAT - Maps an unregistered IP address to a registered IP address from a group of registered IP addresses.
- Overloading - A form of dynamic NAT that maps multiple unregistered IP addresses to a single registered IP address by using different ports. This is known also as PAT (Port Address Translation), single address NAT or port-level multiplexed NAT.
- Overlapping - When the IP addresses used on your internal network are registered IP addresses in use on another network, the router must maintain a lookup table of these addresses so that it can intercept them and replace them with registered unique IP addresses. It is important to note that the NAT router must translate the "internal" addresses to registered unique addresses as well as translate the "external" registered addresses to addresses that are unique to the private network. This can be done either through static NAT or by using DNS and implementing dynamic NAT.
The internal network is usually a LAN (Local Area Network), commonly referred to as the stub domain. A stub domain is a LAN that uses IP addresses internally. Most of the network traffic in a stub domain is local, so it doesn't travel outside the internal network. A stub domain can include both registered and unregistered IP addresses. Of course, any computers that use unregistered IP addresses must use Network Address Translation to communicate with the rest of the world.
- ↑ Defining Network Address Translation (NAT) Geeks for Geeks
- ↑ Explaining Network Address Translation (NAT) whatismyipaddress.com
- ↑ Why Use NAT? Comptia.org
- ↑ How NAT Works How Stuff Works