Firewall
What is a Firewall?
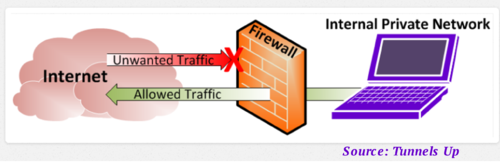
A firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet.[1]
Data flows into and out of devices through what we call ports. A firewall controls what is - and, more importantly, isn't - allowed to pass through those ports. You can think of it like a security guard standing at the door, checking the ID of everything that tries to enter or exit. For most normal computers or home networks, the firewall should allow very little, if any, inbound traffic. There's rarely any legitimate reason for other devices to need to connect to your device or home network unsolicited.[2]
A firewall can be installed as a software program on a single computer. This type of firewall is often limited to only blocking traffic in or out of the computer. For instance, in the Windows operating system, a firewall is installed by default. This will block traffic coming into the computer but allow traffic to leave the computer.
Many companies like to put a firewall on the edge of their network. This is a physical device that sits between the public internet and the private internal network. These types of physical firewalls are created by such companies as Cisco or Juniper.
There are three reasons to deploy a firewall in the network: access control, NAT and VPN. Access control is where policies are created to block or permit traffic based on IP address, port, and protocol. NAT, or network address translation, is the act of converting one IP address to another. A firewall often is equipped to do many kinds of NAT, which would be translating the private internal IP addresses to publicly accessible IP addresses. Firewalls also often have VPN capabilities. A Virtual Private Network is a technology used to securely connect two networks together across an insecure network such as the Internet.[3]
What Firewalls Do And Why Do We Need Them?[4]
A Firewall is a necessary part of any security architecture and takes the guesswork out of host-level protections and entrusts them to your network security device. Firewalls, especially Next Generation Firewalls, focus on blocking malware and application-layer attacks, along with an integrated intrusion prevention system (IPS); these Next Generation Firewalls can react quickly and seamlessly to detect and react to outside attacks across the whole network. They can set policies to better defend your network and carry out quick assessments to detect invasive or suspicious activity, like malware, and shut it down.
Firewalls, especially Next Generation Firewalls, focus on blocking malware and application-layer attacks. Along with an integrated intrusion prevention system (IPS), these Next Generation Firewalls are able to react quickly and seamlessly to detect and combat attacks across the whole network. Firewalls can act on previously set policies to better protect your network. They can carry out quick assessments to detect invasive or suspicious activity, such as malware, and shut it down. By leveraging a firewall for your security infrastructure, you’re setting up your network with specific policies to allow or block incoming and outgoing traffic.
Types of Firewall[5]
- Proxy firewall: An early type of firewall device, a proxy firewall serves as the gateway from one network to another for a specific application. Proxy servers can provide additional functionality, such as content caching and security, by preventing direct connections outside the network. However, this also may impact throughput capabilities and the applications they can support.
- Stateful inspection firewall: Now considered a “traditional” firewall, a stateful inspection firewall allows or blocks traffic based on state, port, and protocol. It monitors all activity from the opening of a connection until it is closed. Filtering decisions are made based on both administrator-defined rules as well as context, which refers to using information from previous connections and packets belonging to the same connection.
- Unified threat management (UTM) firewall: A UTM device typically combines, in a loosely coupled way, the functions of a stateful inspection firewall with intrusion prevention and antivirus. It may also include additional services and often cloud management. UTMs focus on simplicity and ease of use.
- Next-generation firewall (NGFW): Firewalls have evolved beyond simple packet filtering and stateful inspection. Most companies are deploying next-generation firewalls to block modern threats such as advanced malware and application-layer attacks. According to Gartner’s definition, a next-generation firewall must include:
- Intelligence-based access control with stateful inspection
- Integrated intrusion prevention system (IPS)
- Application awareness and control to see and block risky apps
- Upgrade paths to include future information feeds
- Techniques to address evolving security threats
- URL filtering based on geolocation and reputation
While these capabilities are increasingly becoming the standard for most companies, NGFWs can do more.
- Threat-focused NGFW: These firewalls include all the capabilities of a traditional NGFW and provide advanced threat detection and remediation. With a threat-focused NGFW, you can:
- Know which assets are most at risk with complete context awareness
- Quickly react to attacks with intelligent security automation that sets policies and hardens your defenses dynamically
- Better detect evasive or suspicious activity with network and endpoint event correlation
- Greatly decrease the time from detection to clean up with retrospective security that continuously monitors for suspicious activity and behavior even after initial inspection
- Ease administration and reduce complexity with unified policies that protect the entire attack continuum
- Virtual firewall: A virtual firewall is typically deployed as a virtual appliance in a private cloud (VMware ESXi, Microsoft Hyper-V, KVM) or public cloud (Amazon Web Services or AWS, Microsoft Azure, Google Cloud Platform or GCP, Oracle Cloud Infrastructure or OCI) to monitor and secure traffic across physical and virtual networks. A virtual firewall is often a key component in software-defined networks (SDN).
- Cloud Native Firewall: Cloud-native firewalls are modernizing how to secure applications and workload infrastructure at scale. With automated scaling features, cloud-native firewalls enable networking operations and security operations teams to run at agile speeds. Advantages of Cloud Native Firewalls include:
- Agile and elastic security
- Multi-tenant capability
- Smart load balancing
How a Firewall Works[6]
A firewall decides which network traffic is allowed to pass through and which is deemed dangerous. It essentially works by filtering out the good from the bad or the trusted from the untrusted. However, before we go into detail, we must first understand the structure of web-based networks before explaining how a firewall operates to filter between them.
Firewalls are intended to secure the private networks and the endpoint devices within, known as network hosts.
Network hosts are devices that "talk" with other hosts on the network. They send and receive between internal networks, as well as outbound and inbound between external networks.
Your computers and other endpoint devices use networks to access the internet — and each other. However, the internet is segmented into sub-networks or 'subnets' for security and privacy.
The basic subnet segments are as follows:
- External public networks typically refer to the public/global internet or extranets.
- Internal private network defines a home network, corporate intranets, and other "closed" networks.
- Perimeter networks detail border networks made of bastion hosts — computer hosts dedicated to hardened security that are ready to endure an external attack. As a secured buffer between internal and external networks, these can also be used to house any external-facing services provided by the internal network (i.e., servers for web, mail, FTP, VoIP, etc.). These are more secure than external networks but less secure than internal ones. These are not always present in simpler networks like home networks but may often be used in organizational or national intranets.
Screening routers are specialized gateway computers placed on a network to segment it. They are known as house firewalls on the network level. The two most common segment models are the screened host firewall and the screened subnet firewall.
- Screened host firewalls use a single screening router between the external and internal networks, known as the choke router. These networks are the two subnets of this model.
- Screened subnet firewalls use two screening routers— one known as an access router between the external and perimeter network and another labeled as the choke router between the perimeter and internal network. This creates three subnets, respectively.
Both the network perimeter and host machines themselves can house a firewall. To do this, it is placed between a single computer and its connection to a private network.
- Network firewalls involve the application of one or more firewalls between external networks and internal private networks. These regulate inbound and outbound network traffic, separating external public networks—like the global internet—from internal networks like home Wi-Fi networks, enterprise intranets, or national intranets. Network firewalls may come in the form of any of the following appliance types: dedicated hardware, software, and virtual.
- Host firewalls or 'software firewalls' involve using firewalls on individual user devices and other private network endpoints as a barrier between devices within the network. These devices, or hosts, receive customized traffic regulation to and from specific computer applications. Host firewalls may run on local devices as an operating system service or an endpoint security application. Host firewalls can also dive deeper into web traffic, filtering based on HTTP and other networking protocols, allowing the management of what content arrives at your machine rather than just where it comes from.
Network firewalls require configuration against a broad scope of connections, whereas host firewalls can be tailored to fit each machine's needs. However, host firewalls require more effort to customize, meaning network-based are ideal for a sweeping control solution. But using both firewalls in both locations simultaneously is ideal for a multi-layer security system.
Filtering traffic via a firewall uses pre-set or dynamically learned rules for allowing and denying attempted connections. These rules are how a firewall regulates the web traffic flow through your private network and private computer devices. Regardless of type, all firewalls may filter by some blend of the following:
- Source: Where an attempted connection is being made from.
- Destination: Where an attempted connection is intended to go.
- Contents: What an attempted connection is trying to send.
- Packet protocols: What "language" an attempted connection is speaking to carry its message? Among the networking protocols hosts use to "talk" with each other, TCP/IP is the primary protocol used to communicate across the internet and within intranet/sub-networks. Other standard protocols include IMCP and UDP.
- Application protocols: Common protocols include HTTP, Telnet, FTP, DNS, and SSH.
Source and destination are communicated by internet protocol (IP) addresses and ports. IP addresses are unique device names for each host. Ports are a sub-level of any source and destination host device, similar to office rooms within a larger building. Ports are typically assigned specific purposes, so certain protocols and IP addresses utilizing uncommon or disabled ports can be a concern.
Using these identifiers, a firewall can decide if a data packet attempting a connection is to be discarded—silently or with an error reply to the sender—or forwarded.
Vulnerabilities of a Firewall[7]
Less advanced firewalls – packet filtering, for example – are vulnerable to higher-level attacks because they do not use DPI to examine packets fully. NGFWs were introduced to address that vulnerability. However, NGFWs still face challenges and are vulnerable to evolving threats. For this reason, organizations should pair them with other security components, like intrusion detection and prevention systems. Some examples of modern threats that a firewall may be vulnerable to are:
- Insider attacks: Organizations can use internal firewalls on top of a perimeter firewall to segment the network and provide internal protection. If an attack is suspected, organizations can audit sensitive using NGFW features. All the audits should measure up to baseline documentation within the organization that outlines best practices for using the organization's network. Some examples of behavior that might indicate an insider threat include the following:
- transmission of sensitive data in plain text.
- resource access outside of business hours.
- sensitive resource access failure by the user.
- third-party users' network resource access.
- Distributed denial of service (DDoS) attacks: A DDoS attack is a malicious attempt to disrupt normal traffic of a targeted network by overwhelming the target or its surrounding infrastructure with a flood of traffic. It utilizes multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources, such as Internet of Things (IoT) devices. A DDoS attack is like a traffic jam preventing regular traffic from reaching its desired destination. The key concern in mitigating a DDoS attack is differentiating between the attack and normal traffic. Many times, the traffic in this attack type can come from seemingly legitimate sources and requires cross-checking and auditing from several security components.
- Malware: Malware threats are varied, complex, and constantly evolving alongside security technology and the networks it protects. As networks become more complex and dynamic with the rise of IoT, it becomes more difficult for firewalls to defend them.
- Patching/Configuration: A poorly configured firewall or a missed update from the vendor can be detrimental to network security. IT admins should be proactive in maintaining their security components.
See Also
- Network Security
- Network Architecture
- Cyber Security
- Security
- Security Architecture
- Data Center Infrastructure
References