Difference between revisions of "Risk Management Framework (RMF)"
m (The LinkTitles extension automatically added links to existing pages (https://github.com/bovender/LinkTitles).) |
|||
| Line 1: | Line 1: | ||
| − | The ''' | + | == What is the NIST Risk Management Framework? == |
| + | The '''NIST Risk Management Framework (RMF)''' is a set of criteria that dictate how United States government IT systems must be architected, secured, and monitored. Originally developed by the Department of Defense (DoD), the RMF was adopted by the rest of the US federal information systems in 2010. The RMF is maintained by the National Institute of Standards and Technology (NIST) and provides a solid foundation for any data security strategy.<ref>Defining Risk Management Framework [https://www.varonis.com/blog/risk-management-framework/ Varonis]</ref> | ||
| − | NIST Special Publication 800-37, "Guide for Applying the Risk Management Framework to Federal Information Systems", developed by the Joint Task Force Transformation Initiative Working Group, transforms the traditional Certification and Accreditation (C&A) | + | NIST Special Publication 800-37, "Guide for Applying the Risk Management Framework to Federal Information Systems", developed by the Joint Task Force Transformation Initiative Working Group, transforms the traditional Certification and Accreditation (C&A) process into the six-step Risk Management Framework (RMF). The Risk Management Framework (RMF), provides a disciplined and structured process that integrates information security and risk management activities into the system development life cycle. |
| − | + | == Components of the Risk Management Framework (RMF)<ref>[https://www.techtarget.com/searchcio/definition/Risk-Management-Framework-RMF What are the components of the RMF??]</ref> == | |
| − | The risk- | + | There are five components that make up the RMF. These components include the following: |
| + | #Identification: The first component in implementing the Risk Management Framework is to identify the risks that the organization faces. These might include strategic, legal, operational, and privacy risks. It is important to note that risk identification is not a one-time process. The risks that an organization faces tend to change over time, so risk assessments will need to be performed on a periodic basis. | ||
| + | #Measurement and assessment: The goal behind the measurement and assessment component is to create a risk profile for each risk that has been identified. There are a number of different ways that organizations might complete the measurement and assessment phase of the process. In some cases, risk measurement might be based on something as simple as how much capital could potentially be lost as a result of the risk. However, in other cases, measuring the potential impact of a risk might be far more difficult. In the field of information security, for example, an organization might attempt to quantify the cost of a security breach compared with the cost of implementing a security mechanism that can help to mitigate the risk. | ||
| + | #Mitigation: The third component in the framework is risk mitigation. Risk mitigation involves examining the risks that have been identified and determining which risks can and should be eliminated, as opposed to the risks that are deemed to be acceptable. Part of this process involves coming up with mitigation strategies, such as cyber insurance. For example, if an organization identifies cybersecurity risks that need to be dealt with, then it may choose to integrate security controls into its development lifecycle. Such an organization would likely also put additional baseline security controls in place. | ||
| + | #Reporting and monitoring: The fourth component in the process is risk reporting and monitoring. This essentially means regularly reexamining the risks in order to make sure that the risk mitigation strategies the organization has adopted are having the desired effect. | ||
| + | #Governance: The last component in the process is risk governance. Risk governance is the process of making sure that the risk mitigation techniques that have been adopted are put into place and that the employees adhere to those policies. | ||
| − | |||
| − | |||
| − | Step 2: Select | + | == Risk Management Framework (RMF) Steps<ref>[http://csrc.nist.gov/groups/SMA/fisma/framework.html Risk Management Framework (RMF) Steps]</ref> == |
| − | Select an initial set of | + | The risk-based approach to security control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, Executive Orders, policies, standards, or regulations. The following activities related to managing organizational risk (also known as the Risk Management Framework) are paramount to an effective information security program and can be applied to both new and legacy information systems within the context of the system development life cycle and the Federal Enterprise Architecture: |
| + | *Step 1: Categorize: Categorize the information system and the information processed, stored, and transmitted by that system based on impact analysis. | ||
| + | *Step 2: Select: Select an initial set of baseline security controls for the information system based on the security categorization; tailoring and supplementing the security control baseline as needed based on the organization's assessment of risk and local conditions. | ||
| + | *Step 3: Implement: Implement the security controls and document how the controls are deployed within the information system and environment of operation. | ||
| + | *Step 4: Assess: Assess the security controls using appropriate procedures to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system. | ||
| + | *Step 5: Authorize: Authorize information system operation based upon a determination of the risk to organizational operations and assets, individuals, other organizations, and the Nation resulting from the operation of the information system and the decision that this risk is acceptable. | ||
| + | *Step 6: Monitor: Monitor and assess selected security controls in the information system on an ongoing basis including assessing security control effectiveness, documenting changes to the system or environment of operation, conducting security impact analyses of the associated changes, and reporting the security state of the system to appropriate organizational officials | ||
| − | |||
| − | |||
| − | + | [[File:Rmf.JPG|400px|Risk Management Framework]]<br /> | |
| − | + | source: OWASP | |
| − | |||
| − | |||
| − | + | == History of the RMF<ref>[https://en.wikipedia.org/wiki/Risk_Management_Framework History of the NIST Risk Manahgement Framework]</ref> == | |
| − | + | The E-Government Act of 2002 (Public Law 107-347) entitled FISMA 2002 (Federal Information Security Management Act) was a law passed in 2002 to protect the economic and national security interests of the United States related to information security. | |
| + | Congress later passed FISMA 2014 (Federal Information Security Modernization Act) to provide improvements over FISMA 2002 by: | ||
| + | *Codifying Department of Homeland Security (DHS) authority to administer the implementation of information security policies for non-national security federal Executive Branch systems, including providing technical assistance and deploying technologies to such systems; | ||
| + | *Amending and clarifying the Office of Management and Budget's (OMB) oversight authority over federal agency information security practices; and by | ||
| + | *Requiring OMB to amend or revise OMB A-130 to "eliminate inefficient and wasteful reporting." | ||
| − | + | FISMA required the protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide Confidentiality, Integrity, and Availability. Title III of FISMA 2002 tasked NIST with responsibilities for standards and guidelines, including the development of: | |
| − | + | *Standards are to be used by all federal agencies to categorize all information and information systems collected or maintained by or on behalf of each agency based on the objectives of providing appropriate levels of information security according to a range of risk levels. This task was satisfied by FIPS Publication 199; | |
| + | *Guidelines recommend the types of information and information systems to be included in each category. This task was satisfied by NIST Special Publication 800-60, Volumes 1 and 2; and | ||
| + | *Minimum information security requirements (i.e., management, operational, and technical controls), for information and information systems in each such category. This task was satisfied by the development of FIPS Publication 200. | ||
| + | |||
| + | NIST 800-37 (Risk Management Framework or RMF) was developed to help organizations manage security and privacy risk and to satisfy the requirements of the Federal Information Security Modernization Act of 2014 (FISMA), the Privacy Act of 1974, OMB policies, and Federal Information Processing Standards, among other laws, regulations, and policies. | ||
| Line 56: | Line 70: | ||
== Further Reading == | == Further Reading == | ||
| − | * | + | * [http://csrc.nist.gov/groups/SMA/fisma/framework.html Risk Management Framework (RMF) Overview] |
| − | * | + | *[http://csrc.nist.gov/publications/nistpubs/800-37-rev1/sp800-37-rev1-final.pdf Guide for Applying the Risk Management Framework to Federal Information Systems] |
| − | + | *[http://www.dtic.mil/whs/directives/corres/pdf/851001_2014.pdf Risk Management Framework (RMF) for DoD Information Technology (IT)] | |
| − | * | + | *[http://www.asq509.org/ht/a/GetDocumentAction/i/61054 Overview of RMF - a presentation] |
| + | __NOTOC__ | ||
Revision as of 16:07, 20 January 2023
What is the NIST Risk Management Framework?
The NIST Risk Management Framework (RMF) is a set of criteria that dictate how United States government IT systems must be architected, secured, and monitored. Originally developed by the Department of Defense (DoD), the RMF was adopted by the rest of the US federal information systems in 2010. The RMF is maintained by the National Institute of Standards and Technology (NIST) and provides a solid foundation for any data security strategy.[1]
NIST Special Publication 800-37, "Guide for Applying the Risk Management Framework to Federal Information Systems", developed by the Joint Task Force Transformation Initiative Working Group, transforms the traditional Certification and Accreditation (C&A) process into the six-step Risk Management Framework (RMF). The Risk Management Framework (RMF), provides a disciplined and structured process that integrates information security and risk management activities into the system development life cycle.
Components of the Risk Management Framework (RMF)[2]
There are five components that make up the RMF. These components include the following:
- Identification: The first component in implementing the Risk Management Framework is to identify the risks that the organization faces. These might include strategic, legal, operational, and privacy risks. It is important to note that risk identification is not a one-time process. The risks that an organization faces tend to change over time, so risk assessments will need to be performed on a periodic basis.
- Measurement and assessment: The goal behind the measurement and assessment component is to create a risk profile for each risk that has been identified. There are a number of different ways that organizations might complete the measurement and assessment phase of the process. In some cases, risk measurement might be based on something as simple as how much capital could potentially be lost as a result of the risk. However, in other cases, measuring the potential impact of a risk might be far more difficult. In the field of information security, for example, an organization might attempt to quantify the cost of a security breach compared with the cost of implementing a security mechanism that can help to mitigate the risk.
- Mitigation: The third component in the framework is risk mitigation. Risk mitigation involves examining the risks that have been identified and determining which risks can and should be eliminated, as opposed to the risks that are deemed to be acceptable. Part of this process involves coming up with mitigation strategies, such as cyber insurance. For example, if an organization identifies cybersecurity risks that need to be dealt with, then it may choose to integrate security controls into its development lifecycle. Such an organization would likely also put additional baseline security controls in place.
- Reporting and monitoring: The fourth component in the process is risk reporting and monitoring. This essentially means regularly reexamining the risks in order to make sure that the risk mitigation strategies the organization has adopted are having the desired effect.
- Governance: The last component in the process is risk governance. Risk governance is the process of making sure that the risk mitigation techniques that have been adopted are put into place and that the employees adhere to those policies.
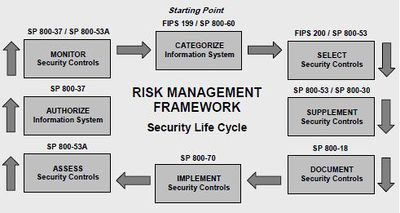
Risk Management Framework (RMF) Steps[3]
The risk-based approach to security control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, Executive Orders, policies, standards, or regulations. The following activities related to managing organizational risk (also known as the Risk Management Framework) are paramount to an effective information security program and can be applied to both new and legacy information systems within the context of the system development life cycle and the Federal Enterprise Architecture:
- Step 1: Categorize: Categorize the information system and the information processed, stored, and transmitted by that system based on impact analysis.
- Step 2: Select: Select an initial set of baseline security controls for the information system based on the security categorization; tailoring and supplementing the security control baseline as needed based on the organization's assessment of risk and local conditions.
- Step 3: Implement: Implement the security controls and document how the controls are deployed within the information system and environment of operation.
- Step 4: Assess: Assess the security controls using appropriate procedures to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system.
- Step 5: Authorize: Authorize information system operation based upon a determination of the risk to organizational operations and assets, individuals, other organizations, and the Nation resulting from the operation of the information system and the decision that this risk is acceptable.
- Step 6: Monitor: Monitor and assess selected security controls in the information system on an ongoing basis including assessing security control effectiveness, documenting changes to the system or environment of operation, conducting security impact analyses of the associated changes, and reporting the security state of the system to appropriate organizational officials
History of the RMF[4]
The E-Government Act of 2002 (Public Law 107-347) entitled FISMA 2002 (Federal Information Security Management Act) was a law passed in 2002 to protect the economic and national security interests of the United States related to information security.
Congress later passed FISMA 2014 (Federal Information Security Modernization Act) to provide improvements over FISMA 2002 by:
- Codifying Department of Homeland Security (DHS) authority to administer the implementation of information security policies for non-national security federal Executive Branch systems, including providing technical assistance and deploying technologies to such systems;
- Amending and clarifying the Office of Management and Budget's (OMB) oversight authority over federal agency information security practices; and by
- Requiring OMB to amend or revise OMB A-130 to "eliminate inefficient and wasteful reporting."
FISMA required the protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide Confidentiality, Integrity, and Availability. Title III of FISMA 2002 tasked NIST with responsibilities for standards and guidelines, including the development of:
- Standards are to be used by all federal agencies to categorize all information and information systems collected or maintained by or on behalf of each agency based on the objectives of providing appropriate levels of information security according to a range of risk levels. This task was satisfied by FIPS Publication 199;
- Guidelines recommend the types of information and information systems to be included in each category. This task was satisfied by NIST Special Publication 800-60, Volumes 1 and 2; and
- Minimum information security requirements (i.e., management, operational, and technical controls), for information and information systems in each such category. This task was satisfied by the development of FIPS Publication 200.
NIST 800-37 (Risk Management Framework or RMF) was developed to help organizations manage security and privacy risk and to satisfy the requirements of the Federal Information Security Modernization Act of 2014 (FISMA), the Privacy Act of 1974, OMB policies, and Federal Information Processing Standards, among other laws, regulations, and policies.
See Also
Risk Analysis
Risk Assessment Framework (RAF)
Risk Management
Risk Assessment
Information Technology Risk (IT Risk)
Enterprise Risk Management (ERM)
Risk IT Framework
Risk Based Testing
Risk-Adjusted Return
Risk-Adjusted Return on Capital (RAROC)
Risk Matrix
Risk Maturity
Risk Maturity Model (RMM)
Risk Mitigation
Enterprise Architecture
Federal Enterprise Architecture Framework (FEA)
IT Governance
IT Governance Framework
References
- ↑ Defining Risk Management Framework Varonis
- ↑ What are the components of the RMF??
- ↑ Risk Management Framework (RMF) Steps
- ↑ History of the NIST Risk Manahgement Framework