Industrial Control System (ICS)
What is Industrial Control System (ICS)[1]
Industrial Control System (ICS) is a general term that encompasses several types of control systems and associated instrumentation used for industrial process control. Such systems can range in size from a few modular panel-mounted controllers to large interconnected and interactive distributed control systems with many thousands of field connections. Systems receive data received from remote sensors measuring process variables (PVs), compare the collected data with desired setpoints (SPs), and derive command functions that are used to control a process through the final control elements (FCEs), such as control valves. Larger systems are usually implemented by supervisory control and data acquisition (SCADA) systems, distributed control systems (DCS), and programmable logic controllers (PLCs), though SCADA and PLC systems are scalable down to small systems with few control loops. Such systems are extensively used in industries such as chemical processing, pulp, and paper manufacture, power generation, oil and gas processing, and telecommunications.
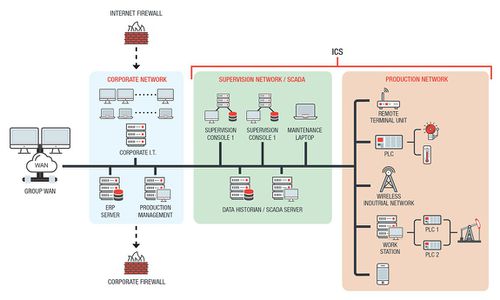
Components of an Industrial Control System (ICS) Environment[2]
IT and OT: Operational Technology (OT) variables include the hardware and software systems that monitor and control physical devices in the field. OT tasks vary with every industry. Devices that monitor the temperature in industrial environments are examples of OT devices The convergence of IT and OT provides enterprises with greater integration and visibility of the supply chain– which includes their critical assets, logistics, plans, and operation processes. Having a good view of the supply chain helps organizations remain competitive. On the flip side, however, the convergence of OT and IT allows easier access to these two components that are targets of cybercriminals. In many organizations, OT infrastructure is at best poorly protected against cyber attacks.
- Programmable Logic Controller (PLC): This is a type of hardware that is used in both DCS and SCADA systems as a control component of an overall system. It also provides local management of processes being run through feedback control devices such as sensors and actuators. In SCADA, a PLC provides the same functionality as Remote Terminal Units (RTU). In DCS, PLCs are used as local controllers within a supervisory control scheme. PLCs are also implemented as primary components in smaller control system configurations.
- Remote Terminal Unit (RTU): An RTU is a microprocessor-controlled field device that receives commands and sends information back to the MTU.
- Control Loop: Every control loop consists of hardware such as PLCs and actuators. The control loop interprets signals from sensors, control valves, breakers, switches, motors, and other similar devices. The variables measured by these sensors are then transmitted to the controller to carry out a task and/or complete a process.
- Human Machine Interface (HMI): A graphical user interface (GUI) application that allows interaction between the human operator and the controller hardware. It can also display status information and historical data gathered by the devices in the ICS environment. It is also used to monitor and configure setpoint, and control algorithms, and adjust and establish parameters in the controllers.
- Remote Diagnostics and Maintenance: This is a term used to identify, prevent, and recover from abnormal operations or failures.
- Control Server: A control server hosts the DCS or PLC supervisory control software and communicates with lower-level control devices.
- SCADA Server or Master Terminal Unit (MTU): This is a device that issues commands to RTUs in the field.
- Intelligent Electronic Device (IED): A smart device capable of acquiring data, communicating with other devices, and performing local processing and control. The use of IEDs in control systems like SCADA and DCS allows for controls at the local level to be done automatically.
- Data Historian: A data historian is a centralized database for logging all process information within an ICS environment and then exporting data to the corporate IS. The data gathered is then used for process analysis, statistical process control, and enterprise-level planning.
Industrial Control System (ICS) Security[3]
Industrial control systems (ICS) are often a sitting target for cybercriminals. The majority of these systems monitor complex industrial processes and critical infrastructures that deliver power, water, transport, manufacturing, and other essential services. There was once a time when these systems were essentially dumb, and those that were computerized used protocols that were proprietary to the system and lived on networks protected by the outside world. The world has changed and as a result, the majority of industrial control systems in operation today connect directly or indirectly to the internet. This introduces them to vulnerabilities like any other connected system. The difference is that downtime or infiltration of an ICS network could result in massive outages, hundreds of thousands of impacted users, and even a national disaster. ICS security is a security framework that protects these systems against accidental or intentional risks.
Securing industrial systems is no trivial task. Most were built before the first cyber threat surfaced and did not have built-in external security controls factored into their design. Understanding some of the most common industrial control system threats is the first step that any industrial organization can take to protect its network.
- External Threats and Targeted Attacks: When you consider that industrial control systems often come under the umbrella of chemical engineering, manufacturing, distribution, and healthcare, it is little wonder that these systems are often targeted by terrorist groups, hacktivists, and other groups with malicious intent. The aim of politically motivated attacks is usually focused on causing physical damage or operational disruption, while industrial espionage attacks will be more focused on stealing or damaging Intellectual Property (IP).
- Internal Threats: Insider threats are well documented when it comes to IT networks, but they can also pose a huge risk to industrial networks. From disgruntled employees to contractors with an ax to grind, the internal threat is real. Most ICS networks require little to no authentication or encryption that controls or restricts user activity. This means that any insider will generally have unlimited access to any device that exists on the network, including SCADA applications and other critical components. Systems that have been upgraded to connect to a digital interface can be easily compromised by malware or a USB device used to download sensitive data.
- Human Error: It is human nature to make mistakes. However, when mistakes are made on an industrial control systems network they can be costly and have a huge impact on operations and reputation. In fact, in many cases, human error is considered the biggest threat to an ICS network. Human errors can include making incorrect configurations, PLC programming errors, or forgetting to monitor key metrics or alerts.
See Also
Advanced Business Application Programming (ABAP)
Advanced Distribution Management Systems (ADMS)
Advanced Distribution Protection and Restoration Devices
Advanced Metering Infrastructure (AMI)
Advanced Technology