Information Technology Controls (IT Controls)
Definition of Information Technology Controls (IT Controls)[1]
Information Technology Controls or IT Controls are essential to protect assets, customers, partners, and sensitive information; demonstrate safe, efficient, and ethical behavior; and preserve brand, reputation, and trust. In today’s global market and regulatory environment, these things are too easy to lose.
IT controls do not exist in isolation. They form an interdependent continuum of protection, but they also may be subject to compromise due to weak links. IT controls are subject to error and management override, range from simple to highly technical, and exist in a dynamic environment. IT controls have two significant elements:
- the automation of business controls (which support business management and governance) and
- control of the IT environment and operations (which support the IT applications and infrastructures).
The Importance of IT Controls[2]
The role of information technology (IT) control and audit has become a critical mechanism for ensuring the integrity of information systems (IS) and the reporting of organization finances to avoid and hopefully prevent future financial fiascos such as Enron and WorldCom. Global economies are more interdependent than ever and geopolitical risks impact everyone. Electronic infrastructure and commerce are integrated in business processes around the globe. The need to control and audit IT has never been greater. Initially, IT auditing (formerly called electronic data processing (EDP), computer information systems (CIS), and IS auditing) evolved as an extension of traditional auditing. At that time, the need for an IT audit function came from several directions
- Auditors realized that computers had impacted their ability to perform the attestation function.
- Corporate and information processing management recognized that computers were key resources for competing in the business environment and similar to other valuable business resource within the organization, and therefore, the need for control and auditability is critical.
- Professional associations and organizations, and government entities recognized the need for IT control and auditability.
From a worldwide perspective, IT processes need to be controlled. From a historical standpoint, much has been published about the need to develop skills in this field. In its 1992 discussion paper, "Minimum Skill Levels in Information Technology for Professional Accountants,"and its 1993 final report, "The Impact of Information Technology on the Accountancy Profession," the International Federation of Accountants (IFAC) acknowledged the need for better university-level education to address growing IT control concerns and issues. From this, it has published more recent guidance and information. The Institute of Internal Auditors (IIA) 1992 document "Model Curriculum for Information Systems Auditing" was developed to define the knowledge and skills required by internal auditors to be proficient in the information age of the 1990s and beyond.
Owing to the rapid diffusion of computer technologies and the ease of information accessibility, knowledgeable and well-educated IT auditors are needed to ensure that effective IT controls are in place to maintain data integrity and manage access to information. Globally, private industry, professional associations, and organizations such as International Federation of Information Processing (IFIP), Association for Computing Machinery (ACM), Association of Information Technology Professionals (AITP), Information Systems Security Association (ISSA), and others have recognized the need for more research and guidance as identified in Appendix III. Control-oriented organizations such as the American Institute of Certified Public Accountants (AICPA), the Canadian Institute of Chartered Accountants (CICA), IIA, Association of Certified Fraud Examiners (ACFE), and others have issued guidance and instructions and supported studies/research in this area. Since 1996, The Colloquium for Information Systems Security Educators (CISSE) has been a leading proponent for implementing the course of Instruction in information security (InfoSec) and Information Assurance in education The need for improved control over IT has been advanced over the years in earlier and continuing studies by the AICPA's Committee of Sponsoring Organizations of the Treadway Commission (COSO), International Organization for Standardization (ISO) issuance of ISO 9000 and ISO 17799 and follow-on amendments, OECD's "Guidelines for the Security of IS by the Organization for Economic Cooperation and Development (OECD)," IIA's "Systems Auditability and Control (SAS) Report," and the U.S. President's Council on Integrity and Efficiency in Computer Audit Training Curriculum. The most recent addition to these major studies is the aforementioned CoBiT research. Essentially, technology has impacted three significant areas of the business environment:
- It has impacted what can be done in business in terms of information and as a business enabler. It has increased the ability to capture, store, analyze, and process tremendous amounts of data and information, which has increased the empowerment of the business decision maker. Technology has also become a primary enabler to various production and service processes. It has become a critical component to business processes. There is a residual effect in that the increased use of technology has resulted in increased budgets, increased successes and failures, and increased awareness of the need for control.
- Technology has significantly impacted the control process. Although control objectives have generally remained constant, except for some that are technology specific, technology has altered the way in which systems should be controlled. Safeguarding assets, as a control objective, remains the same whether it is done manually or is automated. However, the manner by which the control objective is met is certainly impacted.
- Technology has impacted the auditing profession in terms of how audits are performed (information capture and analysis, control concerns) and the knowledge required to draw conclusions regarding operational or system effectiveness, efficiency and integrity, and reporting integrity. Initially, the impact was focused on dealing with a changed processing environment. As the need for auditors with specialized technology skills grew, so did the IT auditing profession.
Organizations today operate in a dynamic global multi-enterprise environment with team-oriented collaboration and place very stringent requirements on the telecommunications network. The design of such systems is complex and management can be very difficult. Organizations are critically dependent on the timely flow of accurate information. A good way to view how stringent the network requirements are is to analyze them in terms of the quality of the telecommunications service. Perhaps, two examples of the world's dependency on IT come as a result of two reported events in the past where IT failure impacted world commerce and communications. In 1998, an AT&T major switch failed due to two software errors and a procedural error, causing communications at that switch to become overloaded and making customers using credit cards unable to access their funds for 18 hours. In another 1998 event, a communication satellite went into an uncontrollable rotation causing pager communication systems worldwide to be "useless," and those companies using this technology for E-account transaction and verification were unable to process credit card information for 24 hours, thus causing their customers to pay cash for their transactions. The disruption of the paging services caused severe impact to services provided by both private and governmental organizations that depended on this communication. Hence the need for a control structure, which provides assurances of integrity, reliability, and validity, to be designed, developed, and implemented.
The financial scandals involving Enron and Arthur Andersen LLP, and others generated a demand for the new legislation to prevent, detect, and correct such aberrations. In addition to this, the advancements in network environments technologies have resulted in bringing to the forefront issues of security and privacy that were once only of interest to the legal and technical expert but which today are topics that affect virtually every user of the information superhighway. The Internet has grown exponentially from a simple linkage of a relative few government and educational computers to a complex worldwide network that is utilized by almost everyone from the terrorist who has computer skills to the novice user and everyone in between. Common uses for the Internet include everything from marketing, sales, and entertainment purposes to e-mail, research, commerce, and virtually any other type of information sharing.
Unfortunately, as with any breakthrough in technology, advancements have also given rise to various new problems that must be addressed, such as security and privacy. These problems are often being brought to the attention of IT audit and control specialists due to their impact on public and private organizations. Current legislation and government plans will effect the online community and, along with the government's role in the networked society, will have a lasting impact in future business practices.
IT and information security are integral parts of the IT's internal controls. The computer is changing the world. Business operations are also changing, sometimes very rapidly, because of the fast continuing improvement of technology. Events such as September 11, 2001, and financial upheavals from corporate scandals such as Enron and Global Crossing have resulted in increased awareness. Yes, IT controls are very important. Today, people are shopping around at home through networks. People use "numbers" or accounts to buy what they want via shopping computers. These "numbers" are "digital money," the modern currency in the world. Digital money will bring us benefits as well as problems. One major benefit of digital money is its increased efficiency. However, it will also create another problem for us. "Security" is perhaps the biggest factor for individuals interested in making online purchases by using digital money. Also, it must be remembered that vigilance needs to be maintained over those who use the Internet for illegal activities, including those who are now using it for scams, crime, and covert activities that could potentially cause loss of life and harm to others. IT control and security is everyone's business.
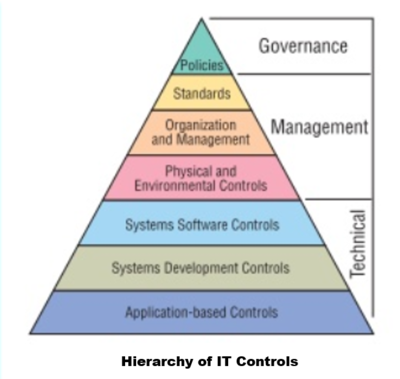
The Hierarchy of IT Controls[3]
Individual controls within an organization can be classified within the hierarchy of IT controls — from the overall highlevel policy statements issued by management and endorsed by the Board down to the specific control mechanisms incorporated into application systems. The Figure below – Hierarchy of IT Controls represents a logical “top-down” approach both when considering controls to implement and when determining areas on which to focus internal audit resources during reviews of the entire IT operating environment. The different elements of the hierarchy are not mutually exclusive; they connect with each other and often overlap and intermingle. Each of the control types within the hierarchy are described below.
- Policies: All organizations need to define their goals and objectives through strategic plans and policy statements. Without clear statements of policy and standards for direction, organizations can become disoriented and perform ineffectively. Because technology is vital to virtually all organizations, clear policy statements regarding all aspects of IT should be devised and approved by management, endorsed by the Board, and communicated to staff. Many different policy statements can be required depending on the organization’s size and the extent to which it deploys IT. For smaller organizations, a single policy statement may be sufficient — provided it covers all relevant areas. Larger organizations often will require more detailed and specific policies.
- Standards: The organization should have an IT blueprint that supports its overall strategy and sets the tone for the resultant IT policies and standards. The standards define ways of working to achieve the objectives of the organization. Adopting and enforcing standards promotes efficiency and ensures consistency in the IT operating environment. Large organizations with significant resources are in a position to devise their own standards, but smaller organizations may not have sufficient resources. There are many sources of information on standards and best practice that smaller organizations may considere using. As with policies, written standards should be approved by management and made available to everyone who implements them.
- Organization and management play a major role in the whole system of IT control in addition to every aspect of an organization’s operations. An appropriate organization structure allows lines of reporting and responsibility to be defined and effective control systems to be implemented. Important controls typically could include segregation of incompatible duties, financial controls, and change management.
- Physical and Environmental Controls: IT equipment represents a considerable investment for many organizations. It must be protected from accidental or deliberate damage or loss. Physical and environmental controls, originally developed for large data centers that house mainframe computers, are equally important in distributed client-server and Web-based systems. Although the equipment commonly used today is designed for ease of use in a normal office environment, its value to the business and the cost and sensitivity of applications running business processes can be significant. All equipment must be protected, including the servers and workstations that allow staff access to the applications. When considering physical and environmental security, it is also appropriate to consider contingency planning. What will the organization do if there is a fire or flood or if any other threat manifests itself? How will the organization continue its operations? This type of planning goes beyond merely providing for alternative IT processing power to be available and routine backup of production data; it must consider the logistics and coordination needed for the full scope of business activity. Finally, history consistently demonstrates that business continuity planning that has not been tested successfully in a realistic simulation is not reliable.
- Systems Software Controls: Systems software products enable the IT equipment to be used by the application systems and users. These products include operating systems (e.g., Windows and UNIX), network and communications software, firewalls, antivirus products, and database management systems (DBMS) (e.g., Oracle and DB2). IT audit specialists should assess controls in this area. Small organizations are unlikely to have the resources to employ such specialists and should consider using external resources. Whether IT auditors are employed or outsourced, they require a highly specific set of knowledge. Much of this knowledge can come from experience, but such knowledge must be updated constantly to remain current and useful. Systems software can be highly complex and can apply to components and appliances within the systems and network environment. Software may be configured to accommodate highly specialized needs and normally requires a high degree of specialization to securely maintain it. Configuration techniques can control logical access to the applications, although some application systems contain their own access controls and may provide an opening for unauthorized users to break into a system. Configuration techniques also provide the means to enforce segregation of duties, generate specialized audit trails, and apply data integrity controls through access control lists, filters, and activity logs.
- Systems Development and Acquisition Controls: Organizations rarely adopt a single methodology for all system acquisitions or development. Methodologies are chosen to suit the particular circumstances. The IT auditor should assess whether the organization uses a controlled method to develop or acquire application systems and whether it delivers effective controls over and within the applications and data they process. By examining application development procedures, the auditor can gain assurance that application controls are adequate. Some basic control issues should be addressed in all systems development and acquisition work. Where systems development is outsourced, the outsourcer or provider contracts should require similar controls. Project management techniques and controls should be part of the development process — whether developments are performed in-house or are outsourced. Management should know whether projects are on time and within budget and that resources are used efficiently. Reporting processes should ensure that management understands the current status of development projects and does not receive any surprises when the end product is delivered.
- Application Controls: The objective of controls over application systems is to ensure that:
- All input data is accurate, complete, authorized, and correct.
- All data is processed as intended.
- All data stored is accurate and complete.
- All output is accurate and complete.
- A record is maintained to track the process of data from input to storage and to the eventual output.
- Reviewing application controls traditionally has been the realm of the specialist IT auditor. However, because application controls now represent a large percentage of business controls, they should be a key concern of every internal auditor. There are several types of generic controls that should exist in any application.
- Input controls: These controls are used mainly to check the integrity of data entered into a business application, whether the source is input directly by staff, remotely by a business partner, or through a Web-enabled application. Input is checked to ensure that it remains within specified parameters.
- Processing controls: These controls provide automated means to ensure processing is complete, accurate, and authorized.
- Output controls: These controls address what is done with the data. They should compare results with the intended result and check them against the input.
- Integrity controls: These controls can monitor data in process and/or storage to ensure that data remains consistent and correct.
- Management trail: Processing history controls, often referred to as an audit trail, enable management to track transactions from the source to the ultimate result and to trace backward from results to identify the transactions and events they record. These controls should be adequate to monitor the effectiveness of overall controls and identify errors as close as possible to their sources.
Categories of IT Controls[4]
IT controls are often described in two categories:
- IT General Controls (ITGC): ITGC represent the foundation of the IT control structure. They help ensure the reliability of data generated by IT systems and support the assertion that systems operate as intended and that output is reliable. ITGC usually include the following types of controls:
- Control environment, or those controls designed to shape the corporate culture or "tone at the top."
- Change management procedures - controls designed to ensure the changes meet business requirements and are authorized.
- Source code/document version control procedures - controls designed to protect the integrity of program code
- Software development life cycle standards - controls designed to ensure IT projects are effectively managed.
- Logical access policies, standards and processes - controls designed to manage access based on business need.
- Incident management policies and procedures - controls designed to address operational processing errors.
- Problem management policies and procedures - controls designed to identify and address the root cause of incidents.
- Technical support policies and procedures - policies to help users perform more efficiently and report problems.
- Hardware/software configuration, installation, testing, management standards, policies and procedures.
- Disaster recovery/backup and recovery procedures, to enable continued processing despite adverse conditions.
- Physical security - controls to ensure the physical security of information technology from individuals and from environmental risks.
- IT Application Controls: IT application or program controls are fully automated (i.e., performed automatically by the systems) designed to ensure the complete and accurate processing of data, from input through output. These controls vary based on the business purpose of the specific application. These controls may also help ensure the privacy and security of data transmitted between applications. Categories of IT application controls may include:
- Completeness checks - controls that ensure all records were processed from initiation to completion.
- Validity checks - controls that ensure only valid data is input or processed.
- Identification - controls that ensure all users are uniquely and irrefutably identified.
- Authentication - controls that provide an authentication mechanism in the application system.
- Authorization - controls that ensure only approved business users have access to the application system.
- Input controls - controls that ensure data integrity fed from upstream sources into the application system.
- Forensic controls - control that ensure data is scientifically correct and mathematically correct based on inputs and outputs
Current IT Standard/Control Frameworks and Models
Several popular IT Governance and Standards Frameworks are displayed in Figure 1: COSO Internal Control Integrated Framework; COBIT (Control Objectives for Information and Related Technology); ITIL (Information Technology Infrastructure Library), and ISO 27001/9000. While no one framework or model encompasses all of the possible IT controls, collectively they cover the “what, how, and scope” of IT Governance — albeit with some duplication and overlap.
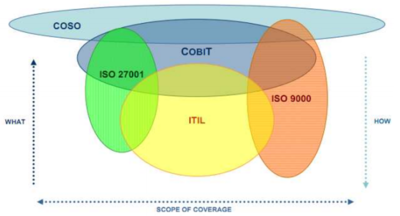 source: Elana Bailey, Jack D. Becker
source: Elana Bailey, Jack D. Becker
COBIT[5]
Short for Control Objectives for Information and Related Technologies, COBIT was first developed to guide IT governance and management. It's scope is unique from most frameworks in that it focuses narrowly on security, risk management, and governance. If you’re looking to streamline business processes, sync IT with business needs, alter your IT infrastructure, or manage the multi-cloud, COBIT isn’t the answer. But with most companies relying enormously on IT for business success – sometimes the IT itself is the product – COBIT is essential to developing, controlling, and maintaining risk and security for enterprises around the world, regardless of your industry.
COSO[6]
The Committee of Sponsoring Organizations were charged by the Treadway Commission to develop an integrated guidance on Internal Control. As a result of this, a framework for designing, implementing and evaluating internal control for organizations was released. The COSO Framework was designed to help businesses establish, assess and enhance their internal control. The importance of Internal Control in the Operations and Financial Reporting of an entity cannot be over-emphasized as the existence or the absence of the process determines the quality of output produced in the Financial Statements. A present and functioning Internal Control process provides the users with a “reasonable assurance” that the amounts presented in the Financial Statements are accurate and can be relied upon for informed decision making. The COSO Integrated Framework for Internal Control has five (5) components which include:
- Control Environment: The control environment is the set of standards, processes, and structures that provide the basis for carrying out internal control across the organization
- Risk Assessment: Risk assessment involves a dynamic and iterative process for identifying and assessing risks to the achievement of objectives.
- Control Activities: Control activities are the actions established through policies and procedures that help ensure that management’s directives to mitigate risks to the achievement of objectives are carried out.
- Information and Communication: Communication is the continual, iterative process of providing, sharing and obtaining necessary information.
- Monitoring Activities: Ongoing evaluations, separate evaluations or some combination of the two are used to ascertain whether each odf the five components of internal control, including controls to effect the principles, within each component, is present and functioning.
ITIL[7]
Successfully aligning customer demand and business needs with technology services offers organizations a unique opportunity to enhance efficiency, improve productivity, and increase value. Aligned organizational needs and services can lay the foundation for establishing a competitive edge and achieving business success. The ITIL® framework offers a set of ITSM best practices aids organizations in aligning IT service delivery with business goals. ITIL, or Information Technology Infrastructure Library, is a well-known set of IT best practices designed to assist businesses in aligning their IT services with customer and business needs. Services include IT related assets, accessibility, and resources that deliver value and benefits to customers. ITIL framework objectives include the delivery of valuable service offerings, as well as meeting customer needs, and achieving business goals of a given organization. Despite the individuality of each organization, ITIL provides guidelines for achieving these objectives and measuring success with KPIs. While it is most common to see ITIL implemented among large organizations, ITIL processes can bring value to small and mid-size organizations. Smaller organizations often implement only a subset of ITIL processes that are perceived to offer the most significant or tangible return on effort.
ISO 27001[8]
ISO 27000|ISO 27001 is the international standard that describes best practice for an ISMS (information security management system). The Standard takes a risk-based approach to information security. This requires organisations to identify information security risks and select appropriate controls to tackle them. Annex A of ISO 27001 provides an essential tool for managing security. It provides a list of security controls to be used to improve the security of information. As you can see from the list below, ISO 27001 is not fully focused on IT, while IT is very important, IT on its own cannot protect information. Instead, bringing together Physical security, HR management, organisational issues and legal protection, along with IT are required to secure the information. A useful way to understand Annex A is to think of it as a catalogue of security controls – based on your risk assessments, you should then select the ones that are applicable to your organisation and tie into your statement of applicability. The 14 control sets of Annex A:
- A.5 Information security policies (2 controls): how policies are written and reviewed.
- A.6 Organisation of information security (7 controls): the assignment of responsibilities for specific tasks.
- A.7 Human resource security (6 controls): ensuring that employees understand their responsibilities prior to employment and once they’ve left or changed roles.
- A.8 Asset management (10 controls): identifying information assets and defining appropriate protection responsibilities.
- A.9 Access control (14 controls): ensuring that employees can only view information that’s relevant to their job role.
- A.10 Cryptography (2 controls): the encryption and key management of sensitive information.
- A.11 Physical and environmental security (15 controls): securing the organisation’s premises and equipment.
- A.12 Operations security (14 controls): ensuring that information processing facilities are secure.
- A.13 Communications security (7 controls): how to protect information in networks.
- A.14 System acquisition, development and maintenance (13 controls): ensuring that information security is a central part of the organisation’s systems.
- A.15 Supplier relationships (5 controls): the agreements to include in contracts with third parties, and how to measure whether those agreements are being kept.
- A.16 Information security incident management (7 controls): how to report disruptions and breaches, and who is responsible for certain activities.
- A.17 Information security aspects of business continuity management (4 controls): how to address business disruptions.
- A.18 Compliance (8 controls): how to identify the laws and regulations that apply to your organisation.
ISO 9000[9]
ISO 9000 is a family of internationally accepted standards that are used to measure the quality management system (QMS) followed by an organization. The main purpose of the ISO 9000 standard is to provide a time-tested framework to help companies establish and follow a systematic approach for managing organizational processes for rendering consistent quality. ISO 9000 is often used to refer to a family of three standards:
- ISO 9000:2005 - Fundamentals and vocabulary
- ISO 9001:2015 - Requirements
- ISO 9004:2000 - Guidelines for performance improvement
See Also
References
- ↑ Definition - What Does Information Technology Controls (IT Controls) Mean? IIA
- ↑ Why Are Information Technology Controls and Audit Important? IT Today
- ↑ The Hierarchy of IT Controls David A Richards et al.
- ↑ The Two Categories of IT Controls Wikipedia
- ↑ COBIT BMC
- ↑ COSO Deloitte
- ↑ ITIL Cherwell
- ↑ ISO 27001 itgovernance.co.uk
- ↑ ISO 9000 ISO 9001 Checklist
Further Reading
- General IT Controls (GITC) Risk and Impact Deloitte Risk Advisory
- Guide to the Sarbanes-Oxley Act: IT Risks and Controls Protiviti
- The Increasing Importance of IT 'Controls' Datamation