Network Infrastructure
What is network infrastructure?
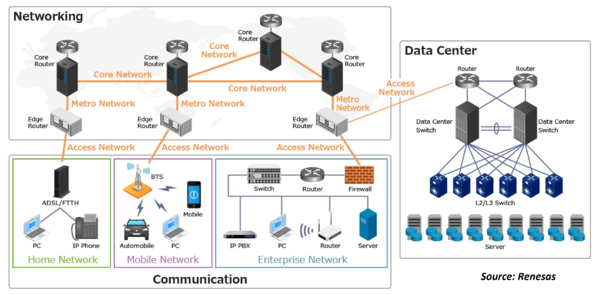
Network Infrastructure refers to all of the resources of a network that make network or internet connectivity, management, business operations, and communication possible. Network infrastructure comprises hardware and software, systems and devices, and it enables computing and communication between users, services, applications, and processes. Anything involved in the network, from servers to wireless routers, comes together to make up a system’s network infrastructure.
Network infrastructure is a critical component of any corporate organization. It serves as the backbone that connects users, services, applications, and processes to each other. It helps ensure a secure and clean experience for all users and provides an efficient way to access data. Network infrastructure also enables organizations to stay connected with customers, partners, suppliers as well as the Internet. Without it, businesses would not be able to effectively carry out their operations; hence its importance cannot be underestimated. Proper planning and design are necessary for optimal network performance in order to successfully support corporate companies’ needs. Any business, whether small or large, needs a reliable network infrastructure to function properly. This includes the hardware and software components that make up the network, as well as the people who manage and support it.
What are the components of network infrastructure?
Network infrastructure is essential in running a successful corporate organization. Network infrastructure is composed of components that can be broken down into three categories: network hardware, network software, and network services. Network hardware includes routers, switches, and physical servers which are used to interconnect devices within the network. Network software includes firewalls and intrusion detection systems that help keep the system secure from unauthorized access or malicious attacks. Network services such as DNS servers provide linkages between networks for easier communication and operation of applications across multiple networks. Edge devices including VPNs and IDSs enhance security by providing additional protection against threats from external sources. All these components work together to provide a reliable, secure, and efficient infrastructure that supports corporate operations.
What are the different types of network infrastructure?
- Local area networks (LANs): A local area network (LAN) is a type of computer network infrastructure that connects multiple devices within a small geographic area, such as an office or building. The LAN uses switches or a stack of switches to link each device together. Each device in the network has its own private IP address, enabling it to exchange data with other connected devices. Benefits of using a LAN include increased security, improved performance due to dedicated bandwidth usage, and shared resources among users in the same area.
- Wide area networks (WANs): A Wide Area Network (WAN) is a network that covers a broad geographical area and typically spans greater distances than those found in Local Area Networks (LANs). WANs are designed to connect computers, other devices, and networks located in different regions, allowing them to communicate with each other. WANs rely on technologies such as leased lines, frame relays, ISDNs, or ATMs for their operations. Companies of various sizes use WANs to facilitate long-distance communication between their offices and with customers or business partners.
- Wireless local area networks (WLANs): A WLAN is a type of network infrastructure that utilizes radio waves to connect devices in a localized area. Unlike other types of network infrastructure, WLANs rely on radio waves rather than wires or cables to enable communication between devices. A WLAN controller manages the access points which are used to allow wireless devices to connect with the company's network and the architecture is designed for power saving and prolonging battery life for mobile equipment. Additionally, IEEE 802.11 supports three different topologies for these networks – IBSS (independent basic service set), BSS (basic service set), and ESS (extended service set).
- Metropolitan area networks (MANs): A Metropolitan Area Network (MAN) is a type of computer network that is larger than a typical Wide Area Network (WAN) and covers a wider area. It connects devices in a large geographical area and can act as an internet service provider. Unlike Local Area Networks (LANs), which are private and connect computers in limited, localized areas, MAN networks span greater distances, such as across cities or countries.
- Virtual private networks (VPNs): A Virtual Private Network (VPN) is a service that provides users with the ability to connect to a private network over an untrusted network, such as the internet. This technology can be used in order to protect data and communications from malicious actors. VPNs are often used by corporate companies in order to secure their networks and maintain their privacy, as well as for providing access to remote employees. To ensure maximum security, multiple approaches must be taken when designing an effective infrastructure security plan. Additionally, wireless networks are generally less secure than hardwired ones and proper use of VPNs can help defend against potential network infiltration attempts.
- Storage area networks (SANs): A SAN, or storage area network, is a type of network infrastructure that enables efficient and reliable data storage and transfer. It does this by striping or mirroring the data for improved performance, as well as providing fast I/O rates for high availability. Routers, switches, load balancers, and DNS are all components of a SAN; however, it differs from other types of network infrastructure in that it also requires regular backups in order to minimize downtime. A properly configured SAN can make an immense difference to the performance and reliability of any corporate company's network infrastructure.
- Network-attached storage (NAS): Network Attached Storage (NAS) is a type of storage that is connected to a network and can be used to store files. It differs from other types of network infrastructure, such as routers, switches, firewalls, load balancers, and storage area networks (SANs), in that NAS offers direct access to the stored data from any device on the network. This makes it much more convenient for users than traditional server-based file storage solutions. Additionally, NAS eliminates the need for complex configuration and maintenance of physical servers as all components are centrally managed by the NAS system itself.
- Content delivery networks (CDNs): A content delivery network (CDN) is a system used by publishers to deliver content such as images and videos from a data center that is close to each user in order to reduce latency. It uses three types of computing endpoints: client-server, endpoint, and proxy server. The proxy server works as a middleman between the clients and the internet while reverse proxies work in the opposite direction, serving requests from the internet directly to clients.
- Cloud computing networks: Cloud computing networks are different from other types of networks in that they are designed to be more robust and handle more demanding workloads. With cloud computing networks, businesses can reduce the time it takes to investigate alerts and respond to incidents, improve their cloud infrastructure and visibility, as well as the performance of their contact centers. Additionally, cloud computing networks allow for easier and faster deployment of applications than other types of networks. Companies looking for a way to meet network infrastructure challenges should consider utilizing Parallels RAS solutions.
- Software-defined networks (SDN): SDN (Software Defined Networking) is a newer type of network infrastructure that is designed to make networks more dynamic, manageable, and cost-effective. It allows network administrators to programmatically control and oversee network behavior dynamically, as well as manage devices and data in a more flexible and efficient way. In comparison to traditional networking platforms such as LAN or WAN infrastructures, SDN provides additional benefits of enhanced security, agility, and cost-efficiency. It can also be used to improve the performance of cloud-based applications. SDN works by utilizing software tools that provide centralized control over the entire network from one source; this helps with overall management by providing visibility into the operations occurring across different parts of the system.
What is the importance of a well-managed network infrastructure for corporate companies?
A well-managed network infrastructure can support corporate companies by helping them avoid costly downtime incidents and protect data. The rise in remote work has put more strain on networks, making it essential to invest in a reliable and secure infrastructure. By taking the time to properly manage the network, companies can ensure that their systems are always up-to-date, secure, and running optimally. This helps reduce costs associated with unexpected outages or data loss due to poor maintenance and support of the network infrastructure.
How can proper support help maintain your network infrastructure?
Step 1: Centralize Traffic: The first step in ensuring proper support for network infrastructure is centralizing traffic. This involves avoiding duplicate data and using the right tools to send the right data where it needs to go.
Step 2: Dealing With Duplicate Data: Duplicate data can have a significant impact on a company's network infrastructure. When dealing with duplicate data, issues such as decreased security and performance can arise. To mitigate the risks associated with this type of data, it is important to centralize traffic, manage data with tools such as servers or cloud storage, and route the right type of information to the correct tool. Additionally, considerations should be taken when choosing software solutions designed to detect potential threats in order to prevent a slowdown in security processing time due to these types of problems.
Step 3: Sending the Right Data to the Right Tool: When troubleshooting network issues, it is important to send the right data to the right tool in order to ensure efficient and cost-effective problem resolution. Failing to do so can lead to ineffective use of cyber security tools and providers, as well as duplicate data being sent out which can further complicate matters. Sending the wrong data or sending it out multiple times can lead to wasted time and resources that could be better spent on resolving an issue.
Step 4: Invest in the Right Network Infrastructure: Investing in the right network infrastructure can bring numerous benefits to a corporate company. It can increase business efficiency and performance, as well as give them the agility and responsiveness they need to keep up with changing business demands. Having a good network infrastructure in place also ensures that an organization will have the scalability they require for future growth and success. Moreover, having the right tools and solutions in place helps make it easier to manage and maintain their network infrastructure effectively.
Step 5: Upgrade Your Network Protocols: Upgrading network protocols is essential for maintaining a reliable and efficient network infrastructure. With the increasing demand for wireless devices and data, newer technologies are needed to ensure that the bandwidth requirements of these devices are met. By upgrading their protocols, companies can ensure that their networks can keep up with ever-changing demands while also ensuring greater performance and reliability. Additionally, improved protocols allow organizations to take advantage of new technologies such as Wi-Fi 6 which quadruples the bandwidth per access point making it ideal for supporting new applications or improving service to older ones.
Step 6: Choose the Right Linux Server Distros: Selecting the right Linux server distros to maintain a network infrastructure can provide several benefits. Using a full-stack firewall to secure data centers and improve resilience is one of these benefits. Additionally, path-based routing can be used to direct web traffic more efficiently, reducing overall load times while keeping data secure. Finally, these distros often include built-in tools for automated system management as well as monitoring and support services for quicker problem resolution.
Step 7: Choose the Right Hosting Control Panel: A hosting control panel is a tool that helps administrators to manage and monitor their Azure resources. It provides an easy-to-use interface for managing the server's operation, including tasks such as deployment or maintenance work. Additionally, it helps to keep track of the network infrastructure in Azure with its documentation features which allow administrators to quickly troubleshoot and fix issues.
Step 8: Invest in the Right Web Hosting Services: It is important for corporate companies to invest in the right web hosting services in order to improve application resilience and minimize cost. These costs include electricity, cooling, and other expenses related to running these services. Investing in the right type of web hosting can help ensure maximum efficiency and cost savings while enabling the enhanced performance of applications.
Step 9: Invest in the Right Mail Server: It is important for corporate companies to invest in the right Linux mail server in order to ensure the secure delivery of emails and provide robust security measures against potential attacks. By investing in a server that meets their specific needs, organizations can be sure that their network infrastructure will have the necessary tools and capabilities needed to support their operations.
Step 10: Get the Latest Software Updates: The significance of getting the latest software updates for maintaining network infrastructure is that it ensures security and stability, preventing malware, viruses, and other cyber threats from infiltrating the system. Additionally, it reduces the risk of data loss due to out-of-date applications or hardware components. By providing timely software updates, companies can ensure their networks remain up-to-date with industry trends and developments which can help them stay competitive in their respective markets.
Step 11: Invest in the Right Web Browser: Investing in the right web browser can bring a number of benefits, such as increased security and privacy, access to more powerful tools and plugins, and better performance. Additionally, users can take advantage of the wide selection of browsers available on Linux that are designed specifically for different tasks. For example, Google Chrome offers a fast browsing experience while Firefox is best suited for developers who need additional tools like Web Development tools or debugging features. Furthermore, investing in the right Linux web browser can increase compatibility with certain websites or applications that are not supported on other platforms. Finally, many popular browsers such as LastPass offer features like secure data storage and authentication which help make browsing even more secure.
Step 12: Invest in the Right CentOS Alternatives: It is important to invest in the right CentOS alternatives because they can help reduce the risk of data breaches by providing a full-stack firewall for secure data centers, as well as allowing for extended hardware refresh cycles through Parallels RAS virtual applications and desktops. This helps to ensure that corporate companies have the necessary infrastructure, management, and support to effectively operate their networks.
Step 13: Invest in Supply Chain Planning and Scheduling: Investing in supply chain planning and scheduling is important because it can help to reduce risk, and waste, and optimize resources. It also helps companies ensure that their products reach customers on time while minimizing costs. Furthermore, supply chain planning and scheduling can help reduce the chance of product recalls or defects, saving both money and time for consumers. Finally, it assists in finding the best network configuration to meet demands using various feedstocks throughout the year.
Step 14: Invest in the Prevention of Large-Impact Attacks: Investing in the prevention of large-impact attacks is essential for companies to maintain secure network infrastructure and protect their systems from malicious actors. It is important for system designers to understand how adversaries may attack so that steps can be taken to prevent potential threats and mitigate the damage caused by such attacks. Companies need to establish effective monitoring and logging systems in order to detect any suspicious activity as soon as possible. By investing in the prevention of large-impact attacks, companies can ensure their networks are protected against sophisticated cyber threats and minimize the risk of being breached.
What are the best practices in managing and supporting a network infrastructure?
- Centralizing traffic: Centralizing traffic is one of the best practices in managing and supporting a network infrastructure because it reduces the amount of data that needs to be stored and processed, eliminates duplicate data, and simplifies sending the right data to the right tool.
- Dealing with duplicate data: It is important to deal with duplicate data when managing a network infrastructure because it can slow down security solutions and make them less effective. Additionally, duplicate data can cause issues with the centrally managed traffic, as well as sending the right data to the right tools for better management of the network infrastructure.
- Sending the right data to the right tool: It is important to send the right data to the right tool when managing and supporting network infrastructure in order to maximize efficiency and minimize costs. Centralizing traffic, dealing with duplicate data, and sending the right data to the right tool are all challenges that must be addressed in order to successfully run a network infrastructure model. Sending data from different sources to the same tool can result in ineffective use of resources, time, and money. By sending only relevant and necessary information directly into its designated resource or application, organizations can ensure that their networks remain operational while also avoiding wasted effort or other costly mistakes.
- Implementing secure authentication protocols: It is important to implement secure authentication protocols in network infrastructure in order to ensure the authenticity of users and protect against potential vulnerabilities and attacks. Such protocols can help control user access, manage privileges, and prevent unauthorized access to the network. Additionally, strong authentication measures such as firewalls and VPNs can help protect against malicious actors who may be trying to gain entry into the network. Behavioral analytics can also be used to identify unusual activity that could suggest a threat from an outside source.
- Monitoring network traffic: Monitoring network traffic is important in managing and supporting a network infrastructure as it allows for the detection of malicious activity and policy violations, as well as the prevention of vulnerability exploits. By keeping an eye on the traffic going through the network, security personnel can ensure that any suspicious activities are identified promptly and addressed appropriately. This helps protect businesses from data breaches or other threats to their networks.
- Ensuring network reliability and availability: Ensuring network reliability and availability is important for businesses of all sizes because it can help to ensure business continuity and provide data protection. The amount of data traveling across corporate networks has increased due to the rise in remote work, making it essential for companies to maintain a reliable network. Furthermore, the strain on networks has been heightened during the coronavirus pandemic, demonstrating that investments in network reliability and availability pay off in the long run.
- Using a secure server operating system: The importance of using a secure server operating system cannot be overstated. It provides robust protection for resources and reduces the costs associated with otherwise preventable data breaches and malfunctioning communications. Additionally, compartmentalizing files prevents unauthorized access to sensitive company data while also providing regular backups to local servers which ensures that data is not lost in the event of a breach or other security incident.
- Enforcing strict access control: It is important to enforce strict access control in network infrastructure in order to limit lateral communications and protect network devices from being compromised. Access control prevents unauthorized users and devices from accessing the network, which can help protect internal infrastructure against attacks. It also helps ensure that administrative privileges are secured and access to infrastructure devices is secure, protecting data and assets. Out-of-band management strengthens security by separating user traffic from management traffic as well, making sure integrity checks on devices and software is regularly performed so that they remain safe from attack.
- Implementing patch management: Patch management is important for network infrastructure in order to ensure the authenticity of users and to keep systems secure. Through patch management, organizations can effectively reduce their risk of security vulnerabilities as software and hardware bugs can be identified and rectified with timely updates. Additionally, patch management also helps protect data integrity by ensuring that only authorized personnel have access to sensitive information.
- Applying security best practices: It is important to apply security best practices when managing and supporting network infrastructure in order to protect users and the IT infrastructure from potential attacks. By implementing Access Control measures, Application Security measures, Firewalls, Wireless security measures, Behavioral analytics tools, Segmentation/Segregation of networks into micro-segments, and Hardening devices, organizations can limit lateral communication and attack opportunities. Additionally separating user traffic from management traffic as well as performing integrity checks on devices/software will ensure a more secure network environment for the organization.
- Regularly backing up data: It is important to regularly back up data in order to maintain the reliability of network infrastructure and prevent downtime. In the current era of remote work, having a reliable backup infrastructure in place is essential for corporate companies. Backups can help mitigate or even prevent disasters, as they keep a copy of all important data secure should something go wrong with the primary source.
- Installing anti-malware software: It is important to install anti-malware software on a network infrastructure in order to protect it from malicious software and viruses. The SARA team has demonstrated this by installing the necessary software and helping the company pass DSS licensing inspections. Having an effective anti-malware system in place is essential for ensuring a secure, reliable, and flexible network infrastructure that can be managed easily.
- Using secure encryption protocols: Using secure encryption protocols is important in managing and supporting a network infrastructure as they help to protect the network from a variety of threats, including unauthorized access. Encryption protocols can help protect data that is sent over the network, even if it is intercepted by malicious actors. Additionally, encryption protocols are increasingly necessary due to the increasing vectors for infiltration and an ever-evolving landscape of cyber threats.
- Adopting the principle of least privilege: The principle of least privilege is an important security principle that states that a user or process should have the minimum amount of access required to do their job. This helps to protect sensitive areas of the network, and also allows administrators to more easily monitor activity on the network. By employing this principle when managing network infrastructure, companies can ensure greater system security and stability.
- Utilizing cloud technologies: Organizations should consider utilizing cloud technologies in their network infrastructure to maximize the potential of their system. This can include using cloud-based observability tools to gain visibility into data centers, deploying security solutions to protect data and applications, employing traffic intelligence software to better understand customer usage patterns and identify issues early on, and accelerating cloud migration by building a multi-cloud observability toolset. Additionally, organizations should ensure cloud security and compliance by implementing zero trust architectures, reduce cost and complexity through making network changes without disruption, optimize the budget for tools usage, and improve SOC (Security Operations Center) and IR (Incident Response) effectiveness through proactive hunting for adversaries or attackers as well as building a resilient enterprise culture; finally, extend visibility with platforms that allow users to achieve the same results as customers who have already utilized their technology.
How can you implement security policies in your company’s network infrastructure?
Step 1: Set up a secure architecture: It is important to have a secure network infrastructure because the security of corporate companies' networks is essential in order to protect sensitive data, prevent unauthorized access, and ensure reliable communication between connected devices. Without proper security measures in place, wireless networks are vulnerable to attacks such as denial-of-service (DoS) attacks and eavesdropping. WLAN architectures are designed with fault tolerance and power savings in mind, which means that when properly configured, the architecture can remain secure despite faults or failures due to its redundancy capabilities. Additionally, proper configuration of the network infrastructure coupled with reliable management and support can ensure that corporate companies' IT systems operate securely at all times.
Step 2: Centralize traffic to ensure adequate monitoring: Centralizing traffic in a company's network infrastructure can have several benefits. By doing so, companies can reduce the number of duplicate data sets and improve data accuracy. Additionally, centralizing traffic in a network can help improve performance and security by making it easier to monitor it. Finally, consolidating the traffic helps ensure compliance with industry regulations or standards.
Step 3: Monitor server performance: Monitor server performance by collecting log data from servers, distributing load, analyzing log data, and automating the collection of log data. This helps in identifying and fixing networking issues quickly.
Step 4: Utilize the latest Linux server distros: Using a Linux server distro is important for security purposes because it provides a secure platform for data management and storage. Additionally, given its open-source nature, Linux distros offer users more control over the system's security settings and can be configured to provide multiple layers of protection. Furthermore, a Linux server distro is also highly resistant to malicious attacks due to its advanced security features such as path-based routing, full stack firewalls, and encryption algorithms that make it difficult for attackers to gain access. As such, utilizing the potential of Linux servers can greatly improve the overall security posture of any corporate network infrastructure.
Step 5: Install the latest version of web browsers: Installing the latest version of web browsers is important for implementing security policies in a company’s network infrastructure because it can help ensure that the latest security patches and updates are applied, which can help protect against malicious actors. Additionally, updated versions of browsers are equipped with more sophisticated security features than older versions, which can provide an additional layer of protection.
Step 6: Utilize the latest mail servers: Using the latest mail server is important for implementing security policies in a company's network infrastructure to configure services on an alternate host, reduce lookup latency and network traffic with the installation of a local caching DNS server, control access to files, monitor traffic, and track user activity.
Step 7: Set up a hosting control panel: It is important for corporate companies to have a hosting control panel in order to manage Azure virtual networks and data center firewall, as well as control the traffic that goes through their data centers by implementing custom routes. This ensures that all of their resources are properly managed and secure. Having a hosting control panel also helps with troubleshooting any issues related to their network infrastructure quickly and efficiently, reducing downtime or other potential issues.
Step 8: Research and select the best hosting services: When selecting hosting services for a company's network infrastructure, it is important to consider the types of data that will need to be processed. Cybersecurity providers often charge based on the amount of data they process, so sending data from different sources to the same tool can lead to inefficiency and increased cost. Companies should look for hosting services that are tailored specifically for their network infrastructure in order to maximize efficiency and minimize costs.
Step 9: Implement a data centralization strategy: Data centralization is the process of collecting and storing data in one centralized location. It can be used to make it easier for security teams to identify, track, and respond to potential attacks by having all data stored in a single place. Data centralization also helps reduce the risk of malicious activity by eliminating duplicate data, which can be difficult to track across different systems. Automating processes by sending the right data to the right tool also improves security team efficiency when dealing with threats.
Step 10: Utilize supply chain planning and scheduling: The significance of supply chain planning and scheduling in relation to implementing security policies in a company's network infrastructure is that it helps to ensure that the right items are ordered in the right quantities and that they arrive on time. Additionally, scheduling helps to ensure that the items ordered are delivered at the right time, in the right place, and by the correct person. This makes it easier for companies to keep purchase data at the granular level so they can better track inventory, make better decisions about marketing and product launches, as well as reduce their risk of coupon fraud. Consequently, proper supply chain planning and scheduling are key for optimizing a company's network infrastructure so they may extract maximum value from data.
Step 11: Install and update the latest Linux distros: The installation and updating of the latest Linux distros provide many benefits to security policies in a company's network infrastructure. This includes increased security through improved patching, which can help mitigate possible cybersecurity risks, as well as improved performance and stability over time due to being able to utilize the most up-to-date technology available. Additionally, using the latest Linux distros is often more cost-effective than older versions. As such, it is beneficial for companies investing in their network infrastructure to install and update their systems with the latest Linux distributions.
Step 12: Attend international symposiums to stay up to date: Attending international symposiums is important for companies to stay up-to-date on the latest cloud, security, and observability tools as well as build relationships that could lead to future collaborations or partnerships. Additionally, attending symposiums can help companies learn from other companies and improve their products. By being informed of the latest technology available and networking with others in the industry, companies can benefit significantly from attending these events.
Step 13: Monitor for duplicate data: Monitoring for duplicate data can help to secure a company's network infrastructure by reducing the amount of unnecessary data sent to security tools and improving the efficiency of those tools. By removing duplicate data, Gigamon enables intelligent traffic filtering so that only the important traffic is sent to security solutions, allowing them to better identify potential threats and respond more quickly. This helps maximize protection against cyberattacks while minimizing disruptions or downtime due to excessive amounts of unnecessary or useless traffic.
Step 14: Implement prevention measures for large-impact attacks: Implementing prevention measures for large-impact attacks is critical for organizations to maintain the security, authenticity, and integrity of their IT infrastructure. Without the proper protection in place, organizations are at risk of suffering a serious attack that could have costly repercussions. Prevention measures such as segmenting networks and functions, properly laying out networks, limiting lateral communications, and securing access to infrastructure devices can help protect against large-impact attacks. Additionally, implementing integrity checks on devices and software can help identify potential threats before they become a reality.
What are the benefits of network infrastructure?
The benefits of network infrastructure are numerous. Network infrastructure provides a foundation for increased efficiency and improved communication, allowing businesses to complete tasks more quickly and improve communication among employees. It is also scalable, and able to handle growth without redesigning the entire network. Proper monitoring and management of the network allow businesses to save money on licensing costs since they can purchase site licenses instead of individual machines. Additionally, security is improved due to files being securely shared across the network and data backups being easily done through local servers. Finally, user files and data can be securely protected from each other with the use of network infrastructure.
How can I manage network infrastructure?
Companies can manage their network infrastructure by hiring trained and experienced IT staff, using key management tools to manage encryption keys, setting up firewalls to control traffic and keep the network safe, implementing intrusion prevention systems and intrusion protection systems to prevent unauthorized parties or devices from joining the network, using optical fiber cables to provide Internet access for all devices in a large network, connecting computers to LANs with switches, connecting different types of networks with gateways and providing servers for other computers. Additionally, managing enterprise-level infrastructure requires a full-time job for one person alone.
What are the challenges of network infrastructure?
Network infrastructure can present various challenges for corporate companies. Centralizing traffic can be difficult due to potential data loss or corruption, and sending the right data to the right tool can be complicated as different tools address different types of data in distinct ways. Additionally, duplicate data may cause problems when attempting to identify which information is necessary. Proper management and support are important aspects of successful network infrastructure in order to avoid these issues.
What is the future of network infrastructure?
It is expected that network infrastructure will continue to move towards greater levels of virtualization and software-defined solutions in the future. This will help organizations become more efficient and reduce the amount of time needed to access business data. Additionally, it is likely that growth-driven strategies for network infrastructure deployment will be increasingly favored by organizations seeking optimal outcomes. The increasing popularity of wireless devices over cable connections is also anticipated to remain strong, while the need for a hybrid networking infrastructure has grown as more organizations embrace remote working models. Wireless access to essential applications and internet connectivity remains an important aspect of any successful network infrastructure in order to support a hybrid workplace.
How do I troubleshoot network infrastructure?
Network infrastructure issues can arise from a variety of sources, such as hardware and software malfunctions, human error, and security breaches. Common issues include slow internet speeds, unresponsive servers or applications, and connection drops. To resolve these problems quickly and efficiently, companies should have a good network management system in place with automated processes. Additionally, utilizing the right technology can help streamline operations and identify any potential problems before they become serious issues. Finally having experienced IT personnel on hand that is able to troubleshoot any issue that may arise is essential for an efficient network infrastructure environment.
What are the best practices for network infrastructure?
Organizations should adhere to certain best practices in order to ensure the security and integrity of their network infrastructure. Proper segmentation and segregation are necessary for protecting networks from attacks, as well as hardware such as routers for physical separation. Lateral communications between computers on a network should be limited and devices hardened in order to increase security. Administrators should be given limited access to important infrastructure devices, while authentication measures such as multi-factor authentication and privileged access management can help ensure user authenticity. Lastly, regular integrity checks on devices and software can help protect against malware infiltration. Following these best practices will enable organizations to maintain a secure network infrastructure foundation upon which they can build successfully.
How do I choose the right network infrastructure for my business?
Choosing the right network infrastructure for a business is an important step in ensuring that the business runs efficiently and securely. It is essential to assess the needs of the business and select an infrastructure platform that can support those needs. Companies should consider both short-term and long-term objectives when selecting an infrastructure platform, and consult with IT professionals if necessary. Additionally, companies should look at products like Restorepoint Universal Console to improve security and performance, as well as choose platforms like VMware or Microsoft for their specific requirements. Ultimately, making a carefully considered decision about which network infrastructure will best suit the needs of your company is critical for achieving success in today's digital world.
See Also
Network Architecture
IT Architecture
IT Infrastructure