Data Security
Definition of Data Security
Data Security refers to the protection of data from unauthorized access, use, theft, or destruction. Data security is a critical aspect of modern computing and is essential for protecting sensitive information and maintaining privacy.
Data security encompasses a range of measures and strategies, including access control, encryption, backup and recovery, and network security. Access control involves controlling who can access data and what they can do. This includes user authentication, password policies, and role-based access control.
Encryption involves the use of mathematical algorithms to scramble data so that it can only be read by authorized users with the appropriate decryption key. Encryption can be applied to data at rest, such as on a hard drive or in a database, as well as data in motion, such as when transmitted over a network.
Backup and recovery involve creating copies of data and storing them in secure locations so that data can be restored in the event of data loss or system failure. Network security involves securing the network infrastructure, such as firewalls, intrusion detection and prevention systems, and virtual private networks, to prevent unauthorized access or attacks.
Data security is important for a variety of reasons. It helps to protect sensitive information, such as personal and financial data, from theft and misuse. It also helps to ensure compliance with regulations and standards, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS).
There are several threats to data security, including cyberattacks, data breaches, and human error. Cyberattacks can involve the use of malware, phishing scams, or other techniques to gain unauthorized access to data. Data breaches can occur when data is stolen or lost, either through intentional or accidental means. Human error can involve mistakes such as accidentally deleting data or falling victim to social engineering scams.
Data Security Vs. Data Privacy[1]
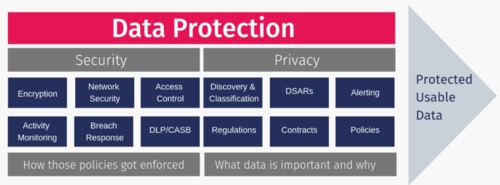
Data security and data privacy are, by no means, the same terms. Data privacy is about the proper usage, collection, retention, deletion, and storage of data. Data security is policies, methods, and means to secure personal data.
So, if you are using a Google Gmail account, your password would be a method of data security, while the way Google uses your data to administer your account would be data privacy.
Think, for example, of a window on a building; without it being in place, an intruder can sneak in and violate both the privacy and security of the occupants. Once the window is mounted it will perform a pretty decent job of keeping unwanted parties from getting into the building. It will, however, not prevent them from peeking in, interfering thus with the occupants’ privacy. At least not without a curtain. In this (oversimplified) example, the window is a security control, while the curtain is a privacy control.
The former can exist without the latter, but not vice versa. Data security is a prerequisite to data privacy. And information security is the main prerequisite to data privacy.
The Need for Data Security[2]
Organizations around the globe are investing heavily in information technology (IT) cyber defense capabilities to protect their critical assets. Whether an enterprise needs to protect a brand, intellectual capital, and customer information or provide controls for critical infrastructure, the means for incident detection and response to protect organizational interests have three common elements: people, processes, and technology.
Ensuring Data Security[3]
While data security isn’t a panacea, you can take several steps to ensure data security. Here are a few that we recommend.
- Quarantine Sensitive Files: A rookie data management error is placing a sensitive file on a share open to the entire company. Quickly get control of your data with data security software that continually classifies sensitive data and moves data to a secure location.
- Track User Behavior against Data Groups: The general term plaguing rights management within an organization is “overpermissioning’. That temporary project or rights granted on the network rapidly becomes a convoluted web of interdependencies that result in users collectively having access to far more data on the network than they need for their role. Limit a user’s damage with data security software that profiles user behavior and automatically puts in place permissions to match that behavior.
- Respect Data Privacy: Data Privacy is a distinct aspect of cybersecurity dealing with the rights of individuals and the proper handling of data under your control.
Types of Data Security Controls[4]
Understanding the importance of data security will help you formulate a plan to protect that data. There are many data security technologies and processes that can support your company’s productivity while safeguarding data. Types of data security controls include:
- Authentication: Authentication, along with authorization, is one of the recommended ways to boost data security and protect against data breaches. Authentication technology verifies if a user’s credentials match those stored in your database. Today’s standard authentication processes include using a combination of ways to identify an authorized user, such as passwords, PINS, security tokens, a swipe card, or biometrics. Authentication is made easier through single sign-on technology, which, with one security token, allows an authenticated user access to multiple systems, platforms, and applications. Authorization technology determines what authenticated users can do or see on your website or server.
- Access Control: Authentication and authorization happen through the process called access control. Access control systems can include **Discretionary access control (the least restrictive), which allows access to resources based on the identity of users or groups,
- Role-based access control, which assigns access based on organizational role and allows users access only to specific information, and
- Mandatory access control, which allows a system administrator to strictly control access to all information.
- Backups & Recovery: Prioritizing data security also requires a plan for accessing your company’s and client’s data in case of system failure, disaster, data corruption, or breach. Doing regular data backups is an important activity to help with that access. A data backup entails making a copy of your data and storing it on a separate system or medium such as a tape, disk, or in the cloud. You can then recover lost data by using your backup.
- Encryption: Data encryption software effectively enhances data security by using an algorithm (called a cipher) and an encryption key to turn normal text into encrypted ciphertext. To an unauthorized person, the cipher data will be unreadable. That data can then be decrypted only by a user with an authorized key. Encryption is used to protect the data that you store (called data at rest) and data exchanged between databases, mobile devices, and the cloud (called data in transit). Your encryption keys must be securely managed, including protecting your critical management systems, managing a secure, off-site encryption backup, and restricting access.
- Data Masking: Data masking software hides data by obscuring letters and numbers with proxy characters. The data is still there, behind the masking. The software changes the data back to its original form only when an authorized user receives that data.
- Tokenization: Tokenization substitutes sensitive data with random characters that are not algorithmically reversible. The relationship between the data and its token values is stored in a protected database lookup table rather than being generated by and decrypted by a mathematical algorithm (as in the case of encryption). The token representing the real data is used across different systems as a replacement, while the actual data is stored on a separate, secure platform.
- Deletions & Erasure: When electronic data is no longer needed and must be permanently cleared from the system, erasure can overwrite that data so that it is irretrievable. Erasure is different from deletion, which is a process that simply hides data in such a way that makes it easy to retrieve.
Data Security Compliance and Standards[5]
When an organization collects any kind of personal data, it instantly becomes known as a data processor. This label comes with a lot of responsibility. For this reason, there are a number of compliance regulations that govern organizations dealing with personal data regardless of the type or volume. The regulations that affect your organization will depend on a selection of factors, such as the industry you are operating in and the type of data you store. For example, if you store data relating to citizens in the European Union (EU) you will need to comply with the latest GDPR regulations. Failure to comply with any regulations that affect your organization could result in hefty fines. Other examples of regulatory compliance and standards examples include:
- NERC - Critical Infrastructure Protection
- China's Personal Information Security Specification
- PCI Security Standards
Regulatory compliance requirements often vary by data type. A few common examples include:
- Personally Identifiable Information (PII)
- Protected Healthcare Information (PHI, HIPAA)
- Credit card information
Benefits of Data Security and The Potential Risks of Poor Data Security[6]
Benefits of Data Security
Loss or unauthorized disclosure of valuable data can be quite costly to an organization. It's the reason data security is quite useful. For instance;
- Safeguards all valuable information: Sensitive information is never supposed to leak. Whether we are talking about bank customers’ details or a hospital’s patients’ information, this is crucial information that is not meant for every prying eye. Data security keeps all this information exactly where it's meant to be.
- Important for your reputation: Any organization that can keep secrets also helps to build confidence among all stakeholders, including customers, who know that their data is both safe and secure.
- Marketing and competitive edge: Keeping sensitive information from illegal access and disclosure keeps you ahead of your competitors. Preventing any access to your future development or expansion plans is key in maintaining your competitive advantage.
- Saves on development and support costs: The earlier you plug security features into your application, the fewer costs you may incur from any future support and development costs regarding code modifications.
Potential Risks of Poor Data Security
The more technologically advanced businesses become, the more susceptible their systems become to attacks. Poor data security can subject your company to the following dangers:
- Costly fines and litigations: Data breaches are usually serious offenses that can lead to legal actions from the customer against an organization. Failure to comply with any applicable state or federal data protection regulations can result in fines exceeding hundreds of thousands of dollars, depending on the severity of the breach, the number of individuals affected, and the company’s attempts (or lack thereof) to notify consumers and mitigate risks.
- Reputation damage: Privacy and security of data are important, especially to your customers. If you don’t meet your end of this bargain – keeping your customers’ data secure in exchange for their business – your reputation as an organization can go up in flames. Customers tend to lose faith and confidence in a company that cannot keep their private information well-protected. Loss of business and a damaged reputation can often be even more costly over time than the hefty regulatory fines you also might be facing.
- Loss of business: Cyber attackers have the potential to not only access and exploit sensitive information; they can also delete the same information. They can even introduce a highly destructive virus that infects the whole system, such as ransomware, requiring the payment of a ransom fee in order to regain access to your networks and sensitive data.
- Poor data security could lead to an event that negatively impacts your business. Even the ability to conduct normal business may be changed. Again, it is a trickle-down effect, in which you may not be able to render the required services, leading to legal action and probable loss of revenue.
Data Security Challenges[7]
- Explosive data growth: Data is growing at an exponential rate. Keeping up with new data sources across multiple environments creates new complexity at an unprecedented scale.
- New privacy regulations: The General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), Brazil’s Lei Geral de Proteção de Dados (LGPD), and more.
- Operational complexity: Movement to the cloud, big data technologies, and disparate tools from multiple vendors intensify complexity.
- Cybersecurity skills shortage: Organizations are already dealing with a lack of skilled security professionals, and this gap is only expected to widen over the next several years.
Data Security Best Practices[8]
There are many parts to a comprehensive data security solution. Below is an overview of what should come together to create a good foundation for data security. What a best practice looks like for your business will depend on many factors, such as size, industry, location, and existing tools and policies.
- Securing information
- Manage your identity by restricting access to sensitive documents. Sometimes called data classification, managing who can see what based on their User ID is a great way to keep sensitive information restricted to only those who need to see it. This limits the amount of damage that can be done if someone's username or log in details are stolen. Companies should be set up to handle different permissions based on the user, and this is a key point in a good data security policy.
- Encryption is one of the best tools that we have to keep data safe, but it isn't a monolith. You can't just decide to encrypt all your data and call it a day — that's not exactly how it works. Often, software tools that you use for your business will have some sort of encryption offered, and that's a great place to start. Your information-backup service, for example, should be able to encrypt that data for you. You should also ensure you encrypt transmissions to add another layer of security to any information you send. Think of encryption as taking your plain data and turning it into a secret code that only you can make sense of — not the bad guys.
- Be prepared for the mobile workforce. As mobile devices take over the workplace, your security threats grow. You need a mobile security plan to keep everyone in line. This should include an enforced protocol for employees, like staying off public Wi-Fi on work devices and having a company-mandated antivirus on mobile devices.
- Protect user data at the source. When customers and employees log in for the first time (or repeatedly), you can verify and secure their information with secure authentication practices like social login. This not only simplifies the process and reduces the risk of churn, but it also helps organize all of this sensitive data in a single location instead of in multiple databases and spreadsheets that can easily be lost.
- Preparing for Threats
- Test how good your system is. The best defense is a good offense, and the best offense in secure data recovery is working to ensure you don't lose your data in the first place. Either create an internal team to stress-test your system or find someone outside your company to do it, but don't leave your security to chance.
- Educate your employees. Common data-security attacks like spear-phishing emails and USB traps target employees who are unaware of the risks and have let their guard down. Circulating everyday tips on Security or implementing an executive training program can go a long way toward mitigating these risks.
- Have an incident-management plan. When you find out that your company's security has been compromised, the last thing you want to do is panic. Having a comprehensive protocol can limit the damage done. Yes, IT needs to be aware of what to do, but you should also create guidelines for management, letting employees know, and the next steps for recovery.
- Make a secure data recovery plan in case of corruption or an unhappy scenario where something you need has been deleted or compromised. For many teams, this means having a backup copy of data that is regularly updated. The backup itself will have to be protected and should also be separate from the rest of your data.
- Deleting information
- Know how and when to let go. When it's time to get rid of information, you must know how to dispose of it properly. When you have to throw out sensitive information on paper, you shred it. You cut up your credit cards and write "VOID" on checks before disposing of them. Digital data is no different. Make sure that when you're wiping information, it's really gone and not lingering somewhere that will come back to bite you.
- Don't forget physical copies. If any of your backups are on paper, are stored on a thumb drive, are X-rays or microfilm or negatives — or anything else that's physical and totally separate from your digital systems — don't forget about them. When you're deleting digital information, make sure that part of the process is double-checking to see whether that information has a physical counterpart and, if so, destroying it in kind.
- Compliance risks (check)
- Some rules and regulations govern what you should and cannot do with your business's data, and they can help lower your risks. Especially if you are dealing with sensitive information, looking toward these laws and guidelines will help give you a better sense of what is appropriate for your company. For example, companies in the medical field are likely required to follow HIPAA requirements.
- You can also reduce compliance risks by following open standards. Take identity management, which has guidelines that are available for everyone to follow, with the explicit purpose of being as safe and responsible as possible.
- Of course, everyone is talking about the GDPR and related laws like the California Consumer Privacy Act(CCPA). These points for data privacy and sharing will help broaden and deepen your existing protocol.
- To ensure that you are exposed to the least risk possible, be thorough in your investigation of the laws that apply to your company and the best practices that have developed in your field or for your concerns. This will depend heavily on industry and location, but it needs to be done correctly to ensure that your data security is as good as possible.
See Also
- Cyber Security
- Encryption: Encryption converts plain text or data into a coded form (ciphertext) to prevent unauthorized access or interception. It ensures data confidentiality by making it unreadable to anyone without the decryption key.
- Authentication: Authentication is verifying the identity of users or entities attempting to access a system or data. It ensures that only authorized users are granted access to sensitive information or resources.
- Access Control: Access control refers to the mechanisms and policies that regulate and restrict access to data, systems, or resources based on user identity, roles, permissions, or other criteria. It helps prevent unauthorized access and data breaches.
- Firewalls: Firewalls are network security devices or software applications that monitor and control incoming and outgoing network traffic based on predefined security rules. They act as a barrier between a trusted internal network and untrusted external networks, such as the Internet, to protect against unauthorized access and cyber threats.
- Intrusion Detection System (IDS): An Intrusion Detection System is a security tool or software application that monitors network or system activities for signs of suspicious or malicious behavior. It detects and alerts administrators to potential security incidents or intrusions, helping to mitigate security threats and vulnerabilities.
- Vulnerability Assessment: Vulnerability assessment is the process of identifying, evaluating, and prioritizing security vulnerabilities and weaknesses in systems, applications, or networks. It helps organizations proactively address security risks and protect against potential exploitation by attackers.
- Data Loss Prevention (DLP): Data Loss Prevention is a set of tools, processes, and policies designed to prevent unauthorized disclosure or leakage of sensitive data. It involves monitoring, detecting, and mitigating risks associated with the unauthorized access, transmission, or storage of sensitive information.
- Secure Sockets Layer (SSL)/Transport Layer Security (SSL/TLS): SSL/TLS are cryptographic protocols used to secure communication and data transmission over the internet. They provide encryption, authentication, and data integrity to protect sensitive information exchanged between clients and servers.
- Security Incident Response: Security incident response is detecting, analyzing, and responding to security incidents, breaches, or cyberattacks. It involves developing incident response plans, coordinating response efforts, containing and mitigating the impact of incidents, and conducting post-incident analysis to improve security defenses.
References
- ↑ Data Security Vs. Data Privacy
- ↑ Why Data Security?
- ↑ How Do You Ensure Data Security?
- ↑ Types of Data Security Controls
- ↑ Data Security Compliance and Standards
- ↑ What are the Benefits of Data Security and the Potential Risks of Poor Data Security
- ↑ What are the top data security challenges?
- ↑ What Are Best Practices for Data Security?