OCTAVE (Operationally Critical Threat, Asset and Vulnerability Evaluation)
The Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) is a framework for identifying and managing information security risks. It defines a comprehensive evaluation method that allows an organization to identify the information assets that are important to the mission of the organization, the threats to those assets, and the vulnerabilities that may expose those assets to the threats. By putting together the information assets, threats, and vulnerabilities, the organization can begin to understand what information is at risk. With this understanding, the organization can design and implement a protection strategy to reduce the overall risk exposure of its information assets.[1]
OCTAVE was developed in 2001 at Carnegie Mellon University (CMU), for the United States Department of Defense. The framework has gone through several evolutionary phases since that time, but the basic principles and goals have remained the same. Two versions exist: OCTAVE-S, a simplified methodology for smaller organizations that have flat hierarchical structures, and OCTAVE Allegro, a more comprehensive version for large organizations or those with multilevel structures.[2]
How it Works[3]
OCTAVE is a flexible and self-directed risk assessment methodology. A small team of people from the operational (or business) units and the IT department work together to address the security needs of the organization. The team draws on the knowledge of many employees to define the current state of security, identify risks to critical assets, and set a security strategy. It can be tailored for most organizations.
Unlike most other risk assessment methods the OCTAVE approach is driven by operational risk and security practices and not technology. It is designed to allow an organization to:
- Direct and manage information security risk assessments for themselves
- Make the best decisions based on their unique risks
- Focus on protecting key information assets
- Effectively communicate key security information
OCTAVE Phases[4]
OCTAVE is organized around these three basic aspects enabling organizational personnel to assemble a comprehensive picture of the organization’s information security needs. The phases are:
- Phase 1: Build Asset-Based Threat Profiles – This is an organizational evaluation. The analysis team determines what is important to the organization (information-related assets) and what is currently being done to protect those assets. The team then selects those assets that are most important to the organization (critical assets) and describes security requirements for each critical asset. Finally, it identifies threats to each critical asset, creating a threat profile for that asset.
- Phase 2: Identify Infrastructure Vulnerabilities – This is an evaluation of the information infrastructure. The analysis team examines network access paths, identifying classes of information technology components related to each critical asset. The team then determines the extent to which each class of component is resistant to network attacks.
- Phase 3: Develop Security Strategy and Plans – During this part of the evaluation, the analysis team identifies risks to the organization’s critical assets and decides what to do about them. The team creates a protection strategy for the organization and mitigation plans to address the risks to the critical assets, based upon an analysis of the information gathered.
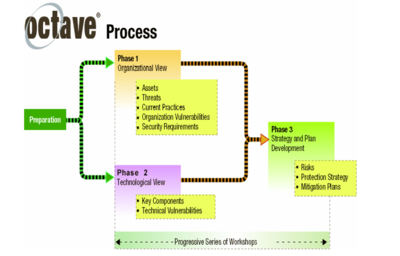
source: Indiana University of Pennsylvania
OCTAVE Methodologies[5]
There are now three distinctive OCTAVE methodologies available for public use: the OCTAVE method, OCTAVE-S, and OCTAVE Allegro. The
introduction of OCTAVE Allegro is not intended to supplant previous OCTAVE methodologies. OCTAVE Allegro is a variant that provides a streamlined process focused on information assets. However, each OCTAVE method has broad applicability, and users of these methods can select the approach that best fits their particular information security risk assessment needs.
- The OCTAVE method was the first OCTAVE-consistent methodology to be introduced [Alberts 2001]. The approach is defined by a method implementation guide (procedures, guidance, worksheets, information catalogs) and training. The method is performed in a series of workshops conducted and facilitated by an interdisciplinary analysis team drawn from business units throughout the organization (e.g. senior management, operational area managers, and staff) and members of the IT department [Alberts 2002]. The intended audience for the OCTAVE method is large organizations with 300 or more employees. More specifically, it was designed for organizations that
- have a multi-layered hierarchy
- maintain their own computing infrastructure
- have the ability to run vulnerability evaluation tools
- have the ability to interpret the results of vulnerability evaluations
- As described above, the OCTAVE method is performed in three phases.
- OCTAVE-S: The development of OCTAVE-S was supported by the Technology Insertion, Demonstration, and Evaluation (TIDE) program at the SEI,4 with the goal of bringing an OCTAVE-based approach to small manufacturing organizations. The most current version of the OCTAVE-S approach, version 1.0, is specifically designed for organizations of about 100 people or less. Consistent with the OCTAVE criteria, the OCTAVE-S approach consists of three similar phases. However, OCTAVE-S is performed by an analysis team that has extensive knowledge of the organization. Thus, OCTAVE-S does not rely on formal knowledge elicitation workshops to gather information because it is assumed that the analysis team (typically consisting of three to five people) has working knowledge of the important information-related assets, security requirements, threats, and security practices of the organization. Another significant difference in OCTAVE-S is that it is more structured than the OCTAVE method. Security concepts are embedded in the OCTAVE-S worksheets and guidance, allowing less experienced risk and security practitioners to address a broad range of risks with which they may not have familiarity. A final distinguishing feature of OCTAVE-S is that it requires a less extensive examination of an organization’s information infrastructure. Because small organizations may not have the resources to obtain and execute vulnerability tools, OCTAVE-S was designed to include a limited examination of infrastructure risks so as to remove a potential barrier to adoption.
- OCTAVE Allegro: The OCTAVE Allegro approach is designed to allow broad assessment of an organization’s operational risk environment with the goal of producingm ore robust results without the need for extensive risk assessment knowledge. This approach differs from previous OCTAVE approaches by focusing primarily on information assets in the context of how they are used, where they are stored, transported, and processed, and how they are exposed to threats, vulnerabilities, and disruptions as a result. Like previous methods, OCTAVE Allegro can be performed in a workshop-style, collaborative setting and is supported with guidance, worksheets, and questionnaires, which are included in the appendices of this document. However, OCTAVE Allegro is also well suited for use by individuals who want to perform risk assessment without extensive organizational involvement, expertise, or input. The OCTAVE Allegro approach consists of eight steps that are organized into four phases. In phase 1, the organization develops risk measurement criteria consistent with organizational drivers. During the second phase, information assets that are determined to be critical are profiled. This profiling process establishes clear boundaries for the asset, identifies its security requirements, and identifies all of the locations where the asset is stored, transported, or processed. In phase 3, threats to the information asset are identified in the context of the locations where the asset is stored, transported, or processed. In the final phase, risks to information assets are identified and analyzed and the development of mitigation approaches is commenced.
See Also
- IT Governance
- ITIL
- Val IT
- Risk IT
- Factor Analysis of Information Risk (FAIR)
- COBIT (Control Objectives for Information and Related Technology)
- Business Model for Information Security (BMIS)
- COSO
- CMMI
- IT Assurance Framework (ITAF)
- IT Governance Framework
- ICT Investment Framework
- The Open Group Architecture Framework (TOGAF)
References
- ↑ Definition - What is OCTAVE (Operationally Critical Threat, Asset and Vulnerability Evaluation) CMU.edu
- ↑ History and Evolution of the OCTAVE Framework Techtarget
- ↑ How Does the OCTAVE Framework Work? U.edu
- ↑ The Three Phases of OCTAVE Framework Matt White
- ↑ What are the Different OCTAVE Methodologies? SEI.CMU
