Fault Configuration Accounting Performance Security (FCAPS)
Definition of Fault Configuration Accounting Performance Security (FCAPS)[1]
FCAPS is the ISO Telecommunications Management Network model and framework for network management. FCAPS is an acronym for Fault, Configuration, Accounting, Performance, Security which are the management categories into which the ISO model defines network management tasks. Where the FCAPS model was largely designed to be network centric, the newer eTOM Business Process Framework is more business centric.
Historical Background Of FCAPS[2]
The ISO, under the direction of the OSI group, has created a network management model as the primary means for understanding the major functions of network management systems. The model in question is interchangeably called either the OSI network management model or ISO network management model so the full name could be the OSI/ISO network management model.
The comprehensive management of an organization's information technology (IT) infrastructure is a fundamental requirement. Employees and customers rely on IT services where availability and performance are mandated, and problems can be quickly identified and resolved. Mean time to repair (MTTR) must be as short as possible to avoid system downtimes where a loss of revenue or lives is possible.
In the early 1980s the term FCAPS was introduced within the first Working Drafts (N1719) of ISO 10040, the Open Systems Interconnection (OSI) Systems Management Overview (SMO) standard. At that time the intention was to define five separate protocol standards, one for each functional area. Since initial experiences showed that these protocols would become very similar, the ISO working group responsible for the development of these protocols (ISO/TC97/SC16/WG4, later renamed into ISO-IEC/JTC1/SC21/WG4) decided to create a single protocol for all five areas instead. This protocol is called common management information protocol (CMIP). In the 1990s the ITU-T, as part of their work on Telecommunications Management Network (TMN), further refined the FCAPS as part of the TMN recommendation on Management Functions (M.3400). The idea of FCAPS turned out to be very useful for teaching network management functions; most textbooks therefore start with a section that explains the FCAPS.
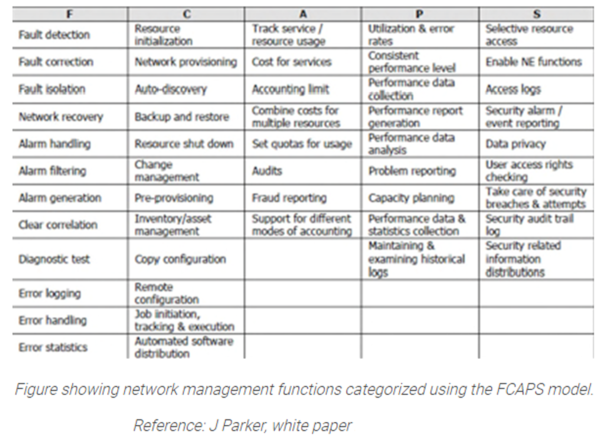
Fault Configuration Accounting Performance Security (FCAPS) Model[3]
F is for Fault
A fault is an event that shows a problem in the network. The aim of fault management is to detect, isolate, correct and log faults that occur in the network. It also includes trend analysis to predict errors so that the network always provides the service it intends to. In order to manage faults, we need a system to monitor the network and raise alarms. A basic alarm management system provides a list of alarms of alarms based on the network topology. Once the alarms are raised or network users face a problem, a ticketing system is required to manage the workload and priorities associated with the faults. An alarm only shows the symptom of a problem, a troubleshooting system is required to gather more information about potential causes that lead to the fault. This includes gathering more information about all devices involved in the path where the fault has occurred. Better fault management can be achieved by proactively keeping track of the network and predicting when a fault can occur. This can be done by injecting tests into the network to find a fault. It can also be done by analyzing historical fault data.
C is for configuration
For the network to do what it is supposed to do, it needs to be told what needs to be done in the first place. This is known as the network configuration function. The goals of network configuration management are to gather and store configurations from network devices (this can be done locally or remotely), to simplify the configuration of the device, to track changes that are made to the configuration, to provision circuits or paths through non-switched networks and to plan for future expansion and scaling. Often the network does not remain static, you may need to add or remove devices. Auto-discovery of network components and network topology building is helpful in such a case. One of the common problems that arises in a large network is managing and configuring IP addresses.
A is for Accounting / Administration
Accounting is also known as billing management. This is mostly for network service providers. The goal is to gather usage data and based on this a bill is generated. For non-billed networks, the A stands for administrative tasks such as user permission management
P is for performance management
Network performance management deals with efficiency of the network. The network performance function, addresses the throughput, percentage utilization, error rates and response times areas. Collecting and analyzing performance data helps in meeting SLAs and to do capacity planning. Like in fault management, one needs to analyze historical performance data to take care of capacity or reliability issues before they affect service requirement. One of the common problems is to monitor bandwidth to understand whether it is utilized prudently. Sometimes one needs to configure policies to give bandwidth priority to certain types of traffic such as VoIP calls. Once this is done VoIP monitoring can help ensure the calls meet the desired quality of service.
S is for Security
Security management involves managing the security of the network. One of its major goals is to manage security threats like hacker attacks, denial of service attacks, viruses and spam. In addition, security management consists of intrusion detection through monitoring traffic on the network, application of policies that limit the traffic or differentiates between different types of traffic and gives them different privileges, blacklisting ports with suspicious traffic and placing honey-pots in the network to attract attackers. Often firewall troubleshooting is required to resolve a security breach or threat.
See Also
Data Security
Security Architecture
Security Policy
Security Reference Model (SRM)
Information Security Governance
Information Security
Adaptive Security Architecture (ASA)
Business Model for Information Security (BMIS)
Common Data Security Architecture (CDSA)
Federal Information Security Management Act (FISMA)
Payment Card Industry Data Security Standard (PCI DSS)
Enterprise Information Security Architecture (EISA)
Fault Configuration Accounting Performance Security (FCAPS)
Graduated Security
Information Systems Security (INFOSEC)
Information Security Management System (ISMS)
Information Technology Security Assessment
Mobile Security
Network Security
Cyber Security