Mobile Information Management (MIM)
HP defines Mobile Information Management (MIM) is "the defined approach by which an organization efficiently plans, protects, controls, and disposes of information accessed, used, and shared on endpoint devices, and through which it ensures that the identification, classification, and leveragability of that information’s value is optimized."[1]
MIM is a device agnostic security strategy that encrypts sensitive information and allows it to be handled only by the approved applications. It deifferentiates between various sources of information and interprets policies or permissions that a data carries. For MIM vendors the primary challenge is to coordinate with the device manufacturers in order to establish an integrated medium for data transmissions. Often, MIM is banded together with MAM and MDM when it comes to matters concerning security.[2]
MIM is distinguished from other mobile security initiatives in that it focuses specifically on data rather than on the devices or applications that utilize the data. Mobile Information Management involves the encryption of sensitive data and ensuring that only authorized applications can access, transmit or store this data using strong password protection.Well-rounded mobile information management strategies and solutions also include clear communication and enforcement of the MIM policies for protecting and securely using data on mobile devices in the enterprise.[3]
Mobile information management is used to optimize the processing of relevant information. When employees have to make important decisions on the road, such as the customer, they often need to have access to information and documents that are usually located on a central server. This applies to repair instructions, the past history of a particular customer, or real mobile BI applications that coordinate and consolidate different internal information sources. Then, for example, a salesperson can calculate the optimal price for a specific customer on the road or filter out the optimal supplementary offer. Not all applications that access data are containerized and the data that these applications process can not always be stored in the application container. Then MIM is particularly important to protect the data against unauthorized access, loss or alteration. Therefore, MIM systems and function blocks are currently gaining in importance. One of the most important functions of MIM modules is the provision of an encrypted document container on the mobile device. It prevents unauthorized access to protected data, for example when the device is lost. To ensure that important documents are not lost by mail, MIM solutions have secure mobile mail services. Secure access to the file server is necessary to load documents from there to the end device. For users and administrators, it is practical and labor-saving, if the MIM functions can be integrated into the existing document management system. In this case, all documents to which the DMS system has access are, in principle, also available to mobile users. This function provides eight of the tested solutions. Good Technologies relies on document management solutions specifically designed for mobile web work. WebDAV (Web-based Distributed Authoring and Versioning),[4]
The goal for MIM is to secure sensitive data on any mobile device that connects to the Enterprise. MIM is not a defense against hacking or malware but looks at the use of sensitive corporate data on mobile devices.
Steps to a Better Mobile Information Management (MIM) Strategy[5]
- Start MIM With Passwords: Any MIM strategy has to start with encryption and password protection. If you forget about the mobile devices or the apps and concentrate on locking the information itself, that is what MIM actually does.
- Design Your Information Governance (IG): Designing your own information governance (IG) will ensure that the information that is crucial to your firm is not vulnerable to any mobile device or app. Building up information governance involves three steps:
- Stating an inventory of rules for data management
- Applying those rules effectively
- Creating records tracking the effective application of all those IG rules. IG must be a part of your enterprise architecture incorporating the rules into all departments.
- Anticipate mobility: All the IG rules must go hand in hand with the expectation of anticipating mobility in company’s data assets and device users. This may also raise the need for regular updates to the existing IG rule portfolios. The IG rules must connect more closely to the data assets rather than user behaviors. This will allow that the responsive policies and controls for mobile devices, are evaluated and designed in a better manner. The IT department must be capable of governing data not only within the company’s own systems, but also when that data is mobile and moving outside the firewalls. Anticipate the mobility of data assets so as to let the enterprise govern the information fully.
- Expand The Information Governance Rules: Governing digital assets is a big responsibility and a set number of information governance rules can’t handle it all. It requires a lot more from the MIM strategy builders. In order to build up a successful mobile information management strategy, you must expand the scope of information governance to govern mobile data assets throughout the information lifecycle. This includes getting access to how digital assets are created, saved, accessed, modified, sent, received, stored, preserved and scheduled for disposition.
- Enable The Legal Rules: It is necessary to stick to the legal rules. Your MIM strategy must support all mandatory legal requirements including the availability of specific types of records. When building up rules and processes within your MIM strategy, you must review all applicable legal rules and incorporate any functional requirements for mobile devices so as to align to those legal rules.
Build up a MIM strategy that secures all your crucial data so that it is no more dependent on the mobile devices and apps for its protection.
Mobile Information Management (MIM): Requirements[6]
From the perspective of the enterprise, the requirements for managing the lifecycle of corporate information are driven by the referential value of that information and the operating procedures or regulations that govern how that information is handled. Essentially, information management approaches are based on how and who creates the information, what it contains, where it is stored, how it is protected, who has access to it, and how it is disposed of. Instead of deploying point-based solutions to address this, enterprises need a single solution that is capable of adapting to data evolution to meet the mobile information management requirements of today. This includes:
- A centralized information hub: Creating a common and global information repository allows the enterprise to apply rules and extract value from all information at the edge and in the margins, regardless of the device(s) it is created on, accessed from, or synchronized to.
- Unified backup, file sync, and file sharing: Unifying how information is protected, synchronized, and shared, empowers the mobile workforce to perform those information-related actions themselves thus removing a huge OPEX burden from the enterprise. Relying on a central information hub, the enterprise can better address information requirements by applying rules and policies at granular or global levels.
- Policy-based information management: It is the speed at which content, ownership, and value change that can quickly cause a point-based solution to become extinct—where the characteristics of the data surpasses the capabilities of the solution. With a centralized information hub, policies can be applied to manage and control the mobility of information. More importantly those policies and adherence to them, can be monitored to prevent the policy from drifting away from compliance standards as the data changes. Policies must affect how information is protected, shared, and accessed at a global and granular level to be truly effective.
- Information intelligence: With corporate information being created, disseminated, and accessed at all times, enterprises need mechanisms to understand the information and assess its value to the business. Only then can the information be properly classified and remain outside the margins. A central information hub provides a single point for all corporate information from which analytics, searching, content-specific policies, and usage data can be discerned. In effect, this approach allows the organization to better utilize infrastructure, maintain control over information, and effectively balance risk with workforce productivity.
- Information security: Mobile workforce access to corporate information can occur through various points, some of which are services and routes managed by IT, others are not. Managing mobile information effectively means relying on a solution that provides data encryption services while the data is at rest and in flight. It also means being able to define data privileges at a granular level and controlling user access with the highest authentication processes.
- Information compliance and auditability: As organizations are facing more and more information-specific regulations outside of their standard operating procedures, guaranteeing information integrity and a defensible position regarding compliance is challenging. The same analytics requirement listed earlier can also be used to address compliance and auditability. This can be done especially when defined policies use analytics services to validate information alignment to compliance policies before actions are taken on it. This is yet another value add of a centralized information hub. Lastly, to address compliance- and audit-related activities, these analytics can be used in the early case assessment phases to identify both the data and the information custodian without compromising the workforce productivity improvements that underpins the mobile workforce.
Implementing Mobile Information Management (MIM)[7]
MIM can be approached in many ways, there might even be an Enterprise policy that can be reused but if you are starting from scratch the recommended approach is to start out simple with two categories, one for Corporate Data and another for Non-corporate Data as portrayed in figure 4. You can then start by securing all Corporate Data if needed and after that start drilling down adding more categories as you identify them thereby providing the possibility of developing a diversified MIM policy dependent on the need for accessibility and security for each category.
Before implementing and configuring a MIM system the following are examples but not limited to what would need to be defined:
- Information Lifecycle Management Strategy
- Information Classification
- Mobile OS
An example of MIM is Apples iOS 7 Open In Management function which offers:
- Managed apps can send data to both managed and unmanaged apps
- Managed apps can send data only to other managed apps
- Unmanaged apps can send data to both managed and unmanaged apps
- Unmanaged apps can send data only to other unmanaged apps
- Managed apps are deployed by the Enterprise app store where unmanaged apps are downloaded by the user directly from public app stores.
Another example is Samsung’s Knox product on Android where a containerized area is created on the mobile device itself where corporate data are stored. It is not possible for users to access data within Knox from apps outside Knox on the mobile device.
MIM must not be confused with MCM which focuses on providing secure content capabilities to your mobile users.
Mobile Information Management High level model(see figure below)
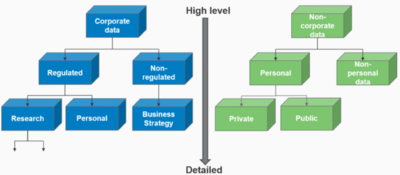
source: Digital Future Today
Mobile Information Management (MIM): Pros and Cons[8]
MIM referred to as Mobile Information Management are essentially cloud providers that allow you to sync information from mobile devices to the rest of your devices.
- Pros
- Centralized location for data and information.
- Ability to access information from almost any device and share between multiple platforms.
- Cons
- Security around the information is an unknown.
- Monitoring becomes significantly difficult.
Despite its promise, mobile information management faces significant obstacles in the enterprise mobility management (EMM) market. The major roadblock has to do with integration; MIM vendors will have to develop standards or partnerships with manufacturers and developers so their devices and apps can read and process the protections placed on data. MIM is often mentioned in security discussions in conjunction with mobile device management (MDM) and mobile application management (MAM ). MDM focuses on mobile device activation, enrollment and provisioning while MAM focuses on software delivery, licensing, configuration, maintenance, policy enforcement and usage tracking.[9]
See Also
Mobile Application
Mobile Application Management (MAM)
Mobile Content Management (MCM)
Mobile Device Management (MDM)
Enterprise Mobility
Enterprise Mobility Management (EMM)
Bring Your Own Device (BYOD)
References
- ↑ Definition of Mobile Information Management (MIM) HP
- ↑ Mobile Information Management (MIM) cioreview.com
- ↑ How Mobile Information Management Works Webopedia
- ↑ Mobile Information Management (MIM) Functions silicon.de
- ↑ 5 Tips To Make Your Mobile Information Management (MIM) Strategy Better appknow blog
- ↑ Adapting to data evolution to meet the mobile information management requirements of today HP
- ↑ Implementing Mobile Information Management (MIM) Digital Future Today
- ↑ Pros and Cons of Mobile Information Management (MIM) TrustedSec
- ↑ mobile information management (MIM) TechTarget
Further Reading
- How do you define "mobile information management"? Will it ever become a reality? Brian Madden
- Mobile Devices: BYOD, MDM, MAM, MIM, BRB… LOL, What Gives? Jamie Davis.Safe Systems
- The Transformative Role of Mobile Devices in an Enterprise Network CIO Review
