Enterprise Mobility Management (EMM)
Definition of Enterprise Mobility Management (EMM)
Enterprise Mobility Management (EMM) is the distribution, organization and control of mobile devices (cell phones, smartphones, tablet, laptops, etc.) used in enterprise mobility. As mobile devices are susceptible to loss or theft, good EMM is vital for companies who wish to protect themselves from data breaches or other privacy concerns. EMM ensures that the mobile devices used by mobile employees are secure enough to protect the company’s data and private information. This can be achieved either by restricting which employee/device has access to what information, by insisting on VPN and HTTPS connections, by restricting app download or by password protecting the devices.[1]
EMM is primarily centered on the enterprise governance, security, management and control of mobile computing technologies. It encompass processes and policies across all mobile devices that have part or a major stake within business processes, such as smartphones, tablet PCs and laptops. EMM’s scope is typically focused on security, application integration and management, as well as the financial implications of such solutions. For example, an enterprise's EMM policy must ensure that the enterprise application is integrated and usable by mobile devices, while providing and ensuring secure access mechanisms. Moreover, the organization must control and manage the financial costs involved in providing such solutions to company/employee owned devices.[2]
EMM typically involves some combination of mobile device management (MDM), mobile application management (MAM) and mobile information management (MIM). MDM focuses on locking down mobile devices, while MAM focuses on controlling which users can access which applications and MIM focuses on allowing only approved applications to access corporate data or transmit it. These three technologies all address specific concerns, but do not provide complete solutions for the problems that enterprise mobility can cause or make worse. The overlap between MDM, MAM and MIM is actually quite minimal. The challenge lies in managing all three concerns with minimal overhead. As more organizations adopt enterprise mobility management, vendors have started to productize EMM, usually by adding MAM or MIM features to their MDM products or vice versa. An enterprise app store or other application delivery and deployment technology is also a common component of EMM products.[3]
The Need For EMM[4]
With users needing access to enterprise data and applications and IT admins requiring visibility to the whereabouts of a device, the business case for EMM should be easy. However, many organizations are still unable to meet these needs. Restricting the ability to root or jailbreak phones is critical to the enterprise. While traditionally a complex operation relegated to highly technical users, a simple Google search and download will render a mobile device wide open. At a simpler level, organizations need to prevent the installation of unapproved apps, including encrypted chat and malware. Even iPhones aren't immune; last September, a number of Chinese developers accidentally published apps with the XcodeGhost malware because downloading Xcode (the Apple development platform) took too long from China. On the Android side, we learned of security gaps, notably the Stagefright malware discovered by Israeli startup Zimperium. With dozens of Android versions and carrier-controlled firmware updates, it takes months (or longer) to bring devices up to patched versions. There is also the case of operational simplicity. Organizations require a simple way to automate time- and labor-intensive tasks, such as provisioning large quantities of devices, adding or removing users, shutting off built-in features (such as camera, audio, fingerprint sensor, location services and other items), along with removing apps and resetting devices; this is critical as the number of mobile devices scale. In the case of a growing contingent workforce, organizations have to balance productivity and enablement with security and management. Ultimately, a good EMM program will allow organizations to have control and visibility (including reporting and analytics), while being invisible to the end users.
Forming an Enterprise Mobility Management strategy:Key factors[5]
An Enterprise Mobility Management strategy lists and describes your company’s key requirements and positions on a wide range of mobility issues. The goal is to align mobile IT priorities with short-term and long-term business goals. It should be a formal document created by IT, HR, and Legal, but must include input from all stakeholders. If your organization doesn’t have an EMM strategy today, there’s no reason to postpone it. Think of it as a living document. The discussions you have while you build it will allow you to make the critical decisions you need to get an effective long-term EMM solution in place. Your Enterprise Mobility Management strategy answers important basic questions such as:
- Who pays for hardware, software, and wireless services?
- Are BYOD and COPE devices supported, and if so, how? And for which business units, roles or individuals?
- Which employees get what type of mobile device, e.g. laptop, smartphone, tablet?
- How much security is required, for which user types, and how will it be enforced?
- What data, applications and functions are allowed on which enterprise devices?
- Who supports the mobile device users and manages the devices?
- How will you handle LCM (Lifecycle Management) when it’s time to upgrade devices and apps?
But this is only the beginning. There are several categories to weigh, across management, security and implementation. If your stakeholders can form clear opinions on these issues, you’ll be on your way to an Enterprise Mobility Management strategy. And with that strategy in place, finding the right EMM solution (and optimizing it from there) will be much, much easier.
Buying Considerations for Enterprise Mobility Management (EMM) Software[6]
- Prepare for the Long Term: Make sure that the chosen EMM tool can configure both employee-owned or corporate-owned mobile devices for optimal performance, effective containerization, and security. Buyers should also understand that EMM software needs to exist for the long term, so they need to anticipate mobile-specific issues that may appear in the future.
- Operating Systems: EMM software needs to stay on top of constantly evolving mobile operating systems and devices, which come with their own brands of security threats and user expectations. Therefore, look at EMM software products that will support differing operating systems instead of Android or Apple-specific operating systems, unless they know they will exclusively use one or the other.
- Measured Rollouts/User Adoption: Look at EMM software as the closest thing to device control and information security that can be afforded to the business world. Therefore, measured rollouts of EMM software ensure its successful adoption by employees who may initially hedge against an all-encompassing mobile device management tool.
- Onboarding Time: Onboarding an EMM solution is difficult because they are comprehensive software platforms that perform multiple functions. EMM software configures mobile device operating systems, handles device and app lifecycles, and supports identification tools. The cost it takes to manage corporate-owned devices is now being displaced by the time it takes for employees to get accustomed to EMM-managed personal devices. Buyers should also consider whether it makes more sense to spend the time onboarding employees and integrating multiple mobile management systems, which run the risk of being incompatible.
- Small Footprint: A good EMM solution enables IT staff and administrators to have control, visibility, reporting, and analytics without impeding too much on employees’ regular use of their devices. Like with other types of software that protect the end user, the more intrusive it is, the more annoying it will be for the user, and the less likely they will want to use the tool. Try out EMM software to see if it operates, more or less, quietly in the background.
- Risk Management: Look at EMM software products that can limit network resources or constantly monitor to protect from rogue or not-fully managed devices. Only consider EMM platforms that can block or prevent the installation of unapproved applications, and let administrators set up multiple access settings.
- Cloud vs. On-Premise vs. Hybrid: Consider the pros and cons of cloud-based, on-premise, or hybrid cloud/on-premise EMM solutions. Consider which deployment will help offset the amount of space the software will utilize, and any costs associated with maintenance and administrative overhead of the tool.
- Business Needs: Consider the organization's requirements and look at which feature sets of EMM tools best meet those requirements. The support of features like geo-fencing, containerization, bring-your-own-device support, and alignment with wearable technology should also be considered.
- Scalability: Mobile technology is constantly changing and growing, so the best EMM product will be the one that has the flexibility to adapt and ability to scale, both in terms of workforce size and future business strategy.
Enterprise Mobility Management (EMM): Security[7]
Because mobile devices are easily lost or stolen, data on those devices is vulnerable. Enterprise mobility management is a set of systems intended to prevent unauthorized access to enterprise applications and/or corporate data on mobile devices. These can include password protection, encryption and/or remote wipe technology, which allows an administrator to delete all data from a misplaced device. With many systems, security policies can be centrally managed and enforced. Such device management systems are programmed to support and cooperate with the application programming interfaces (APIs) from various device makers to increase security compliance. The data transfer between mobile device and the enterprise should always be encrypted, for example through a VPN tunnel or over HTTPS. Mobile devices in companies with "bring your own device" (BYOD) policies are often used both personally and professionally. In these cases, corporate IT has less control over whether malware is on the device and what damage may be caused to corporate data. Apart from careful user behavior - data storage on the mobile device should be limited and centrally organized. The diversity of Android devices appeals to consumer buyers, but is a source of anxiety for IT security experts. OpenSignal, a UK-based mobile company, recently published a survey of almost 700,000 devices and reported approximately 12,000 distinct Android devices using eight different versions of the Google operating system. For many IT organizations charting out their BYOD strategy, this translates into security risks that are tough to monitor and control.
Enterprise Mobility Management Stages[8]
- 1. Planning/Strategies Formulation- To plan for any strategy a well-defined enterprise policies are required, as enterprise policies enables security & management to get engaged with desired solutions. Within these solutions mobile offering is an imperative part which should be identified before planning any further action. These mobile strategies will provide the way to go ahead on Enterprise mobility.
- 2. Product/Solution- Enterprises prefers to use catalyst according to their business nature, flow & its execution. Although it is not necessary that these catalyst have mobile offerings. But now-a-days mobile products, solutions or devices are inevitable part of these solutions.
- 3. Product/Service management- Once the strategies are formulated & product/solutions are designed and well implemented,then maintenance support is important part to deal with. Support and maintenance of the system will deal with well-structured process, security, change management and availability.
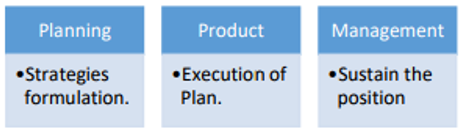
source: IJESRT
EMM Solution Approaches[9]
- Device Centric Approach
- Solution runs as a daemon process in device. This would be native application
- Mainly an MD approach which controls and monitors at device level
- Containerization with SDK
- Solution is provided through SDK/library which should be integrated with mobile application
- Many MAM and BYOD go with this approach due to more control and security at app and data level.
- There are containeriztion approaches where multiple applications are executed in single container environment to create virtual data partitioning between personal and enterprise apps on the device.
- Advanced features like data sharing between enterprise apps, persona based apps and data management, custom app specific policies etc., is possible
- Containerization without SDK
- Solution is to wrap the application with secured container without any code integration or source code changes which is the main advantage of this approach.
- Many MAM and BYOD solution providers prefer this approach.
- Executable of mobile application just needs to be deployed at the vendor's on-premise enterprise network or on a secure cloud environment.
- There can be some limitations with this approach like advanced features, allowed data sharing between enterprise apps, supporting multi user profiles, scenario based authorization etc,... may not be possible.
- Remote Streaming
- This approach creates a virtually separate space on mobile application where app is located from device specific settings, configurations and interaction with other apps in any means.
- Solution delivers applications on users' devices through application streaming from hosted servers in the data center.
- This solution is more generic in terms of device types (hand held devices, desktops, printers and other peripherals), operating system/platform type or nature of an application (native or thin client).
- Network Based
- This unique approach gathers the real-time contextual information from the network, devices (either laptop, hand held or any other non-telephonic devices) and users.
- It runs more on network measurement and instrumentation out of IP packets traversing on network between device and enterprise server wall.
- This provides security framework for any wireless devices, desktops or even wired/wireless peripheral devices like printers since they detect data at network layer like SSL/VPN/WLAN.
- Limitation lies in the fact that approach has a huge dependency on the infrastructure.
Key Benefits of Enterprise Mobility Management (EMM) Software[10]
With enterprise mobility management (EMM) software, you can:
- Blend the best of mobile application management and mobile device management functionality
- Enforce employee adherence to company policy
- Allow employees to experience a familiar, consumer-like mobile experience when using mobile devices for work
- Allow companies to deploy a mobile-first (or close to mobile first) strategy
- Unify the management and auditing of mobile devices onto a singular platform
- Improve security measures
- Scale according to business requirements and size
See Also
Mobile Application
Mobile Application Management (MAM)
Mobile Content Management (MCM)
Mobile Device Management
Mobile Information Management (MIM)
Enterprise Mobility
Bring Your Own Device (BYOD)
References
- ↑ Defining Enterprise Mobility Management (EMM) Investopedia
- ↑ Explaining Enterprise Mobility Management (EMM) [1]
- ↑ What is Enterprise Mobility Management (EMM) TechTarget
- ↑ The Need for Enterprise Mobility Management (EMM) Josh Linder
- ↑ The Key factors in Forming an Enterprise Mobility Management strategy Blackberry
- ↑ Buying Considerations for Enterprise Mobility Management (EMM) Software G2 Crowd
- ↑ Enterprise Mobility Management (EMM): Security Wikipedia
- ↑ Enterprise Mobility Management Stages Dr. Shine David*, Mr. Raghvendra Singh Dikhit, Jay Shrivastava, Twinkle Sawlani
- ↑ Enterprise Mobility Management (EMM) Solution Approaches Infosys
- ↑ Key Benefits of Enterprise Mobility Management (EMM) Software G2 Crowd
Further Reading
- Why the Market Moved From Mobile Device Management to Enterprise Mobility Management Technology Advice
- How to choose the right enterprise mobility management tool ComputerWorld
- The CIO's Guide to EMM: 10 Critical decision points Blackberry Whitepaper
- 10 Mobile Security Requirements for the BYOD Enterprise
- Enterprise Mobility Strategy in the Cloud
