Information Systems Security (INFOSEC)
Definition of Information Systems Security (INFOSEC
Information Systems Security, also known as INFOSEC, is a broad subject within the field of information technology (IT) that focuses on protecting computers, networks, and their users. Almost all modern companies, as well as many families and individuals, have justified concerns about digital risks to their well-being. These threats come in all shapes and sizes, including theft of private information in a databasehack, installation of malicious software on a machine and intentional service disruptions.[1]
Generally information systems can be broken up into two main groups, IT security and information assurance. IT security is the security applied to technology, usually the computer system. IT security specialists are responsible for keeping all the technology in companies safe from cyber attacks. Information assurance is the act of ensuring data is not lost when issues arise, including natural disasters, computer/server malfunction, or theft. IT security specialists generally provide information assurance by having off-site backups of data to combat these problems.
Information systems security does not just deal with computer information, but also protecting data and information in all of its forms, such as telephone conversations. Risk assessments must be performed to determine what information poses the biggest risk. For example, one system may have the most important information on it and therefore will need more security measures to maintain security. Business continuity planning and disaster recovery planning are other facets of an information systems security professional. This professional will plan for what could happen if a major business disruption occurs, but still allow business to continue as usual. The term is often used in the context of the U.S. Navy, who defines INFOSEC as:
COMPUSEC + COMSEC + TEMPEST = INFOSEC
Where COMPUSEC is computer systems security, COMSEC is communications security, and TEMPEST is compromising emanations.[2]
Information System security is a subset of Information Security. While Information Security involves everything related to the information all the way up to Corporate lawyers sending cease and desist letters to journalists, Information Systems Security is only related to the systems where system information resides. e.g. once a employee legally puts the data on a thumbdrive it is no longer covered by Information System Security but by Information Security in general.[3]
Information Systems Security Principles[4]
The basic components of information systems security are most often summed up by the so-called CIA triad: confidentiality, integrity, and availability.
- Confidentiality is perhaps the element of the triad that most immediately comes to mind when you think of information security. Data is confidential when only those people who are authorized to access it can do so; to ensure confidentiality, you need to be able to identify who is trying to access data and block attempts by those without authorization. Passwords, encryption, authentication, and defense against penetration attacks are all techniques designed to ensure confidentiality.
- Integrity means maintaining data in its correct state and preventing it from being improperly modified, either by accident or maliciously. Many of the techniques that ensure confidentiality will also protect data integrity—after all, a hacker can't change data they can't access—but there are other tools that help provide a defense of integrity in depth: checksums can help you verify data integrity, for instance, and version control software and frequent backups can help you restore data to a correct state if need be. Integrity also covers the concept of non-repudiation: you must be able to prove that you've maintained the integrity of your data, especially in legal contexts.
- Availability is the mirror image of confidentiality: while you need to make sure that your data can't be accessed by unauthorized users, you also need to ensure that it can be accessed by those who have the proper permissions. Ensuring data availability means matching network and computing resources to the volume of data access you expect and implementing a good backup policy for disaster recovery purposes.
In an ideal world, your data should always be kept confidential, in its correct state, and available; in practice, of course, you often need to make choices about which information security principles to emphasize, and that requires assessing your data. If you're storing sensitive medical information, for instance, you'll focus on confidentiality, whereas a financial institution might emphasize data integrity to ensure that nobody's bank account is credited or debited incorrectly.
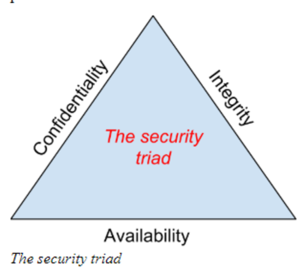
source: Dave Bourgeois and David T. Bourgeois
Types of Security Controls[5]
It is the responsibility of the information owner (usually a Sr. executive within the management group or head of a specific dept) to protect the data and is the due care (liable by the court of law) for any kind of negligence. Security Controls can be classified into three categories
- Administrative Controls which include
- Developing and publishing of policies, standards, procedures, and guidelines.
- Screening of personnel.
- Conducting security-awareness training and
- Implementing change control procedures.
- Technical or Logical Controls which include
- Implementing and maintaining access control mechanisms.
- Password and resource management.
- Identification and authentication methods
- Security devices and
- Configuration of the infrastructure.
- Physical Controls which include
- Controlling individual access into the facility and different departments
- Locking systems and removing unnecessary floppy or CD-ROM drives
- Protecting the perimeter of the facility
- Monitoring for intrusion and
- Environmental controls.
Types of Information Systems Security (INFOSEC)[6]
- Application security: Application security is a broad topic that covers software vulnerabilities in web and mobile applications and application programming interfaces (APIs). These vulnerabilities may be found in authentication or authorization of users, integrity of code and configurations, and mature policies and procedures. Application vulnerabilities can create entry points for significant InfoSec breaches. Application security is an important part of perimeter defense for InfoSec.
- Cloud security: Cloud security focuses on building and hosting secure applications in cloud environments and securely consuming third-party cloud applications. “Cloud” simply means that the application is running in a shared environment. Businesses must make sure that there is adequate isolation between different processes in shared environments.
- Cryptography: Encrypting data in transit and data at rest helps ensure data confidentiality and integrity. Digital signatures are commonly used in cryptography to validate the authenticity of data. Cryptography and encryption has become increasingly important. A good example of cryptography use is the Advanced Encryption Standard (AES). The AES is a symmetric key algorithm used to protect classified government information.
- Infrastructure security: Infrastructure security deals with the protection of internal and extranet networks, labs, data centers, servers, desktops, and mobile devices.
- Incident response: Incident response is the function that monitors for and investigates potentially malicious behavior. In preparation for breaches, IT staff should have an incident response plan for containing the threat and restoring the network. In addition, the plan should create a system to preserve evidence for forensic analysis and potential prosecution. This data can help prevent further breaches and help staff discover the attacker.
- Vulnerability management: Vulnerability management is the process of scanning an environment for weak points (such as unpatched software) and prioritizing remediation based on risk.
In many networks, businesses are constantly adding applications, users, infrastructure, and so on. For this reason, it is important to constantly scan the network for potential vulnerabilities. Finding a vulnerability in advance can save your businesses the catastrophic costs of a breach.
INFOSEC Certifications[7]
- Certified Ethical Hacker (CEH): This is a vendor-neutral certification from the EC-Council, one of the leading certification bodies. This security certification, which validates how much an individual knows about network security, is best suited for a penetration tester role. This certification covers more than 270 attacks technologies. Prerequisites for this certification include attending official training offered by the EC-Council or its affiliates and having at least two years of information security-related experience.
- Certified Information Systems Auditor (CISA): This certification is offered by ISACA, a nonprofit, independent association that advocates for professionals involved in information security, assurance, risk management and governance. The exam certifies the knowledge and skills of security professionals. To qualify for this certification, candidates must have five years of professional work experience related to information systems auditing, control or security.
- Certified information security manager (CISM): CISM is an advanced certification offered by ISACA that provides validation for individuals who have demonstrated the in-depth knowledge and experience required to develop and manage an enterprise information security program. The certification is aimed at information security managers, aspiring managers or IT consultants who support information security program management.
- GIAC Security Essentials (GSEC): This certification created and administered by the Global Information Assurance Certification organization is geared toward security professionals who want to demonstrate they are qualified for IT systems hands-on roles with respect to security tasks. Candidates are required to demonstrate they understand information security beyond simple terminology and concepts.
See Also
Data Security
Security Architecture
Security Policy
Security Reference Model (SRM)
Information Security Governance
Information Security
Adaptive Security Architecture (ASA)
Business Model for Information Security (BMIS)
Common Data Security Architecture (CDSA)
Payment Card Industry Data Security Standard (PCI DSS)
Data Security
Computer Security
Enterprise Information Security Architecture (EISA)
Fault Configuration Accounting Performance Security (FCAPS)
Graduated Security
Information Systems Security (INFOSEC)
Information Security Management System (ISMS)
Information Technology Security Assessment
Mobile Security
Network Security
Cyber Security
References
- ↑ Definition - What Does Information Systems Security (INFOSEC) Mean? Computer Science Degree Hub
- ↑ Expalining Information Systems Security (INFOSEC) Techopedia
- ↑ What is Information Systems Security Related To? Jesper Jurcenoks
- ↑ Information Systems Security Principles CSO Online
- ↑ Types of Security Controls Wikibooks
- ↑ What are the Different Types of INFOSEC? Cisco
- ↑ INFOSEC Certifications Techtarget
