Ransomware
Ransomware, or Ransom malware, is a type of malware that prevents users from accessing their system or personal files and demands ransom payment in order to regain access. The earliest variants of ransomware were developed in the late 1980s, and payment was to be sent via snail mail. Today, ransomware authors order that payment be sent via cryptocurrency or credit card.[1]
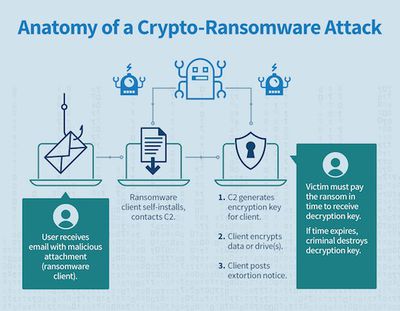
Anatomy of a Ransomware Attack[2]
A common form of delivering ransomware is through malicious attachments to email messages. Users are convinced against their better judgment – through social engineering – to open the attachment. The attachment is typically a form of self-installing malware, often called a Trojan or virus dropper file. Once installed, the dropper enrolls in a cyberattacker’s botnet by contacting the botnet command and control (C2). When contacted, the C2 will generate and return encryption-keying material for the ransomware dropper (and possibly additional malicious code). The ransomware dropper will use the keying material to encrypt personal files on the infected device. It then posts an extortion notification, demanding that the victim pay a ransom payment for a key that will decrypt the now inaccessible data.
Many ransomware attackers threaten victims with permanent loss of their personal files if the ransom is not paid within a 24-hour timeframe. To enhance deception, some ransomware notifications impersonate law enforcement or government agencies and represent the extortion as a fine.
How Ransomware Works[3]
The good news is that ransomware does not usually appear on its own. It must be activated in order to deliver its payload, usually through a malicious link or attachment in an email. There are generally five steps required for ransomware to achieve its objective:
- The System Is Compromised: The majority of ransomware attacks start life as a social engineering exercise, usually in the form of an attachment or malicious link. The aim is to entice the user to click on these objects in order to activate the malware.
- The Malware Takes Control: Once the malware has taken control of the system, certain file types will be encrypted and access will be denied to users.
- The Victim Is Notified: For the ransom to be paid, the user must be aware of the demands of the criminals. At this point, they will usually receive notification on the screen explaining the demands and how they can regain access.
- The Ransom Is Paid: Once they have system access, attackers will either identify and encrypt certain file types or deny access to the entire system.
- Full Access Is Returned: In the majority of cases, attackers return full control to the victim. It is in their interest to do this; failure to do so would mean few organizations would be willing to pay if they didn't believe their data would be restored.
History of Ransomware[4]
- Encrypting ransomware: The first known malware extortion attack, the "AIDS Trojan" written by Joseph Popp in 1989, had a design failure so severe it was not necessary to pay the extortionist at all. Its payload hid the files on the hard drive and encrypted only their names, and displayed a message claiming that the user's license to use a certain piece of software had expired. The user was asked to pay US$189 to "PC Cyborg Corporation" in order to obtain a repair tool even though the decryption key could be extracted from the code of the Trojan. The Trojan was also known as "PC Cyborg". Popp was declared mentally unfit to stand trial for his actions, but he promised to donate the profits from the malware to fund AIDS research.
- The idea of abusing anonymous cash systems to safely collect ransom from human kidnapping was introduced in 1992 by Sebastiaan von Solms and David Naccache. This electronic money collection method was also proposed for cryptoviral extortion attacks. In the von Solms-Naccache scenario a newspaper publication was used (since bitcoin ledgers did not exist at the time the paper was written).
- The notion of using public key cryptography for data kidnapping attacks was introduced in 1996 by Adam L. Young and Moti Yung. Young and Yung critiqued the failed AIDS Information Trojan that relied on symmetric cryptography alone, the fatal flaw being that the decryption key could be extracted from the Trojan, and implemented an experimental proof-of-concept cryptovirus on a Macintosh SE/30 that used RSA and the Tiny Encryption Algorithm (TEA) to hybrid encrypt the victim's data. Since public key crypto is used, the cryptovirus only contains the encryption key. The attacker keeps the corresponding private decryption key private. Young and Yung's original experimental cryptovirus had the victim send the asymmetric ciphertext to the attacker who deciphers it and returns the symmetric decryption key it contains to the victim for a fee. Long before electronic money existed Young and Yung proposed that electronic money could be extorted through encryption as well, stating that "the virus writer can effectively hold all of the money ransom until half of it is given to him. Even if the e-money was previously encrypted by the user, it is of no use to the user if it gets encrypted by a cryptovirus". They referred to these attacks as being "cryptoviral extortion", an overt attack that is part of a larger class of attacks in a field called cryptovirology, which encompasses both overt and covert attacks. The cryptoviral extortion protocol was inspired by the parasitic relationship between H. R. Giger's facehugger and its host in the movie Alien.
- Examples of extortionate ransomware became prominent in May 2005. By mid-2006, Trojans such as Gpcode, TROJ.RANSOM.A, Archiveus, Krotten, Cryzip, and MayArchive began utilizing more sophisticated RSA encryption schemes, with ever-increasing key-sizes. Gpcode.AG, which was detected in June 2006, was encrypted with a 660-bit RSA public key. In June 2008, a variant known as Gpcode.AK was detected. Using a 1024-bit RSA key, it was believed large enough to be computationally infeasible to break without a concerted distributed effort.
- Encrypting ransomware returned to prominence in late 2013 with the propagation of CryptoLocker—using the Bitcoin digital currency platform to collect ransom money. In December 2013, ZDNet estimated based on Bitcoin transaction information that between 15 October and 18 December, the operators of CryptoLocker had procured about US$27 million from infected users. The CryptoLocker technique was widely copied in the months following, including CryptoLocker 2.0 (thought not to be related to CryptoLocker), CryptoDefense (which initially contained a major design flaw that stored the private key on the infected system in a user-retrievable location, due to its use of Windows' built-in encryption APIs), and the August 2014 discovery of a Trojan specifically targeting network-attached storage devices produced by Synology. In January 2015, it was reported that ransomware-styled attacks have occurred against individual websites via hacking, and through ransomware designed to target Linux-based web servers.
- The Microsoft Malware Protection Center identified a trend away from WSF files in favour of LNK files and PowerShell scripting. These LNK shortcut files install Locky ransomware by automating infection operations rather than relying on traditional user downloads of WSF files—all of which is made possible by the universal PowerShell Windows application. Unfortunately, cybercriminals have been able to leverage PowerShell for their attacks for years. In a recent report, the application was found to be involved in nearly 40% of endpoint security incidents. While attackers have been finding weaknesses in the Windows operating system for years, it's clear that there's something problematic with PowerShell scripting.
- Some ransomware strains have used proxies tied to Tor hidden services to connect to their command and control servers, increasing the difficulty of tracing the exact location of the criminals. Furthermore, dark web vendors have increasingly started to offer the technology as a service. Symantec has classified ransomware to be the most dangerous cyber threat.
- Non-encrypting ransomware: In August 2010, Russian authorities arrested nine individuals connected to a ransomware Trojan known as WinLock. Unlike the previous Gpcode Trojan, WinLock did not use encryption. Instead, WinLock trivially restricted access to the system by displaying pornographic images and asked users to send a premium-rate SMS (costing around US$10) to receive a code that could be used to unlock their machines. The scam hit numerous users across Russia and neighbouring countries—reportedly earning the group over US$16 million.
- In 2011, a ransomware Trojan surfaced that imitated the Windows Product Activation notice, and informed users that a system's Windows installation had to be re-activated due to "[being a] victim of fraud". An online activation option was offered (like the actual Windows activation process), but was unavailable, requiring the user to call one of six international numbers to input a 6-digit code. While the malware claimed that this call would be free, it was routed through a rogue operator in a country with high international phone rates, who placed the call on hold, causing the user to incur large international long distance charges.
- In February 2013, a ransomware Trojan based on the Stamp.EK exploit kit surfaced; the malware was distributed via sites hosted on the project hosting services SourceForge and GitHub that claimed to offer "fake nude pics" of celebrities. In July 2013, an OS X-specific ransomware Trojan surfaced, which displays a web page that accuses the user of downloading pornography. Unlike its Windows-based counterparts, it does not block the entire computer, but simply exploits the behaviour of the web browser itself to frustrate attempts to close the page through normal means.
- In July 2013, a 21-year-old man from Virginia, whose computer coincidentally did contain pornographic photographs of underage girls with whom he had conducted sexualized communications, turned himself in to police after receiving and being deceived by FBI MoneyPak Ransomware accusing him of possessing child pornography. An investigation discovered the incriminating files, and the man was charged with child sexual abuse and possession of child pornography.
- Leakware (also called Doxware): The converse of ransomware is a cryptovirology attack invented by Adam L. Young that threatens to publish stolen information from the victim's computer system rather than deny the victim access to it. In a leakware attack, malware exfiltrates sensitive host data either to the attacker or alternatively, to remote instances of the malware, and the attacker threatens to publish the victim's data unless a ransom is paid. The attack was presented at West Point in 2003 and was summarized in the book Malicious Cryptography as follows, "The attack differs from the extortion attack in the following way. In the extortion attack, the victim is denied access to its own valuable information and has to pay to get it back, where in the attack that is presented here the victim retains access to the information but its disclosure is at the discretion of the computer virus". The attack is rooted in game theory and was originally dubbed "non-zero sum games and survivable malware". The attack can yield monetary gain in cases where the malware acquires access to information that may damage the victim user or organization, e.g., the reputational damage that could result from publishing proof that the attack itself was a success.
- Mobile ransomware: With the increased popularity of ransomware on PC platforms, ransomware targeting mobile operating systems has also proliferated. Typically, mobile ransomware payloads are blockers, as there is little incentive to encrypt data since it can be easily restored via online synchronization. Mobile ransomware typically targets the Android platform, as it allows applications to be installed from third-party sources. The payload is typically distributed as an APK file installed by an unsuspecting user; it may attempt to display a blocking message over top of all other applications, while another used a form of clickjacking to cause the user to give it "device administrator" privileges to achieve deeper access to the system.
- Different tactics have been used on iOS devices, such as exploiting iCloud accounts and using the Find My iPhone system to lock access to the device. On iOS 10.3, Apple patched a bug in the handling of JavaScript pop-up windows in Safari that had been exploited by ransomware websites. It recently has been shown that ransomware may also target ARM architectures like those that can be found in various Internet-of-Things (IoT) devices, such as Industrial IoT edge devices.
- In August 2019 researchers demonstrated it's possible to infect DSLR cameras with ransomware.[63] Digital cameras often use Picture Transfer Protocol (PTP - standard protocol used to transfer files.) Researchers found that it was possible to exploit vulnerabilities in the protocol to infect target camera(s) with ransomware (or execute any arbitrary code). This attack was presented at the Defcon security conference in Las Vegas as a proof of concept attack (not as actual armed malware)
The Spread of Ransomware[5]
Ransomware attacks and their variants are rapidly evolving to counter preventive technologies for several reasons:
- Easy availability of malware kits that can be used to create new malware samples on demand
Use of known good generic interpreters to create cross-platform ransomware (for example, Ransom32 uses Node.js with a JavaScript payload)
- Use of new techniques, such as encrypting the complete disk instead of selected files
Today’s thieves don’t even have to be tech savvy. Ransomware marketplaces have sprouted up online, offering malware strains for any would-be cybercrook and generating extra profit for the malware authors, who often ask for a cut in the ransom proceeds.
Preventing Ransomware[6]
There are a number of defensive steps you can take to prevent ransomware infection. These steps are a of course good security practices in general, so following them improves your defenses from all sorts of attacks:
- Keep your operating system patched and up-to-date to ensure you have fewer vulnerabilities to exploit.
- Don't install software or give it administrative privileges unless you know exactly what it is and what it does.
- Install antivirus software, which detects malicious programs like ransomware as they arrive, and whitelisting software, which prevents unauthorized applications from executing in the first place.
- And, of course, back up your files, frequently and automatically! That won't stop a malware attack, but it can make the damage caused by one much less significant.
Ransomware Protection and Best Practices[7]
Ransomware can be devastating to an individual or an organization. Anyone with important data stored on their computer or network is at risk, including government or law enforcement agencies and healthcare systems or other critical infrastructure entities. Recovery can be a difficult process that may require the services of a reputable data recovery specialist, and some victims pay to recover their files. However, there is no guarantee that individuals will recover their files if they pay the ransom.
CISA recommends the following precautions to protect users against the threat of ransomware:
- Update software and operating systems with the latest patches. Outdated applications and operating systems are the target of most attacks.
- Never click on links or open attachments in unsolicited emails.
- Backup data on a regular basis. Keep it on a separate device and store it offline.
- Follow safe practices when browsing the Internet. Read Good Security Habits for additional details.
In addition, CISA also recommends that organizations employ the following best practices:
- Restrict users’ permissions to install and run software applications, and apply the principle of “least privilege” to all systems and services. Restricting these privileges may prevent malware from running or limit its capability to spread through a network.
- Use application whitelisting to allow only approved programs to run on a network.
- Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate inbound email to prevent email spoofing.
- Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
Configure firewalls to block access to known malicious IP addresses.
The Future of Ransomware[8]
It will not be surprising if ransomware change in a few years. In terms of potential, they can evolve into malware that disable entire infrastructure (critical not only to a business’s operation but also a city’s or even a nation’s) until the ransom is paid. Cybercriminals may soon look into approaches like hitting industrial control systems (ICS) and other critical infrastructure to paralyze not just networks but ecosystems. A key area that could become a bigger target for cybercriminals are payment systems, as seen with the Bay Area Transit attack in 2016 where the service provider’s payment kiosks were targeted with ransomware.
We have seen ransomware operators hit hospitals and transportation service providers. What would stop attackers from hitting even bigger targets like the industrial robots that are widely used in the manufacturing sector or the infrastructure that connect and run today’s smart cities? Online extortion is bound to make its way from taking computers and servers hostage to any type of insufficiently protected connected device, including smart devices, or critical infrastructure. The return on investment (ROI) and ease with which cybercriminals can create, launch, and profit from this threat will ensure it continues in the future.
See Also
Mobile Security
Network Security
Cyber Security
Data Security
Computer Security
Malvertising
Malware
Spyware
Ransomware
Virus
Information Technology Risk (IT Risk)
Risk
Risk Management
Risk Assessment
Risk Mitigation
IT Governance
References
- ↑ Definition - What Does Ransomware Mean? Malwarebytes
- ↑ Anatomy of a Ransomware Attack Icann
- ↑ How Ransomware Works Forcepoint
- ↑ History of Ransomware Wikipedia
- ↑ Why is ransomware spreading? McAfee
- ↑ How to prevent ransomware CSO Online
- ↑ Ransomware Protection and Best Practices CISA
- ↑ The Future of Ransomware Trendmicro