Network Based Application Recognition (NBAR)
Network Based Application Recognition (NBAR) is the mechanism used by some Cisco routers and switches to recognize a dataflow by inspecting some packets sent. The networking equipment which uses NBAR does a deep packet inspection on some of the packets in a dataflow, to determine which traffic category the flow belongs to. Used in conjunction with other features, it may then program the internal application-specific integrated circuits (ASICs) to handle this flow appropriately. The categorization may be done with Open Systems Interconnection (OSI) layer 4 info, packet content, signaling, and so on but some new applications have made it difficult on purpose to cling to this kind of tagging. The NBAR approach is useful in dealing with malicious software using known ports to fake being "priority traffic", as well as non-standard applications using dynamic ports. That's why NBAR is also known as OSI layer 7 categorization. On Cisco routers, NBAR is mainly used for quality of service and network security purposes.[1]
Applications in today's enterprise networks require different levels of service based upon business requirements. These requirements can be translated into network policies. The resources provided here assist you in configuring your network to provide the appropriate level of service to these applications. Mission critical applications including ERP and workforce optimization applications can be intelligently identified and classified using Network Based Application Recognition (NBAR). Once these mission critical applications are classified they can be guaranteed a minimum amount of bandwidth, policy routed, and marked for preferential treatment. Non-critical applications including Internet gaming applications and MP3 file sharing applications can also be classified using NBAR and marked for best effort service, policed, or blocked as required.[2]
Next Generation NBAR or NBAR2 is a backward compatible re-architecture of NBAR, designed with several new advantages that give greater granular control over network traffic while addressing new technologies and emerging security threats. Features include advanced classification techniques to identify new IP protocols, evasive applications (for example, Tor), cloud applications, and mobile applications. Further improvements include traffic accuracy techniques, custom protocols, common protocol library, and a new signature delivery using protocol packs that allow distribution of protocol updates outside of the Cisco operating release train enabling rapid response to market trends.
How NBAR Works[3]
NBAR provides intelligent network classification for network infrastructure. It has the ability to recognize a wide variety of applications, including those that dynamically assign Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) port numbers. Upon recognition of the application, the network assigns it specific services. Using quality-of-service (QoS) features, NBAR helps ensure network bandwidth is being used to meet enterprise objectives. This means:
- guaranteed bandwidth for critical applications;
- limited bandwidth for non-critical applications;
- avoiding congestion by dropping specific packets; and
- marking specific packets to enable end-to-end QoS from.
While many network administrators are using monitoring tools to oversee network link usage, these tools only provide a partial view – the volume of traffic, but not type of traffic. NBAR examines traffic on a designated router interface, identifying it by the application. This is done by mapping traffic ports to standard and non-standard protocols – much more manageable than access control lists (ACLs) that require precise matching of protocols and ports. NBAR supports a wide range of network protocols, including some of these stateful protocols that were difficult to classify before NBAR:
- HTTP classification by URL, host, and Multipurpose Internet Mail Extensions (MIME) type
- Oracle SQL*Net
- Sun RPC
- Microsoft Exchange
- UNIX r commands
- VDOLive
- RealAudio
- Microsoft Netshow
- FTP
- StreamWorks
- Trivial File Transfer Protocol (TFTP)
NBAR2 provides support for an even greater number of protocol types, including non-TCP and non-UDP IP protocols, statically assigned TCP and UDP port numbers, dynamically assigned TCP and UDP port numbers, and subport classification or classification based on deep packet inspection. Network administrators can obtain new protocol support by downloading protocol packs from Cisco Connection Online.
NBAR and Classification[4]
Classification is the first step in implementing QoS. NBAR can be used to implement classification. NBAR is a Cisco IOS classification engine that inspects packets and classifies them based on their application type. This can be something as simple as examining the TCP or UDP port numbers in the transport header of a segment, or it can as complex as examining information in HTML headers or web content. Basically, NBAR can inspect traffic from Layers 3 through 7. This inspection can look for the following types of information:
- TCP and UDP port numbers in the transport-layer segment header
- Dynamic TCP and UDP port numbers assigned for additional connections for an application, such as FTP (similar to the inspection process that CBAC uses when examining applications that open additional connections)
- Subport information, which is information contained in the application layer data, such as application commands or data types
- Layer 3 IP protocols (other than TCP and UDP)
Classification of traffic with NBAR can be done dynamically or manually. NBAR supports the Protocol Discovery feature, which allows NBAR to discover automatically application protocols that enter or leave an interface. This feature also maintains per-protocol statistics, such as the number of input and output packets and bytes, bit rates, and other statistical information. With manual classification, you define the traffic types that NBAR should examine. After NBAR has identified an application, the appropriate classification can take place, marking the packet header with the corresponding IP Precedence or DSCP value.
Classification Process
NBAR enables you to classify traffic from information found in Layers 3 through 7 of the OSI reference model. The first step in setting up NBAR is to create classes for traffic that you want NBAR to inspect. You can have NBAR examine many things, such as the application type, specific addresses for connections, data in a connection, and the length of a packet. Based on your matching criteria, NBAR places matching traffic into your specified class (or grouping).
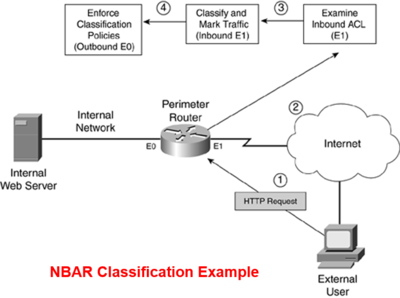
When you have created your classification rules, you create a policy that marks the traffic. For IP traffic, you use IP Precedence to group (classify) the traffic. The IP Precedence standard (and DSCP) uses the bits in the ToS field in an IP packet to classify the traffic. Both of these functions are performed on the ingress interface (as traffic enters your router). Then you define what action(s) will occur for marked traffic when it leaves a specific egress interface(s) on your router. Normally, with QoS, this affects how the packet is queued up before it is transmitted out the interface. However, you can define other policies for this traffic, such as limiting its bandwidth or even dropping the traffic, based on the classification, of course. The figure below illustrates this process.
The following steps occur, with reference to the numbering in the figure above:
1. In this example, an external user generates an HTTP query to a web server located on the internal network.
2. The router receives this traffic on its external interface. If an inbound ACL is applied on the external interface, the router processes the ACL.
3. Assuming that the ACL permits the packet, the router uses NBAR to classify and mark the packet. This classification is done in the ingress direction of the external interface. In this case, you need an NBAR classification for HTTP traffic. For QoS purposes, you could classify all HTTP traffic into one grouping; however, if this was for security purposes, you might be looking for specific commands, filenames, or other data in the HTML query request to mark it, such as with a worm, a virus, or a Trojan horse attack. When used for security purposes, you would configure NBAR to drop unwanted or dangerous traffic. If the traffic does not match any of the classification rules, it is not marked (it is not dangerous).
4. After NBAR processes the traffic, it is routed to the egress interface. In this example, this is E0. The router then processes any QoS actions on the packet. I use the term QoS loosely here because the Cisco IOS can take many actions when dealing with the packet, such as queuing it up with an appropriate queuing mechanism, shaping it, policing it, and even dropping it. For security purposes, you want to drop the marked traffic and, possibly log the transaction. If the traffic is not marked, it is treated normally. Finally, if there is an egress ACL on the router's interface, this affects what traffic can exit it.
A few important things must be pointed out about NBAR and classification:
- When the Cisco IOS marks the packets' ToS field with the IP Precedence or DSCP value, this remains in the packet as long as the packet is being routed to the destination (unless another router modifies the ToS value).
- For NBAR to process traffic, the traffic must be seen by two interfaces on your router: The ingress interface classifies and marks the traffic, and the egress interface enforces policies concerning the markings.
- You can apply NBAR classification, marking, and policing in more than one direction of the router. For example, in Figure 10-4, you could set up two different policies: one for traffic entering the network (from E1 to E0) and one for traffic leaving the network (E0 to E1), giving you a lot of flexibility in enforcing security policies.
NBAR Advantages vs. Traditional Traffic Analytics Engines:[5]
- Out-of-the-box visibility into more than 1,500 applications running on a network
- More granular layer 7, SD-WAN, and traffic-shaping policies using enhanced application visibility
- Well-established traffic classification engine used by many Cisco products
- Fine-grained traffic analytics and client tracking
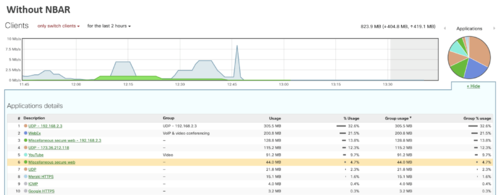
As shown above, categories like “Miscellaneous secure web” and “UDP” traffic flows consist of many applications which aren't classified by the traditional traffic analytics engine.
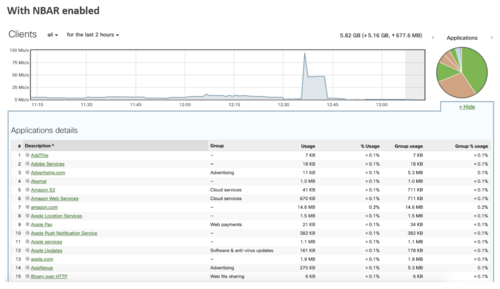
As shown above, NBAR-enabled platforms will classify more applications as opposed to categorizing as “Miscellaneous secure web” and “UDP” traffic. It also allows administrators to enforce more granular L7 firewall and traffic-shaping rules, giving more flexibility into blocking and prioritizing desired applications.
See Also
Network
Network Address Translation (NAT)
Network Architecture
Network Control Program (NCP)
Network Diagram
Network Effect
Network Infrastructure
Network Management
Network Map
Network Mapping
Network Monitoring
Network Motif
Network News Transfer Protocol (NNTP)
Network Operations Center (NOC)
Network Organization
Network Performance Management (NPM)
Network Protocol
Network Security
Network Structure
Network Topology
References
- ↑ Definition - What Does Network Based Application Recognition (NBAR) Mean? Wikipedia
- ↑ What is Network Based Application Recognition (NBAR)? Cisco
- ↑ How Does NBAR Work? Live Action
- ↑ NBAR and Classification eTutorials.Org
- ↑ NBAR Advantages vs. Traditional Traffic Analytics Engines Meraki